 A few days ago, I attended an event organized by the Chamber of Commerce in Belgium (ICC Belgium) and the Federation of Enterprises (FEB) to announce with great ceremony the release of the first Belgian Cyber Security Guide. Honestly, this is a great initiative! In the audience, many many infosec professionals were present but not many “business owners“. That’s not a surprise… Ok, I’ll mitigate, it’s also part of our daily job to promote security to C-levels. Even if the message is still not yet received by the target audience, that’s the goal of a “security awareness” process which can be resumed as:
A few days ago, I attended an event organized by the Chamber of Commerce in Belgium (ICC Belgium) and the Federation of Enterprises (FEB) to announce with great ceremony the release of the first Belgian Cyber Security Guide. Honestly, this is a great initiative! In the audience, many many infosec professionals were present but not many “business owners“. That’s not a surprise… Ok, I’ll mitigate, it’s also part of our daily job to promote security to C-levels. Even if the message is still not yet received by the target audience, that’s the goal of a “security awareness” process which can be resumed as:
while(true) {Â repaeat_message(); }.
An endless loop…
The document content is quite good and resume lot of useful information that everybody should follow, even you, your family and friends. To briefly resume, the document is based on a top-ten “must do” security actions:
- Action 1: Implement user education & awareness
- Action 2: keep systems up to date
- Action 3: Protect information
- Action 4: Apply mobile device security
- Action 5: Only give access to information on a “need to know†basis
- Action 6: Enforce safe surfing rules
- Action 7: Use strong passwords and keep them safe
- Action 8: Make and check backup copies of business data and information
- Action 9: Apply a layered approach against viruses and other malware
- Action 10: Prevent, detect and act
My advice is download it, read it and promote it!
But the guide is not complete and could be extended. The actions listed above focus on the end-user and his device(s) – pc/laptop/mobile devices. Â In my humble opinion, the guide is lacking some advices regarding our networks and infrastructures. Recently, while surfing here and there, I landed on a MySQL database server publicly available. For infosec professionals, our first reaction is always: “WTF, why is this server facing the wild Internet?“. A few months ago, I scanned for recursive DNS servers in Belgium. To build this first report, I compiled a huge list of Belgian IP addresses. I reused my list of subnets and did the same exercise now with MySQL servers. I scanned the huge pool of IP addresses against the port TCP/3306. What are my findings?
- 10.263.320 IP addresses scanned
- 2.325 IP addresses were running a MySQL server (read: successfully generated a 3-way handshake and replied with the MySQL protocol)
- 0,02% of the IP space was running MySQL
- Only 829 MySQL servers prohibited the connection (“xxx is not allowed to connect to this MySQL server“).
- A lot of IP addresses reported were dynamically assigned (ADSL, etc)
What about the detected versions? The top-ten is:
| MySQL Version |
Count |
| 5.1.49 |
257 |
| 5.1.49-3 |
132 |
| 5.1.66 |
114 |
| 5.0.27 |
104 |
| 5.0.51a-24+lenny5 |
104 |
| 5.1.66-0+squeeze1 |
96 |
| 5.0.51a-24+lenny4 |
90 |
| 5.1.63-0+squeeze1 |
90 |
| 4.1.20 |
67 |
| 5.1.61 |
66 |
Based on all MySQL servers found, here is the repartition:
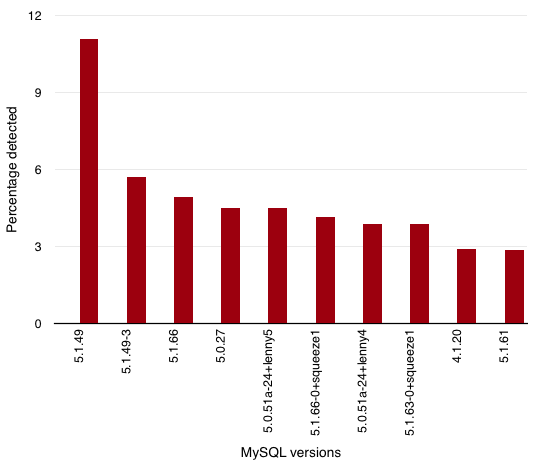
Just for the information, the oldest server found is still running a MySQLÂ 3.23.41-nt. Just have a look at the vulnerabilities discovered for this release. I don’t see why a database server (whatever the type/brand is) must be facing the wild Internet.
Conclusion: I would like to see more advices added to the Belgian Cyber Security Guide about network design and infrastructure. And if this topic looks too deep, just add a suggestion to request the help of professionals to design your network infrastructure. My goal is not to be alarmist but even if you follow up carefully the advices listed in the current document, you are still vulnerable if your resources are directly exposed to the wild! My $0.02…
RT @xme: [/dev/random] Why the Belgian Cyber Security Guide Must Be Extended? Example with MySQL! http://t.co/93izsY1STK
RT @xme: [/dev/random] Why the Belgian Cyber Security Guide Must Be Extended? Example with MySQL! http://t.co/93izsY1STK
It is just in this type of organization that some advice re effectiveness of AV could be useful. E.g. do not spend money on AV, but get the “best” free AV as e.g. recommended by AV-comparatives.org. Works as well as non-free at a portion of the cost.
EMET on the endpoints of PME/KMO where the user is (even less?) security-aware might actually have a higher effect than in a larger company. This would be valuable advice from/for a “Belgian guide”. Especially considering the names “behind” it (incl. Microsoft, E&Y, …).
For me, this guide targets definitively the “PME/KMO’s”. Talking about “EMET” or effectiveness of AV solutions is way too deep! Such organizations just want aproduct that protect them. Helas, it does not exist!
Why I wrote this blog post? Today, event small companies can have an infrastruture with many devices like NAS, webcam, … that are often deployed without any security concern!
RT @xme: [/dev/random] Why the Belgian Cyber Security Guide Must Be Extended? Example with MySQL! http://t.co/93izsY1STK
Re your remarks on the doc, I don’t think it is such a “new” instrument. It does raise good points -the known best practices- but leaves many questions unanswered. Take for instance “Prevent, detect, act”. Simply because of BE privacy laws, a lot of traffic is not being intercepted – e.g. SSL traffic to banks and other domains. One ends up with a lot of encrypted, unknown streams out of the network. Ideal for malware to hide in. No mention on how to address this in the guide. Defense-in-depth/layered approach: is it still working, in a world where endpoints are so vulnerable? I’m not saying it is a bad guide; just isn’t ground breaking. One could follow all advice and still be compromised.
Of course, for organizations which are not at that maturity level yet, it is a good instrument. But for those who are nearing or at that maturity level, a lot of abstraction of practical challenges is made, with little to no guidance re cost / return on investment and net positive effects of implementing certain measures. Or how to even implement them in a correct fashion.
You raise good points re architecture, but the issues run deeper than that I’m afraid. I see nothing on the effectiveness of AV solutions, nothing on “newer” protections such as EMET etc.
RT @xme: [/dev/random] Why the Belgian Cyber Security Guide Must Be Extended? Example with MySQL! http://t.co/93izsY1STK