 Connecting a server to the Intertubes is like connecting it to the wild. There are plenty of bots (thousands? millions?) scanning IP addresses for vulnerable services. Once a service is enabled on an IP address, you don’t have to wait a long time before detecting incoming traffic! One of the most common ports is HTTP (80). There are plenty of outdated or unpatched applications still running in the wild and CMS (“Content Management Systems“) are one of the favourite targets for bots. This blog is running WordPress. Why hide it if it can be guessed in a few seconds. WordPress is a well-known CMS with plenty of third-party plugins and also a lot of security holes. It is a nice target for bots. Regularly, my blog is visited by bots and it’s part of the game… Usually, I don’t care about them, they are just temporary blacklisted.
Connecting a server to the Intertubes is like connecting it to the wild. There are plenty of bots (thousands? millions?) scanning IP addresses for vulnerable services. Once a service is enabled on an IP address, you don’t have to wait a long time before detecting incoming traffic! One of the most common ports is HTTP (80). There are plenty of outdated or unpatched applications still running in the wild and CMS (“Content Management Systems“) are one of the favourite targets for bots. This blog is running WordPress. Why hide it if it can be guessed in a few seconds. WordPress is a well-known CMS with plenty of third-party plugins and also a lot of security holes. It is a nice target for bots. Regularly, my blog is visited by bots and it’s part of the game… Usually, I don’t care about them, they are just temporary blacklisted.
But, a few days ago, another attack drew my attention. It has the following interesting characteristics:
- Coming from a bot (or proxies) from multiple countries/ISP’s
- Using multiple valid User-Agent strings
- Generating traffic at a low rate to avoid my anti-bruteforce filter
It was a dictionary attack against the ‘admin’ user. After a first wave of login attempts, something interesting happened: every password was probed twice; A first time agains the “admin” account and a second time against a private account. This proves that I was facing my first targeted attack! Instead of loosing my time trying to blacklist the IP addresses, I let the attacker play and sniffed the traffic until the attack stopped by itself. A brief analyze of the PCAP file revealed:
As shown on the timeline below, there was two first peak of requests then, the attack was lighter but stable with a constant number of probes:

When you have IP addresses, it’s easy and very convenient to perform a GeoIP lookup and display them on a map:
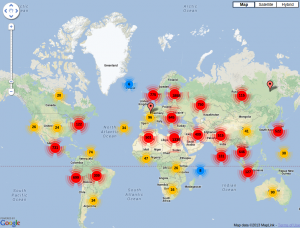
Geolocation is interesting but where are they coming from (from an ISP or company perspective). Here is the top-30 of TLD (based on the reserve lookup of offensive IP addresses):
| TLD | # |
| ukrtel.net | 852 |
| com.tr | 794 |
| com.mx | 483 |
| telecom.kz | 473 |
| net.ua | 440 |
| ne.jp | 316 |
| triolan.net | 234 |
| kyivstar.net | 217 |
| mgts.by | 189 |
| com.ua | 180 |
| net.br | 143 |
| net.co | 130 |
| com.br | 127 |
| volia.net | 126 |
| odessa.ua | 101 |
| co.th | 76 |
| kiev.ua | 75 |
| rima-tde.net | 72 |
| vega-ua.net | 70 |
| net.mx | 70 |
| mclaut.net | 68 |
| net.pe | 67 |
| telecomitalia.it | 64 |
| breezein.net | 64 |
| wanadoo.frt | 62 |
| totbb.net | 62 |
| bbtec.net | 56 |
| pldt.net | 51 |
| hinet.net | 51 |
| poltava.ua | 50 |
Finally, was it a targeted attack or not? I don’t think so… Why? When you plan to conduct a targeted attack, the primary phase (“reconnaissance“) is a key to understand the behavior (amongst technical details) of your future target. In my case, the attacker should see that my blog requires dual-factor authentication! Why run a bruteforce attack against a login page without providing an OTP (“One Time Password“)? This is completely useless. I think that bots become more intelligent and extract now user names from the link to editors in posts:
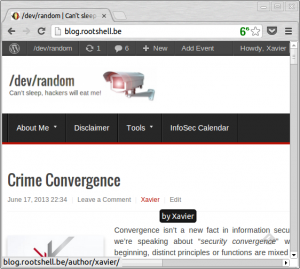
Take care with your blog users and roles (subscriber, administrator, editor, contributer, etc)! Like any regular user, apply the least privileges principle and… keep an eye on your logs!
Hello, Xavier,
Nice post, I guess you are right speaking of bots becoming more intelligents because I found the same pattern on a SSH honeypot (it used the same IP than the web site).
Cheers,
Jean-Philippe.
I’m probably barking up the wrong tree, but you can enable 2-factor authentication to make these attacks an order of magnitude more difficult. I use “Google Authenticator” (http://henrik.schack.dk/google-authenticator-for-wordpress/) which, contrary to the name, works perfectly without Google.
RT @xme: [/dev/random] Proud of My First Targeted Attack… or Not! http://t.co/N77I0ye0JK