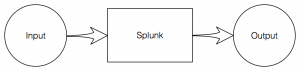
While you use a tool every day, you get more and more knowledge about it but you also have plenty of ideas to improve it. I’m using Splunk on a daily basis within many customers’ environments as well as for personal purposes. When you have a big database of events, it becomes quickly mandatory to deploy techniques to help you to extract juicy information from this huge amount of data. The classic way to do hunting is to submit IOC’s to Splunk (IP addresses, domains, hashes, etc) and to schedule searches or to search it in real time. A classic schema is:
Inputs are logs, OSINT sources or output from 3rd party tools. Outputs are enriched data. A good example is to use the MISP platform. Useful IOC’s are extracted at regular interval via the API and injected into Splunk for later searching and reporting.
# wget --header 'Authorization: xxxxx' \
--no-check-certificate \
-O /tmp/domain.txt \
https://misp/attributes/text/download/domain/false/false/false/false/false/7d
This process has a limit: new IOC’s are not immediately available when exported on a daily basis (or every x hours). When we see new major threats like the Bad Rabbit last week, it is useful to have a way to search for the first IOCs released by security researchers. How to achieve this? You can run manually the export procedure by starting a connection on the Splunk server and executing commands (but people must have access to the console) or … use a custom search command! Splunk has a very nice language to perform queries but, do you know that you can expand it with your own commands? How?
A Splunk custom search command is just a small program written in a language that can be executed in the Splunk environment. My choice was to use Python. There is an SDK available. The principle is simple: input data are processed to generate new output data. The basis of any computer program.
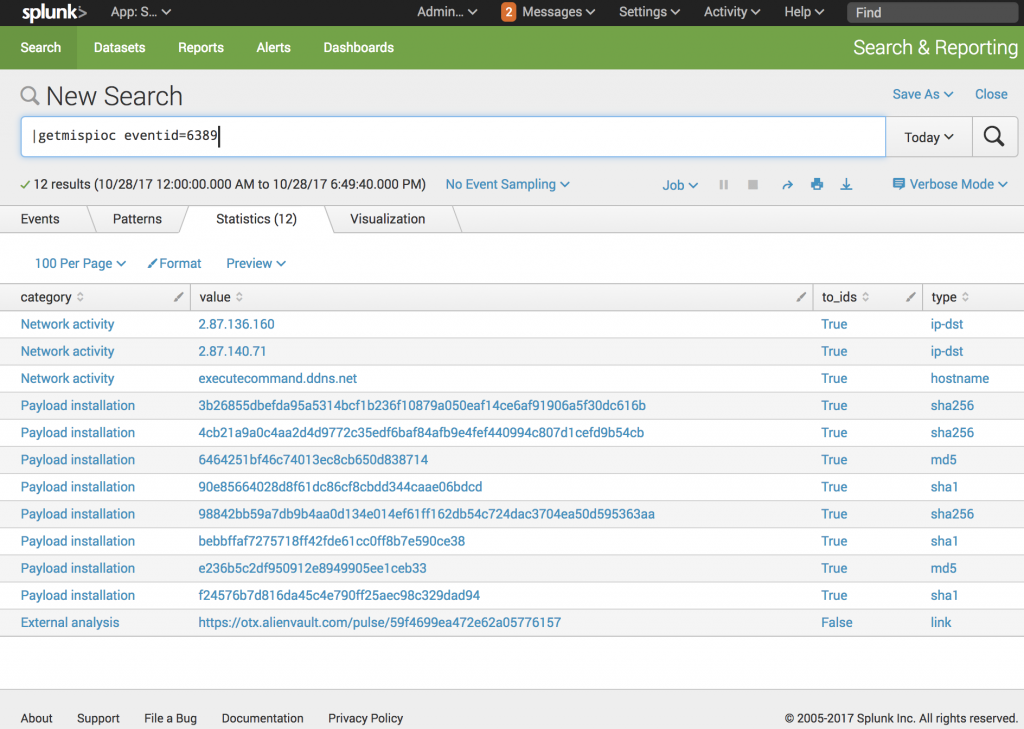
I wrote a custom search command that interacts with MISP to get IOCs. Example:
The command syntax is:
|getmispioc [server=https://host:port]Â
[authkey=misp-authorization-key]
[sslcheck=y|n]
[eventid=id]
[last=interval]
[onlyids=y|n]
[category=string]
[type=string]
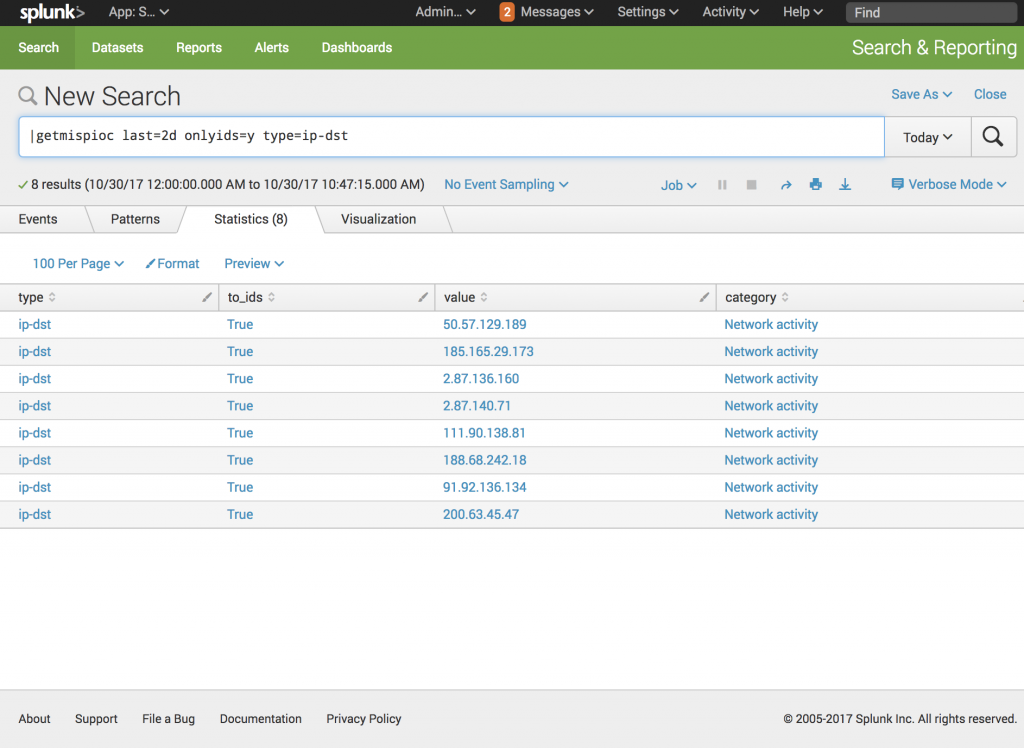
The only mandatory parameters are ‘eventid’ (to return IOCs from a specific event) or ‘last’ (to return IOCs from the last x (hours, days, week, or months). You can filter returned data by filtering on the ‘ids_only’ flag and/or a specific category or type. Example:
|getmispioc last=2d onlyids=y type=ip-dst
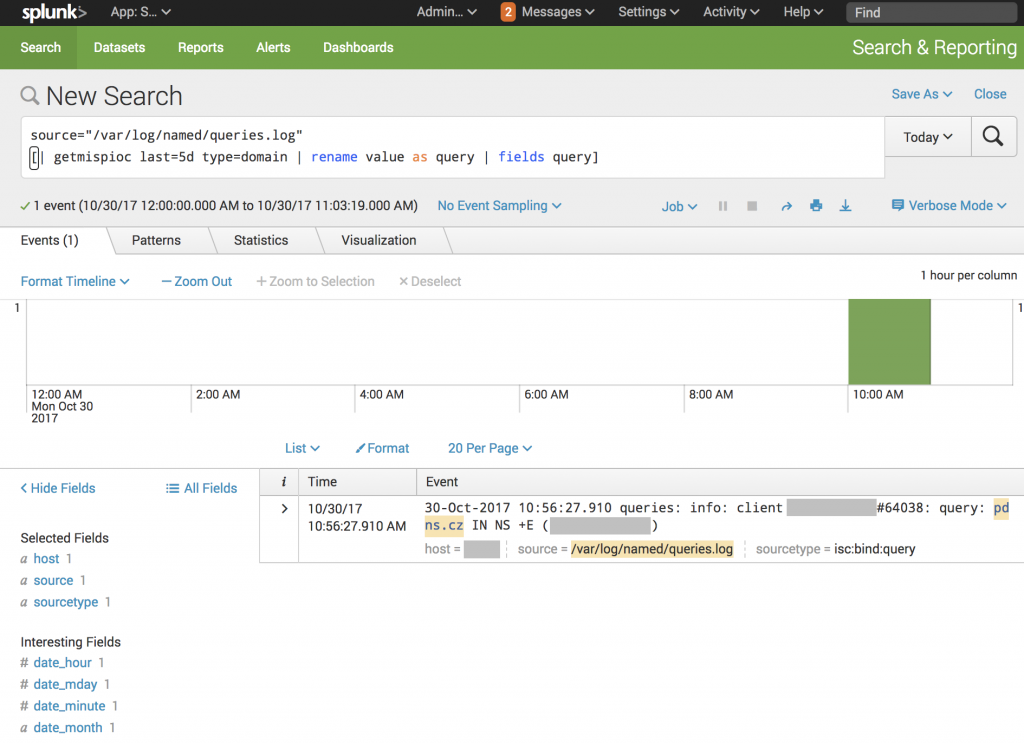
Now, you can integrate the command into more complex queries to search for IOCs across your logs. Here is an example with bind logs to search for interesting domains:
source=/var/log/named/queries.log [|getmispioc last=5d type=domain |rename value as query |fields query ]
The custom command is based on PyMISP. The script and installation details are available on my github account.
I don’t understand your question!? You don’t need an index to run the scripts. It queries the MISP server API. And results are reuised in another query.
Hi
How to create index=misp from the misp42splunk app. I ve created but no events from misp42splunk populate the misp index ???
Hi Ian,
I would recommend you to have a look at a much more mature app (and developed by a Friend): https://github.com/remg427/misp42splunk
Is there a way to get this app to use the decay model in MISP?
Ideally I’d like to pull all IOCs where the decayed value is set to NO
I must python 3 ? Or you have other way ?
thx Xme !