
My clock tower is completed! I left home yesterday at 6AM to Disneyland Ressort Paris and I’m just back at 6AM. It’s too late to go to bed so I finished to write my Nuit du Hack wrap-up. This was the first time I attended this event. During the last years, I always attended Hack in Paris which is organised at the same place the week before. The Nuit du Hack is first of all the biggest CTF contest organised in France. For this edition, more than 1300 people attended the event. It’s an impressive organisation! But before the CTF, talks are also organised during the day. Here is my quick review of them.
The keynote was presented by Jérémie Zimmermann:  “Freedom or control?“. Jérémie is the co-founder of La Quadrature du Net and fights for online privacy and freedom. The keynote started later due to issues with the public transports and was limited in time. Jérémie started with one question: “Who’s still using Facebook or Gmail?“. Of course, most of the audience is! It’s difficult to get rid of services that we use on a daily basis. Everybody agrees on the fact that those services are monitored (You know: PRISM,NSA, etc) but we need solid evidences (not only provided by hackers and geeks) to prove that we are monitored. A few years ago, computers were our best friend. It was easy to understand how they worked from A to Z. It’s not the case anymore and computers became our enemies! When you are in front of a technological choice, it’s important to verify the infrastructure, think about free softwares and end-to-end encryption. Conclusion to the keynote: we need to educate users. They must realise that everything they typed on Gmail can be re-used to track or score them.
The first talk was “Thinking outside the box” by Dave Kennedy, the founder of TrustedSec. Dave is well-known to be also the developer of SET (“Social Engineering Toolkit“). SET is a wonderful tool that you must use if you are doing pen tests. New versions are regularly distributed with updates, bug fixes but also new attacks. Dave’s talk was based on scenarios. The first one was about a health care company. The first phase is to learn about the target and think about what you want. He provided a good example of spear-phishing  (think about all the details – headers, body, signature, links). To be successful the mail must:
- Fear the people (you won’t receive money, we will cancel your account)
- Ask for a quick action (it will require only 2 mins of your time)
- Feel secure (use HTTPS)
- Discovery
- Reconnaissance
- Exploitation (46% of successful attacks upload a web shell) and this shell is visited in 3h30 after the exploit.
This was an interesting research.
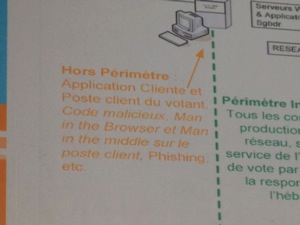
The next talk was presented by Sébastien Andrivet who spoke about the e-voting system used in Genève/Switzerland for a few years. In Switzeland, citizens have three ways to vote: via a polling station, snail mail or via Internet (still experimental). When Sébastien used the system for the first time, I was curious to learn how it is working and how to be sure that votes are correctly handled. Official servers are not always online (only during polling periods) and could not be attacked, so he decided to build his own voting system based on the public one. A huge project! But he succeeded and found interesting stuff:
- Developer’s names were present in the code
- Some comments in Java class files were “inappropriate” for a software developed by a government
- Why does the system allow the citizen to modify his vote?
This was my preferred presentation today! Great job!
The next talk: “Cracking and analysing Apple iCloud protocols: iCloud backups, Find My iPhone, document storage” by Vladimir Katalov. Vladimir explained how iCloud works and was are the protocols/requests used to put/get files. Simply interesting. Just remember that iCloud backups can’t be fine tuned. Apple has the key and can access your data!
The two next talks were presented during the lunch time and were more funny or based on demos. First, how journalism and social engineering can be mixed. Yes, journalists also use SE techniques to put people in confidence. They have to check their language, keep an eye on the body language. In fact, SE is used every time you need to get some info from somebody (journalists, vendors, politicians, etc). Nothing new… Then a very nice live lock picking demo was organised. Always funny!
Then came Rosario Valotta to speak about “Abusing browser use interfaces for fun & profit“. Malware number is increasing and attacks are mainly originated by user initiated downloads. Users have requirements (more security) and vendors try to provide responses. Let’s focus on Chrome: Browser security notifications are a crucial part of the browser trust model. Notify the user before making important choices. Notifications need to be recognisable and trusted. How? There are two modes used by browsers:
- Modal: Popup window: accept/deny/ok/yes/now – Workflow blocking / visual contrast / default answer?
- Modeless notifications: file download, plugging activated, HTML5 apis, etc (work flow is not stopped) (more informative)
# iptables -A INPUT -j NFQUEUE --queue-num 0
The first demo was a perl script reading the queue and processing the packets (also the payload). Then, he faked SSH source by applying packet alteration. It’s also possible to fake a traceoute, you just need cool ideas! Finally, he explained how Nmap performed OS fingerprinting and explaint how to generate answers with correct data to fake an OS.
And we continue with Thibaut Scherrer who talked about CCTV cameras deployed by authorities. They are presented by politicians as the key weapon to prevent crime. Is it true? After a presentation of the different models of cameras used in France (wires/wireless, fixed, pan, tilt, zoom, etc), he gave some pro & con and more interesting how to abuse them to prevent a recording. Some techniques are a wifi jammer or a laser. Thibaut explained also the algorithm developed with other students to detect which camera must be blocked to safely cross from a point A to a point B in Paris. They are open maps with all the information required. Thibaut explained how to protect himself from being recorded with some infrared lights placed on a helmet!

Jayson Street came on stage to talk about email attacks to abuse of companies. Â What’s new with email attacks? Nothing new and it still works. Today, 91% of attacks involved spear phishing!

Jayson came on stage with new stories to abuse people with emails. What’s new with email attacks? It still work but nothing new. 91% of attacks involved spear phishing! Jason explained how to perform a good phishing attack. A good introduction email must contain:
- Danger
- Intrigue
- Politics
- Reward
After explaining how to write a good email with real contact, correct information etc. He explained the new type of attack he used to enter a company. Why bypass your firewall if I can bypass your receptionist? Jayson’s idea was to use Gmail emails but displayed on a tablet and show this to the receptionist… Lot of funny examples!
Next, Florent Batard & Nicolas Oberli presented “Modern frameworks, modern vulnerabilities”. Based on several demos, they showed how to exploit modern frameworks used to build web applications. Example with the “known secret” attack against a Python framework. Those framework are good in protecting themselves against attack but the weakest list is often the developer who by mistake disclose the secret key in public websites like github or pastebin or do not change the default secret key implemented in the source code. If you know this key, you can perform lot of nice attacks like privilege escalation or code execution. The demo displayed a classic file (/etc/passwd) but also started a remote shell using netcat. But generating cookies manually is a pain. The speaker developed a tool called pppp.py that will help you to generated cookies for multiple frameworks. A must have if you are doing pen tests. The tool will be release soon, check out balda.ch.
The last talk was about e-banking application: “Practical exploitation of rounding vulnerabilities in internet banking applications” by Adrian Furtuna. According to some tweets, it wasn’t a brand new topic but it was the first time that I learned this type of exploitation. In this case, no XSS, CRSF or funny attacks but some kind of abuse of how banks process our payments. Think about this: when you buy stuff for 1.99 EUR, do you pay the exact cent? How much sellers win from rounding? Based on this question, does the same works with banks? Usually, amounts are specified with two decimals. Here are two examples:
- Transfer of 8.3436 EUR, the bank will transfer 8.34 EUR and wins 0,0036 EUR
- Transfer of 8.3578 EUR, the bank will transfer 8.35 EUR and looses 0.0022 EUR


RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
Hi xavier! Thank you very much for your post about this event and I’m glad to read that you enjoyed it.
About the Workshop yes, we had a meeting about this point and will probably push them on another room next year, but doing it, we lost the advantage of the main scene of the room.
I would like to apology myself in the name of the organizers about the excesses that some of our attendees caused on the Tris’s workshop and surely condamn this kind of behavior!
Kind regards,
ArKam
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
@xme merci 🙂
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
Thanks for posting this great summary! 🙂 RT “@xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/F67ROfhDZpâ€
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
@xme thank you a lot.
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
RT @xme: [/dev/random] La Nuit du Hack 2013 Wrap-Up http://t.co/kOKpeV06rJ
@xme merci pour le résumé et bonne nuit quand même 😉