 On a daily basis, I’m looking for malicious emails. I own catch-all mailboxes that collect a huge amount of spam that I’m using to perform deeper analysis: to discover new tactics used by attackers and new piece of malicious code. Basically, they are two categories of phishing campaigns: the one sent to a large base of potential victims and the one targeting only one victim (one person or one company). The first one has a very low ROI (“Return On Investment“) while the second one can be much more lucrative! Those are usually well prepared and can be very difficult to detect by regular users. On the other hand, common campaigns are easy to detect: they contain typo errors, they remain vague in their context and details. The content does not match the language or style used by the spoofed issuer. But, sometimes, it goes in the other way…
On a daily basis, I’m looking for malicious emails. I own catch-all mailboxes that collect a huge amount of spam that I’m using to perform deeper analysis: to discover new tactics used by attackers and new piece of malicious code. Basically, they are two categories of phishing campaigns: the one sent to a large base of potential victims and the one targeting only one victim (one person or one company). The first one has a very low ROI (“Return On Investment“) while the second one can be much more lucrative! Those are usually well prepared and can be very difficult to detect by regular users. On the other hand, common campaigns are easy to detect: they contain typo errors, they remain vague in their context and details. The content does not match the language or style used by the spoofed issuer. But, sometimes, it goes in the other way…
Today I received an e-mail from a well-known Belgian company. I contacted them during the weekend to request an invoice for the service (travel) that I ordered previously. I filled an online form, submitted my details. The feedback was “Thank you, we will send you more information via email.“.
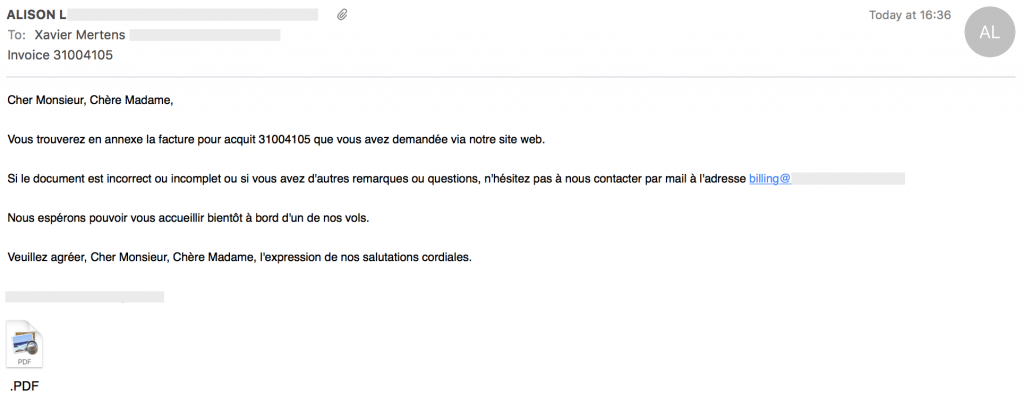
Here is a copy of the received email:
For my non-French speaking readers, here is a quick translation:
Dear Sir, dear Madam,
Please find attached the invoice 31004105 you requested via our website.
If the document is incomplete or incorrect, or if you have other comments or questions, feel free to contact us by mail at xxx.
We hope to welcoming you on board one of our flights.
Kind Regards,
My first reaction was “Warning – Phishing ahead!” for the following reasons:
- The mail was sent in plain text
- The subject was a classic one for phishing attemps
- The sender name written in uppercase
- The attached document name was “.PDF.pdf” (wtf?)
- The message looked similar to many phishing attempts
Fortunately, the mail was an original. The mail path was correct (checked via the SMTP headers), the attached PDF file was clean and contained references to the company (note: this can be also forged in a real phishing attack). According to LinkedIn, the sender was working for the company (this can also be forged with a fake profile).
While many companies are trying to improve their communication channels with their customers to protect them against phishing emails, how can we still receive such kind of emails in 2016? I would expect:
- A properly formatted email with the look and feel of the company
- More references to my order (name, dates, …)
- Complete contact information about the sender (at least a phone number)
- Avoid attachment like the plague! More and more mail gateways implement strong filters that could put valid emails in quarantine (prefer a unique URL which points to the document).
With companies sending such emails, I’m not surprised that people still fall in the phishing trap! Just my $0.02…
RT @xme: [/dev/random] How to Not Send Corporate Emails? https://t.co/K7ma5lygiz
True… Maybe I was not clear enough: I’d prefer a link to download the file (and keep my local copy) than to have multiple attachments.
I agree with most of your points. Except that there is nothing as annoying as HTML-only email and I really appreciate suppliers who send me simple plain text email. I also like having the attached invoice. That way it’ll be safe and backed up at least on one system. If I need it again in five years’ time (or even next week, given how fast the “web” moves – for better or for worse), their link is guaranteed to be broken.
RT @xme: [/dev/random] How to Not Send Corporate Emails? https://t.co/K7ma5lygiz
RT @xme: [/dev/random] How to Not Send Corporate Emails? https://t.co/K7ma5lygiz
RT @xme: [/dev/random] How to Not Send Corporate Emails? https://t.co/K7ma5lygiz