What do security analysts when they aren’t on fire? They hunt for malicious activity on networks and servers! A few days ago, some suspicious traffic was detected. It was an HTTP GET request to a URL like hxxp://xxxxxx.xx/south/fragment/subdir/… Let’s try to access this site from a sandbox. Too bad, I landed on a login page which looked like a C&C. I tried some classic credentials, searched for the URL or some patterns on Google, in mailing lists and private groups, nothing! Too bad…
Then, you start some stupid tricks like moving to the previous directory in the path (like doing a “cd ..”) again and again to finally… find another (unprotected) page! This page was indexing screenshots sent by the malware from compromised computers. Let’s do a quick ‘wget -m’ to recursively collect the data. I came back a few hours later, pressed ‘F5’ and the number of screenshots increased. The malware was still in the wild. A few hours and some ‘F5’ later, again more screenshots! Unfortunately, the next day, the malicious content was removed from the server. Hopefully, I got copies of the screenshots. Just based on them, it is possible to get interesting info about the attack / malware:
- People from many countries were infected (speaking Chinese, Russian, German, Arab, …)
- It targeted mainly organizations
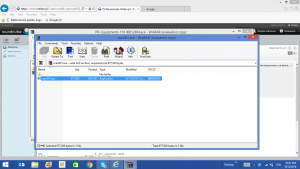
- The malware was delivered via two files:
- A “scan001.ace” archive containing a “scan001.exe” malicious PE file.
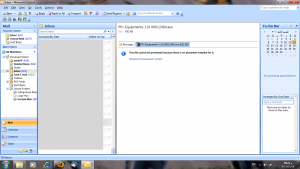
- A “PR~Equipments-110 00012404.ace” file
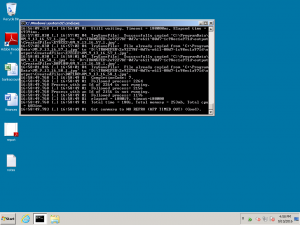
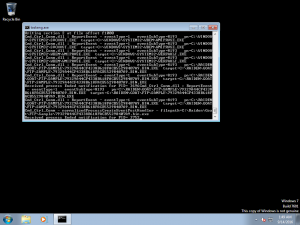
- The malicious file was opened on file servers and even a DC!
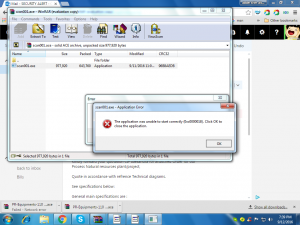
- The malicious file was analyzed in sandboxes (easy to recognize them, Cuckoo & FireEye)
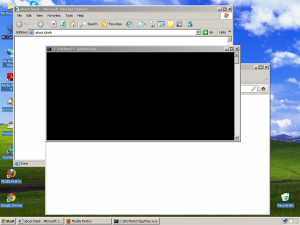
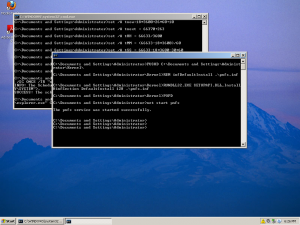
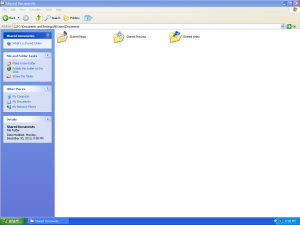
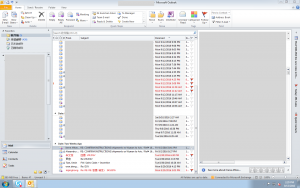
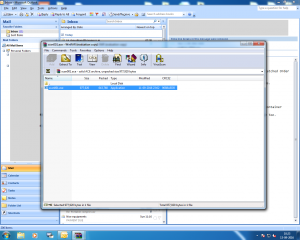
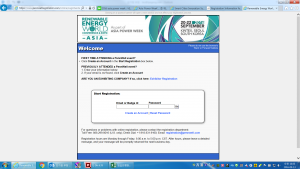
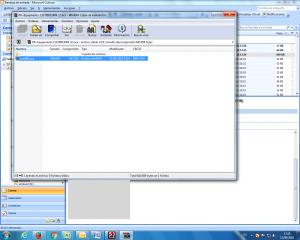
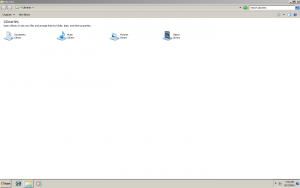
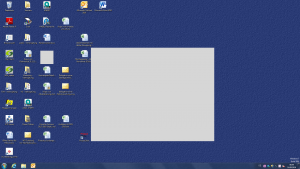
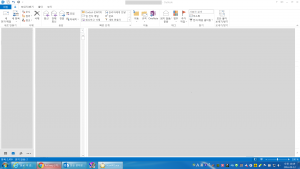
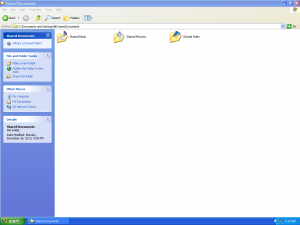
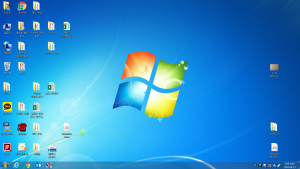
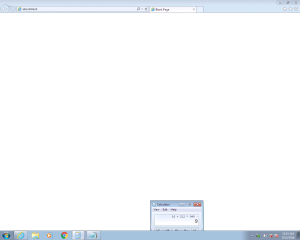
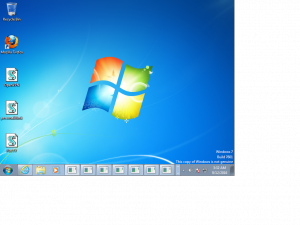
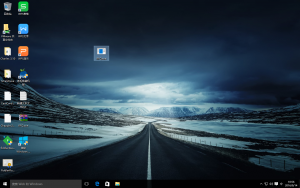
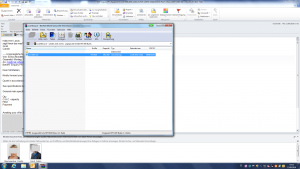
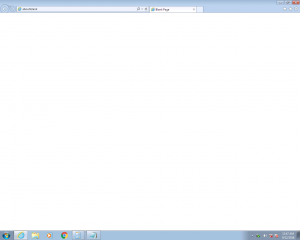
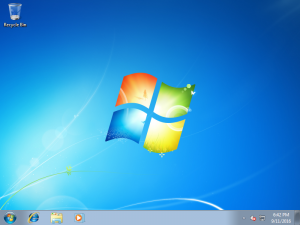
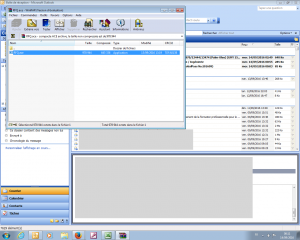
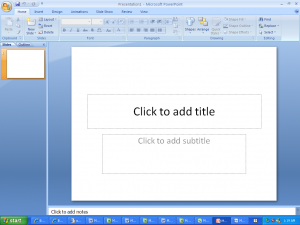
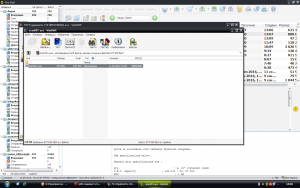
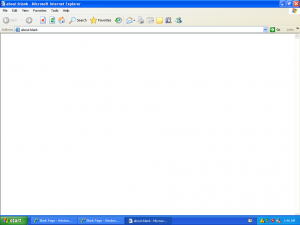
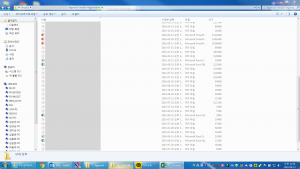
Here is a selection of interesting screenshots (anonymized). The original screenshots were named “<hostname>_<month>_<day>_<hour>_<min>_<sec>.jpg”. Based on the filename format, it seems that the malware is taking one screenshot per minute. I renamed all the files with their MD5 hash to prevent disclosure of sensitive info.



RT @xme: [/dev/random] Go Hunt for Malicious Activity! https://t.co/gs3XnAPEu8
Cool thing! It reminds me a bit vncroulette ruling the world a couple of months ago (yep, I know that one used totally different approach with shodan etc..). Some advice on URL for that particular? Besides – greetings from behind the same office SOC desk!
@xme Marrant 🙂 Je me demande ce que cet exercice donnerait “chez moi” (université de Namur)… Faudra retester !
RT @xme: [/dev/random] Go Hunt for Malicious Activity! https://t.co/gs3XnAPEu8