 I don’t know if you already noticed but it looks to be a never-ending story: Companies got pwned and data leaked on the
I don’t know if you already noticed but it looks to be a never-ending story: Companies got pwned and data leaked on the Internet pastebin.com. Then starts the game of press releases…
Most companies try to reduce the impact of the breach they suffered and it looks like Holliwood movies with animals involved in stunt scenes: Â “No Animals Were Harmed in the Making of This Film“.
Let’s take a practical example which occured recently in Belgium. Rex Mundi is a group of people (Note: I don’t say “hackers“) who like my country! Not for our beers or the french fries (and even I’m not sure) but they like our websites:
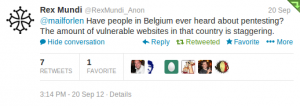
Previously they already targeted some companies like buyway.be, habeas.be. Their latest target is the Internet provider Numericable. They claimed to grab 6000 customer records:
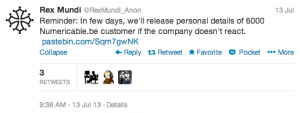
Their method is always the same: They grab interesting data (usually customer information), publish a sample and ask for some ransom by threatening to disclose the full set of stolen data. I don’t know if companies paid, I hope not! The goal of this post is not to debate about those stories which remain illegal. But, as I said above, companies tend always to reduce the impact of such attacks. Again with Numericable which communicated that the stolen data were not “critical“. They didn’t contain billing information but only names, e-mail addresses and phone numbers of visitors who requested information via a website.
I’m sorry but ALL data are VALUABLE! There will always be people ready to get them. Two scenarios:
- Use the data to perform statistics or try to attract new  customers (think about a competitor – another ISP)
- Use the data to perform attacks (spear-phishing) – “Dear x, you contact Numericable recently blah blah blah…“
This behavior is a side effect of the business: Companies must keep customer confidence and prefer to try to minimize the impacts of such attacks. So, nobody was harmed in this attack? I’m not sure…
Another scenario : use so-called “non critical” information such as email, name, birth date to try and guess other credentials for this user… Don’t underestimate the weakness *and* “re-use” of credentials across several websites !