 A few
A few days weeks ago, I wrote a blog post (link) about a (unsuccessful) WordPress bruteforce attack agains this site. I captured the attackers’ traffic in a big pcap file. It was a good opportunity to perform a quick analysis to try to extract some statistics. Here follow more details about the attackers. I extracted the offending IP addresses (15K+) and fired a big Nmap against them. I agree this was a rude approach and, in some countries, port scanning is prohibited. No complaint was received and I detected only one “back” scan from one of the targets. [Note: during the scan, no kid, no animal was injured and no attempt to abuse resources was performed]
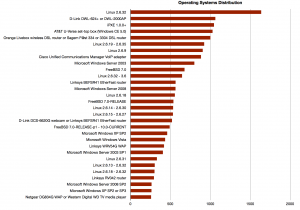
The first scan took a lot of time (but I was not in a hurry) because I used the “-O” switch to enable the OS detection. Here is a first table based on the scan results: The operation systems distribution. Not a big surprise, a lot of different Linux distributions! But Windows Microsoft Server 2003 in a nice 9th position. Later in the list, there are lot of broadband routers from multiple vendors.
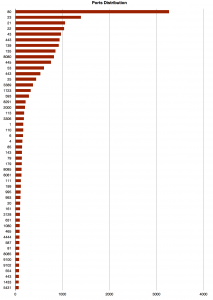
After the operating systems detection, it’s normal to have a look at the available ports. The following graph represents the top-50 of  ports (with the Nmap states “open” or “filtered“). No surprise, HTTP is the winner.
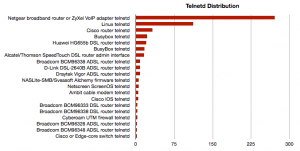
The other top protocols prove that lot of IP addresses were broadband routers. Then, I scanned again but only interesting ports and executed Nmap scripts against them (-sC). Let’s focus on the open Telnet(TCP/23) port. In this case. It’s scarying to see so many telnetd open in the wild also Linux boxes or Cisco devices! Below in the list, I also found some NASes and… one AS/400!?
What about the HTTP servers? There was plenty of them but some interesting:
- Lot of webcams (Avtech, Panasonic, …)
- VMWare ESXi Server
- Fortigate firewalls
- Cisco SPA112 VoIP Adapter
- Checkpoints firewalls
- Cisco IOS
- SoftPerfect Bandwidth Manager (WTF?)
- Siemens Simatic HMI Miniweb
- Sonicwall firewalls
- Bluecoat proxies
- Juniper firewalls
- Asterisk
By seeing the huge number of “commercial” solutions, it means that lot of IP addresses were used in companies. Another tempting port to probe is… 445! Here again, plenty of interesting information:
Host script results: | smb-os-discovery: Windows XP | LAN Manager: Windows 2000 LAN Manager | Name: CARWASH\SECURITY |_ System time: 2013-07-05 13:51:56 UTC+3 | nbstat: NetBIOS name: SECURITY, NetBIOS user: <unknown>, NetBIOS MAC: xx:xx:xx:xx:xx:xx | Name: SECURITY<00> Flags: <unique><active> | Name: CARWASH<00> Flags: <group><active> | Name: SECURITY<20> Flags: <unique><active> | Name: CARWASH<1e> Flags: <group><active> | Name: CARWASH<1d> Flags: <unique><active> |_ Name: \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
In total, 227 hosts offered SMB services directly on the Internet. Personally, I liked the “SECURITY” in the output above.
Finally, is this scan relevant or not? I don’t think so. It was performed a few days after the attack (which runned also during a few days) and, seeing the high number or broadband connections, their IP address was renewed for a while. I scanned hosts which were not involved in the attack. The list of open ports is too wide to be reported here… Remote access, facilities (printers, UPS), file transfers, email (POP3, IMAP (!)) … Finally, here is an idea of the topology:
Hoppefully not in the top list but:
# grep -i bsd os-unique.tmp
FreeBSD 5.3 or 5.5 (x86)
FreeBSD 6.1-RELEASE
FreeBSD 6.1-STABLE
FreeBSD 6.2-RELEASE
FreeBSD 6.3-RELEASE
FreeBSD 7.0
FreeBSD 7.0-BETA2 (custom compiled)
FreeBSD 7.0-BETA4 – 7.0
FreeBSD 7.0-CURRENT
FreeBSD 7.0-RC1
FreeBSD 7.0-RELEASE
FreeBSD 7.0-RELEASE – 9.0-RELEASE
FreeBSD 7.0-RELEASE-p1 – 10.0-CURRENT
FreeBSD 7.0-RELEASE-p2 – 7.1-PRERELEASE
FreeBSD 7.0-STABLE
FreeBSD 7.1-PRERELEASE 7.2-STABLE
FreeBSD 7.1-RELEASE
FreeBSD 7.1-RELEASE – 9.0-CURRENT
FreeBSD 7.2-RELEASE
FreeBSD 8.0-RC1-p1
FreeBSD 8.0-RELEASE
FreeBSD 8.1-RELEASE
FreeBSD 8.2
FreeBSD 8.2-RELEASE
FreeBSD 8.2-STABLE
FreeBSD 9.0-RELEASE
FreeBSD 9.1-PRERELEASE
NAS4Free (FreeBSD 9.1)
OpenBSD 3.6 (x86)
OpenBSD 4.0
OpenBSD 4.3
OpenBSD 4.4
IMHO those are BSD boxes used as firewalls/routers to protect LANs which have compromized hosts.
Hi Xavier,
Very fine job, hopefully I didn’t see any OpenBSD in the list 😉
And btw, you’re right, scanning is prohibited (as you mention) in your south neighbor (I mean country) 🙂
Cheers.
RT @xme: [/dev/random] Post-Analysis of My WordPress Bruteforce Attack http://t.co/DCRNc7fBCi