Facebook is in the news for a few days after the disclosure of the Cambridge Analytica scandal. A few days ago, another wave of rumours revealed that the Facebook app could collect your private data. Facebook denied and a ping-pong game started. Is it true or false? The fact is that more people started to take care of their data and uninstalled the app from their mobile phone. Hashtags also appeared on Twitter like #leavefacebook…
If you’re curious about what Facebook knows about you, they allow you to download an archive of all (let’s trust them?) data they have about you. Go to your profile settings, general and click “Download a copy of your Facebook data”. You must provide your password and a few minutes later (depending on your activity on Facebook), you’ll get an email with a temporary link to download a nice ZIP archive. It contains a tree of subdirectories. In my case:
./index.htm ./html ./messages ./messages/photos ./photos
The index.htm can be used from your browser to navigate through your data:
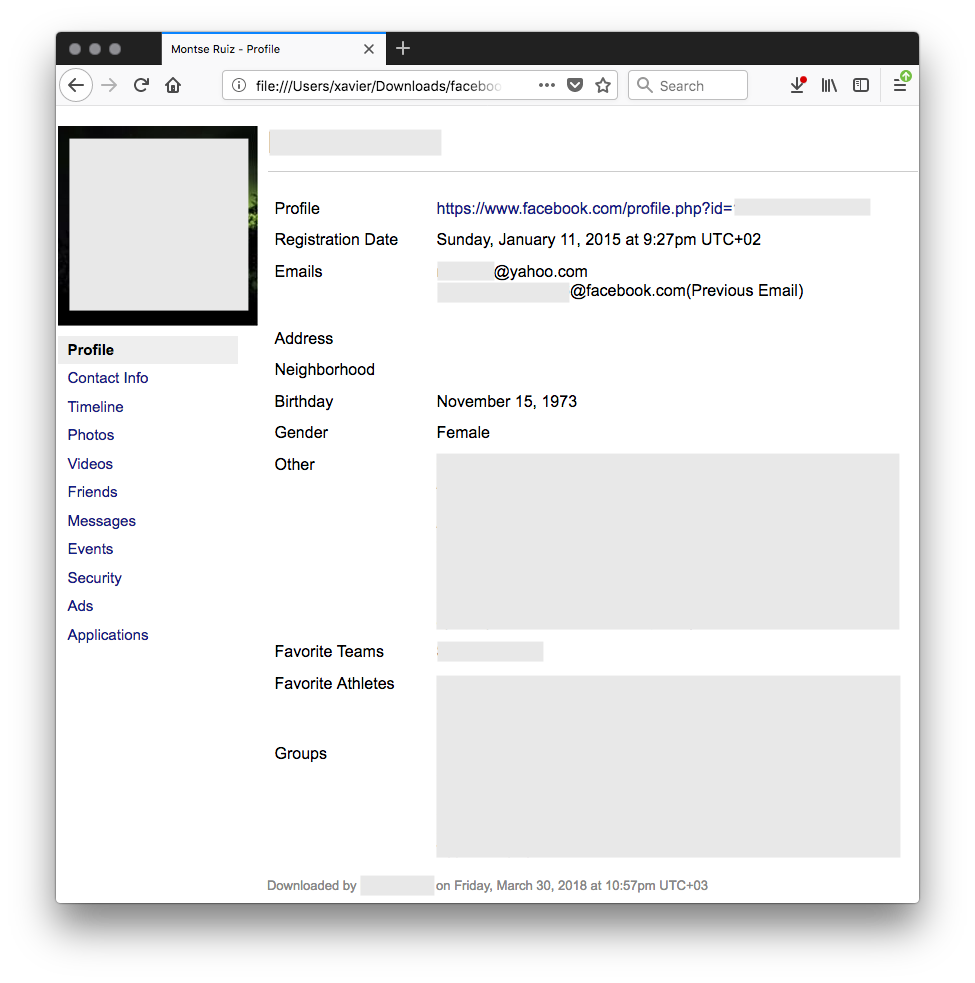 The downloaded archive name has the following format: facebook-<string>.zip. Based on my findings, <string> can be your Facebook username or ID. With interesting content like this, it was tempting to start searching for Facebook users’ history file on the net. What’s the best place to search for files uploaded by users or without their explicit consent? Virustotal of course!
The downloaded archive name has the following format: facebook-<string>.zip. Based on my findings, <string> can be your Facebook username or ID. With interesting content like this, it was tempting to start searching for Facebook users’ history file on the net. What’s the best place to search for files uploaded by users or without their explicit consent? Virustotal of course!
I created a simple YARA hunting rule to search for interesting Facebook archives:
rule FacebookArchive
{
strings:
$s1 = "messages/" nocase wide ascii
$s2 = "photos/" nocase wide ascii
condition:
new_file and any of ($s*) and file_type contains "zip" and file_name contains "facebook-"
}
Guess what? Less than 24 hours later, I already got one hit. At the moment, I collected five archives that contain:
- Profile details
- Timeline of activity
- Photos / Videos
- Friends (when added)
- Messaging conversations
- Events (accepted, declined)
- Account activity (with IP addresses, Browser UA)
- Ads displayed to the users (with the one he/she clicked)
- Applications installed
I contacted Facebook via their bug bounty program to report the issue just to raise the potential issue which is, I agree, not directly related to their services. Users are responsible for the privacy of the data once downloaded. Not surprisingly, their answer was negative:
Hi Xavier,
Thanks for contacting us. Keep in mind that this queue is specifically for security vulnerabilities. Since what you describe doesn’t appear to be a security vulnerability, you can provide feedback or suggestions regarding a feature here:
https://www.facebook.com/help/contact/268228883256323
Thanks,
So, they consider that it’s not a security issue but a feature. My suggestion is:
- To generate a unique filename (example: based on the file SHA256)
- To encrypt the ZIP archive with the current user’s password.
Conclusion (and reminder): do not post sensitive files to VirusTota and, when you’re using tool that relies on VirusTotal, be sure that files will not be sent without your prior consent!

Tx, fixed typo!
Nice article, didn’t think of that!
Small typo: I already got one it. r/it/hit 😉
It would also mean that someone could offline brute force their actual FB password if they got access to the zip.
Emailing or SMSing a random password seems like a much better option!
Right! Good catch! 😉
They could generate a random pw and use an alternate way to provide it to the user (sms?)
If Facebook is handling the passwords properly, they cannot encrypt the zip with the user’s Facebook password, because they only have a hash of it.