 BruCON 0x05 is already over! What an exciting week! After months of preparation, the event went very smoothly without big issues. Here is my quick wrap-up. This time, it’s not a wrap-up about the talks. I don’t have time to follow them, keeping an eye on the network all the time during the conference. As I like to say: “A network is like milk on a stove, you need to keep an eye on it all the time“. How was the fifth edition? We don’t change a winning team! So, we based our network on the same great team of volunteers (Guys, many many thank you for your help, especially @SenseiZeon) and  the same mix of hardware / software solutions. Compared to the 4th edition, the network was easy to deploy, we already knew the venue.
BruCON 0x05 is already over! What an exciting week! After months of preparation, the event went very smoothly without big issues. Here is my quick wrap-up. This time, it’s not a wrap-up about the talks. I don’t have time to follow them, keeping an eye on the network all the time during the conference. As I like to say: “A network is like milk on a stove, you need to keep an eye on it all the time“. How was the fifth edition? We don’t change a winning team! So, we based our network on the same great team of volunteers (Guys, many many thank you for your help, especially @SenseiZeon) and  the same mix of hardware / software solutions. Compared to the 4th edition, the network was easy to deploy, we already knew the venue.
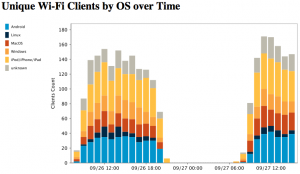
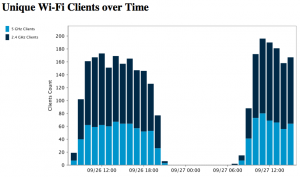
Let’s give some statistics about our beloved visitors. We had much more visibility on the Wi-Fi network this year. We were able to extract interesting stuff:
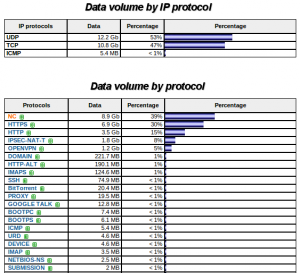
Our bandwidth was a pipe of 100 Mbits. We got some peaks up to 70 MBits/seconds. Even if HTTP(S) remains the most used protocol (HTTP isn’t the new TCP after all? ;-)), we also saw a big increase in VPN technologies (Mostly OpenVPN & IPSEC). That’s why we generated more UDP traffic then TCP!
In the table above, the protocol called “NC” means “Non Classified“. It represents all the traffic using ports that were not present in the default configuration (based on IANA’s list). Malware analysis is a hot topic today, a workshop about Cuckoo was organized and we also received a nice appliance to perform live malware tracking (a FireEye WebMPS). We detected only two events over the two days (honestly, I expected more). The first one was really a false positive. Somebody downloaded a malicious .rar file but from a known website to share files. It was maybe somebody doing a test. The second one was more suspicious. It was a callback to a C&C (the malware was well know – Bot.IRC.Sdbot):
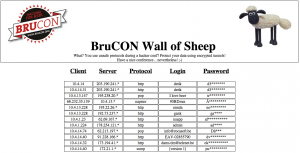
Of course, the Wall of Sheep was alive and tracked careless visitors. People are using VPN’s but we still see cow-boys using corporate laptops (It’s easy to be detected based on the box name presented to the DHCP server) and clear-text protocols.
During the conference, many people asked us questions about the network setup (“How do you see or monitor this?“, ” Which tool do you use to do this?“, etc). So, in last minute (during the BruCON party in fact), we (@SenseiZeon & myself) decided to give a small lightning talk about our baby. The slides are available on SlideShare:
What’s next now? We collected all the traffic generated by attendees in two big pcap files (~60 GB each day). The goal will be to extract even more statistics from them. Then, they will be deleted of course. We only keep the session headers for legal purposes.
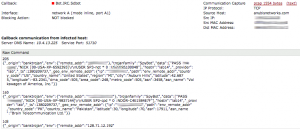
Yep, only two which were false positives! Sad, I expected much more but on the other side, the BruCON attendees were not a good sample of users…
Only two alerts from FireEye, WTF? It woud be very interesting to see how many alerts you would get if you run the PCAPs trough Bro IDS (but also Snort/Sourcefire)!
RT @xme: [/dev/random] #BruCON 0x05 Wrap Up http://t.co/hdxLDOAHE8
RT @xme: [/dev/random] #BruCON 0x05 Wrap Up http://t.co/hdxLDOAHE8
The Bot.IRC.Sdbot was not a real infection either. Check last slide on http://files.brucon.org/2013/Apresentacao%20Brucon.pptx and check video for that talk you will understand this was a couple of tests we were running. Am suprised you didn’t catch the rest 🙂 Also if you check on your image source host belongs to anubisnetworks, the people presenting that talk (us) work for anubisnetworks 😀
@xme Should put the PCAPs up here: http://t.co/EmJPCyIayK 🙂
@xme @SenseiZeon but please replace Shaun next time for he’s known to be the smartest sheep ever
#brucon
RT @xme: [/dev/random] #BruCON 0x05 Wrap Up http://t.co/hdxLDOAHE8
RT @xme: [/dev/random] #BruCON 0x05 Wrap Up http://t.co/hdxLDOAHE8
RT @xme: [/dev/random] #BruCON 0x05 Wrap Up http://t.co/hdxLDOAHE8
RT @xme: [/dev/random] #BruCON 0x05 Wrap Up http://t.co/hdxLDOAHE8
RT @xme: [/dev/random] #BruCON 0x05 Wrap Up http://t.co/hdxLDOAHE8
RT @xme: [/dev/random] #BruCON 0x05 Wrap Up http://t.co/hdxLDOAHE8
RT @xme: [/dev/random] #BruCON 0x05 Wrap Up http://t.co/hdxLDOAHE8