It’s over! The 4th edition of Botconf just finished and I’m in the train back to Belgium writing the daily wrap-up. Yesterday, the reception was organized in a very nice place (the “Chapelle de la Trinitéâ€). Awesome place, awesome food, interesting chats as usual. To allow people to recover smoothly, the day started a little bit later and some doses of caffeine.
The day was kicked off by Alberto Ortega with a presentation called “Nymaim Origins, Revival and Reversing Talesâ€. Nymaim is a malware family discovered in 2013 mainly used to lock computers and drop ransomware. It was known to be highly obfuscated and to use anti-analysis techniques (anti-VM, string description on demand, anti-dumping, DGA, campaign timer). During the analysis of the code, a nice list of artefacts was found to detect virtualized environments (ex: “#*INTEL – 6040000#*†to detect the CPU used by VMware guests). Alberto reviewed the different obfuscation techniques. In the code obfuscation, they found a “craft_call†function to dynamically calculate a return address based on an operation with the two hard-coded parameters. Campaign timer is also classic for Nymaim: There is a date in the code (20/11/2016) which will prevent the malware to execute after this date (the system date must be changed to permit the execution of the malware, which is not easy on a sandbox). Network traffic is encrypted with different layers. The first one is encrypted with RC4 with the static key and a variable salt for each request/response. The DNS resolution is also obfuscated. Domains are resolved using a homemade algorithm. “A†records returned are NOT the actual IP addresses. (Google DNS are used). To know the real IP address, the algorithm must be used. Of course, DGA is used of course. It uses PRNG based on Xorshift algorithm Seeded with the current system time and a fixed seed. Nymaim is used to perform banking fraud. The way this feature is configured is similar to Gozi/IFSB (that will be covered later today). They use redirects to the injects panel. Nice review of the malware with an amazing job to reverse and understand all the features.
Then Jose Miguel Esparza and Frank Ruiz presented “Rough Diamonds in Banking Botnetsâ€. Criminals keep improving their backends : C&C’s and control panels. They made a nice review of the current landscape but this talk was flagged as TLP:RED so no more information.
After a coffee break, we restarted with Maciej Kotowicz who presented “ISFB, Still Live and Kickingâ€. Also named Gozi2/Ursnif, ISFB is a malware which appeared in 2014 and is, still today, one of the most popular bankers on the market. Why this name? “ISFB†string was found in debugging instruction in the code. Targets are numerous (all over the world). The dropper performs persistency, inject worker, setups IPC and (new!) download the 2nd stage. It also has anti-VM tricks. It uses GetCursorInfo() to get the movement of the mouse. No movement, no execution! It also enumerates devices. Then Maciej reviewed deeper how the malware works, its configuration and registry keys. Communications to phone home are based on the Tor network and P2P network and a DGA of course.
The next slot was assigned to Margarita Louca with a non-technical talk: “Challenges for a cross-jurisdictional botnet takedownâ€. Margarita being from Europol, she also asked to consider her presentation as TLP:RED.
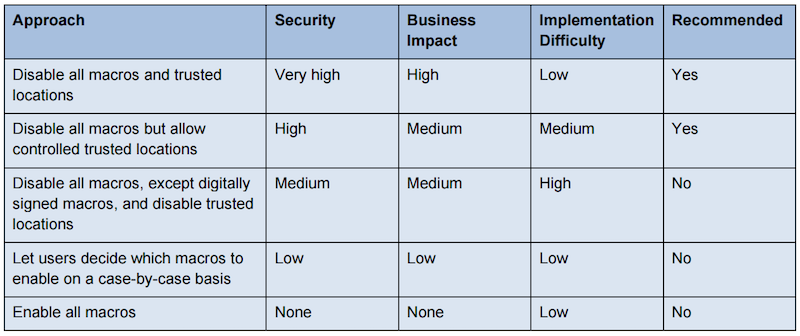
The afternoon started with two last talks. Kurtis Armour presented “Preventing File-Based Botnet Persistence and Growthâ€. The goal of this talk was education of threat landscape and the layers of protection. The most part of his talk focused on post-exploitation (only on classic computers – No IoT). Botnet delivery mechanism is based on social engineering, tricking users to go unsafe source and to gain some money (monetise) or via browsers, 3rd party apps (EK), this was already covered. Dropped code can be file based or memory based. Starting from the fact that code is made to be executed by the computer, Kurtis reviewed how this code can be executed by a Windows computer. The code can be a binary, shell code or a script. This code must be dropped on the victim by a dropper and they are many way to achieve that! Via HTML, JavaScript, ZIP, EXE, DLL, Macros, PowerShell, VBA, VBS, PDF, etc. The talk was mainly defensive and Kurtis explained with several examples how to prevent (or at least reduce the chances) code execution. First golden rule: “No admin rights!“. But we can also use pieces of software to reduce the attack surface. A good example is LAPS from Microsoft. Windows Script Files are a pain. Don’t allow their execution. This can be achieved by replaced the default association (wscript.exe -> notepad.exe). Microsoft Office files are well known to be (ab)used to distribute macros. Starting with Office 2016, more granularity has been introduced via GPO’s. Here is an interesting document about the security of macros published (source)
PowerShell is a nice tool for system administrator but also very dangerous: it runs from memory, download & exec from remote systems. But powershell is harder to block. Execution policies can be implemented but are easy to bypass. Powershell v5 to the rescue? Improved logging and security features (but don’t forget to uninstall previous versions). Application whitelisting to the rescue? (the talk focused on AppLocker because being by default and can be managed via GPO’s). It can be used to perform an inventory of the applications, to protect against unwanted applications and increase software standardisation. Another technique is to restrict access to writable directories like %APPDATA% but they are many others. hta files are nasty and are executed via a specific interpreter (mshta.exe). There are many controls that could be implemented but they are really a pain to deploy. There was an interesting question from somebody in the audience: Who’s using such controls (or at least a few of them). Only five people raised their hand!
And finally, Magal Baz & Gal Meiri closed the event with another talk about Dridex: “Dridex Gone Phishingâ€. After a short introduction about Dridex (or a recap – who don’t know this malware?), they explained in details how the banking fraud is working from the infection to the fraudulent transaction. You have a token from your bank? 2FA? Good but it’s not a problem for Dridex. It infects the browser and places hooks in ouput and input functions of the browser and all data is duplicated (sent to the bank and the attack. This is fully transparent to the user. A good way to protect yourself is to rename your browser executable (ex: “firefox_clean.exe” instead of “firefox.exe”). Why? Dridex has a list of common browsers process names (hashed) and compromize the browser based on this list.
As usual, there was a small closing session with some announcements. A few numbers about the 2016 edition? 325 attendes, 4 workshops, 25 talks (out of 48 proposals). And what about the 2017 edition? It should be organized in Montpellier, another nice French city between 5th and 8th of December.