
The 2012 edition of hack.lu is already over for a few minutes. Here is my wrap-up posted just before driving back to $HOME! Yesterday, we had a nice dinner with Belgian friends. This is some kind of tradition during the conference, meet friends and exchange ideas, positions around a table with good food. This morning, everybody looked tired and the coffee was welcome!
The schedule of the third day was interesting. It started with Paul Rascagneres and Hugo Caron who presented their baby: malware.lu.

The purpose is to provide malware samples to researchers and companies. Finding good malware samples was not easy, until they started their own project! Registration is free and wait for their approval (there is no automatic registration – they reserve the right to not accept you!). At the moment, they have +4 millions samples (7TB of data!), 25 published articles and 1000 users. The malware database is searchable by hash or name. They try to use the same names at the ones defined in antivirus applications but it’s not always easy (different vendors use different name)s. The second part of the project is to provide malware analysis. They gave an overview of a real case: the analyse of the HerpesNet botnet. From reversing the malware to owning the C&C and finally the bot owner himself They found not only his nick but real name. This was an open door to his real life: Facebook, Picassa, Skype, Email addresses, Twitter and… a picture of his girlfriend! Finally, the tool “malwasm” was presented. This is a free tool which helps you to analyse malware samples. It is based on Cuckoo. All activities are stored in a Postgress database. Once done, the security analyst can browse the data via a nice web interface. The killer feature of this GUI is the time bar which allows you to browse trough the malware activity via a time line! You may compare the generated output like a real debugger. To conclude, Paul performed a complete demo of all the features. Brilliant! The tool is available here.
Then Andres Blando & Matias Eissler talked about “One firmware to monitor them all” (in fact, only Matias was present). The subject looked fuzzy: it was about the modification of the Broadcom Wifi cards firmware. To add monitor mode and frame injection. I presume that I don’t need to explain why those features can be sometimes useful! This topic was already widely covered for a few years (reverse engineering of the firmware, exploitation, etc) but mainly on PC architectures. What about the mobile devices today? It could be very funny to use monitor mode on our mobile devices. They focused the research on BCM4325 & BCM 4329 chipsets which are present in many phones. The firmware is present on the device filesystem (Example on Android in /system/etc/wifi/). It is of course closed source but… not signed! The first challenge was: how to play with the binary chunk? How to detect the architecture? Broadcom cards are using ARM CPUs. Based on this info and manual tests, disassembling can start as well as the identification of primitive functions and more precisely the 802.11 ones.
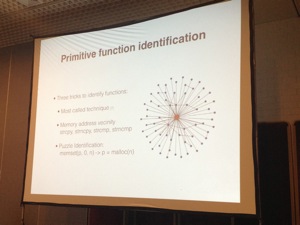
The firmware verifies itself. Modifications must be implemented with a replacement of the existing one. The next challenge was to obtain the monitor mode: Getting the 802.11 & PHY headers as well as all the traffic (management control & data). Live demo of monitor mode via an Android tablet:
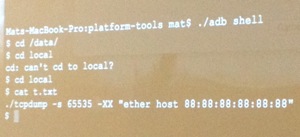
The next step was of course injection! Because we want to inject! After detailed explanations, the next demo was injection of packets via a Python script running on an iPad. Oh! A new access point:Â
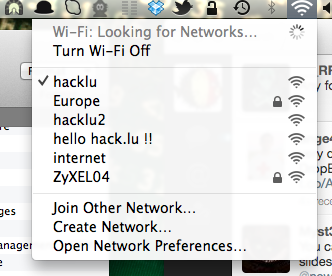
Very good job and presentation! The conclusion was already known but reminders are always useful: Never truss WiFi networks!
All security conference must have at least a talk about iOS! It remains a hot topic. This time, Mathieu Renard (from Sogeti) presented “Hacking iOS applications – Is your company data safe when stored on iDevices?“. IOS devices have multiple attack vectors. One of them is AFC (“Apple File Connection“). A daemon is running on all devices and is used by iTunes to exchange files. Did you already saw docking stations available in hotel rooms or shops to charge your device? Are you sure they don’t contain a hardware backdoor?

Files can be dumped without any activity shown on the mobile screen! Do you have backups of your iDevices? Good! But very interesting data can be find in them! Are they properly stored? Example: the iOS keychain contains crypto keys, credentials. Some data are less protected like Wifi keys. Network traffic can also be an attack vector. A remote virtual interface is created when connecting a device over USB and traffic mirrored. The HTTPS traffic can be intercepted like any other website. Use your favourite proxy (like BurpSuite). If you need a full access to the system, jailbreaking is the only good solution. You’ll got full root access on the device. Once done, you have access to all applications. The next step is of course reversing them. Mathieu explained deeply how are working iOS executable. MobileSubstrate is an application which allow developers to hook functions! Funny demo: stealing crypto keys by hooking the CCCrypt() API! Another interesting hook: Bypassing detection of jailbroken devices! (Your $$$ MDM solution will not report it as bad 😉
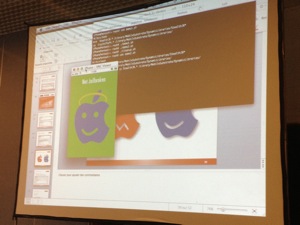
And the browser? It is secure? All the cookies are leaked in the logs! And logs are readable by all applications. Fail. Another demo was authentication bypass again by using another hook. Which defensive measures can be used? (only to slow down the analysis) Use anti debug or anti hooking techniques. Try to obfuscate your application (dynamic string generation?). Conclusion: Minimise the use of Objective-C for critical functions! A great talk with nice demos!
Philippe Langlois (P1 Security) came to talk about SS7: “Remotely crashing HLR or why it took telecom industry 20 years to recognise the problems with SS7?“. Philippe is always trying to work with niche products that are not always considered as interesting for security researches. This is the case of SS7. Example: In July 2012, the O2 network fully restored after a 24-hour blackout. What is a HLR? IT’s a huge database with all customers, phones, etc. No HLRÂ (“Home Location Register“), no network services! Big mobile providers were affected by HLR crashes (O2, Orange) and it was not due to an attack! Most often it was a new equipment or a new feature deployed in the network or protocol incompatibilities. A HLR relies on big IT infrastructures (with clusters, SANs, high-end servers) running in full load-balancing mode. But the problem: they never imagine that one of the cluster members can be bad guy. Those infrastructure are very complex and run obscure software. Even logging is a pain, how can you interpret this:
Philippe explained how malformed SCCP traffic can be a big issue. There exists lot of fuzzing tools for regular protocols but who will invest in a fuzzing tool for a protocol used by a niche market? It’s possible to crash a HLR just by adding random data ti a SCCP packet. Vendors of telecom products seems to live on another planet:

If you enable debugging mode, the HLR crashes even more (100GB of process to dump to disk). DoS using 6 packets / minutes! What were the root causes of technical crashes?
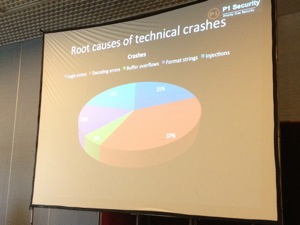
Mobile operators try to keep crashes and outage away from the public to protect their image (common behaviour). Vendors deny the root causes of the crashes. It’s a fake security feeling (crashes only, no tracing, no proof). Â HLR has a big attack surface: Legacy protocols, billing interfaces, reporting interfaces, data warehousing, etc). The telco world is a niche and I don’t have any experience with it but Philippe’s presentation proved that like any IT infrastructure, security could be improved. Only a few operators are current on security and vendors are lagging, even preventing security.
After the lunch, a second set of lightning talk sessions was organised. One of the interesting talks was the one of @r00tbsd about the Belgian eID: “When malwares targeted the Belgian eID“. This card is used by Belgian citizens to sign & authenticate documents (amongst other services). The malware used the smart card API provided by Windows to access the card. Its concept: share the USB device with the C&C! The PoC uses a driver to make USB over TCP/IP. To get the PIN, just use a key logger. Demo: Let’s sign a Word document. And, via Meterpreter, the attacker is able to read the PIN code in a lock.  The presentation is available here. Another interesting lightning talk: the one of Didier Stevens (blog) about shell code injected in Excel. Did you already tested his task manager in Excel? FURL is the “Fast URL Parser Library” and was  presented by Sébastien Tricaud.
Back to the regular talks. Morgan Marquis & Cory Altheide presented “Post-Introsion Problems: Pivot, Persist and Property“. Their idea is a framework for thinking about post-intrusion and response to targeted attacks. They are two models: playing the role of police or firefighters. Which one to choose? Neither, use counter-intelligence. State of the art:
- Level 1: Most responders focus on vulnerabilities and exploits.
- Level 2: TTP – “Tools, Techniques & Procedures“. Note that tools are easy to modify or abandon.
The “kill chain” is an interesting concept: Trying to detect as soon as possible, before the real attack.
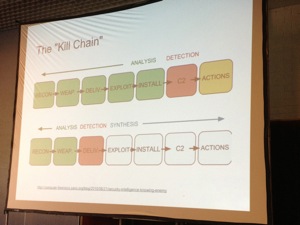
The speaker’s approach is to focus on things the attacker must do, not things they happen to do! This works only with motivated attackers! Focus on your adversary goal, what do we have to do to achieve that goal and check what they generally do in an operation. Pivoting, enumeration (mapping the hosts, identification of users/privileges and mapping the data). Interesting artifacts while pivoting: process/sockets, shell history, event logs or user profile directories. Others are RDP/SSH, registry keys or memory-only artefacts (IP, FQDN, command buffers). Network artefacts are: DC/Kerberos/LDAP/DNS logs, internal net flows. About persistence? We have trojaned binaries, userland backdoors, hiding in plain sight, MBR, VBR and kernel root kits. Maintaining access? Even detecting poor persistence techniques is done poorly. Of douse, one of the most important step is the data exfiltration. Many techniques exist (SMTP, UUCP, FTP, SCP, Base64, serial line logging, tunnelling, etc. Don’t forget cloud services! (Dropbox, Google Drive, etc). Maybe the keyword to conclude this talk was “Aggressive Defense”. Guys, you spoke too quickly! It was not easy to follow you and take notes at the same time.
Like iOS, mobile devices and networks are always the subject of nice researches like the one of Sébastien Dudek and Guillaume Delugre: “MobiDeke: Fuzzing the GSM protocol stack“. They started with some good reminders about classic GSM networks (2G). Modern smartphones use two CPUs: one for the applications and one for the basedand. Many attacks have already been published against mobile phones. In the case presented today, the baseband was the target. Why? Setup a baseband is easy (OpenBTS is your friend). Typical scenario: the attacker runs the rogue base station, the victim’s mobile connects to it. The problem is that the baseband software is closed source. How to find  bugs? Classic methods remain the same: reverse-engineering or fuzzing. MobiDeke is framework that use fuzzing to create crafter L3 messages sent over the air. Once the fuzzing successful, how to monitor crashes? One of the solutions is to check if the baseband still respond to ‘AT’ commands. Sébastien explained the methodology in details (honestly, I did not follow everything) and showed a video demo. MobiDeke is still in development and the source code is not released at the moment.
Then we did some forensics with Guy Martin who presented “Real-time network forensics using pom-ng“. Why? How to capture a lot of network traffic and finally, what do you with this huge amount of data?

Guy had the classic reaction: If you don’t find a tool to do the job, write it by yourself! This tool is “packet-o-matic“. Initialy, it was very easy and parsed common protocols. Most problems were: single threaded, packet mangling, rule based. So came the “Next Generation” (argh, I definitively hate this expression) with new features:
- No more complex rules
- No more packet mangling
- Abstraction layer between parsing/processing and outputs
- Multi-threaded
- Multi-input
Guy explained how his tool works. Based on raw packets, it can generate event, payload or packet output. Guy made a nice demo, sniffing the HTTP traffic to Google and displayed the requests live (with funny requests sent from the audience):
The configuration is performed using a command line interface. Example:
pom> input parameter set wlan0 interface mon0 pom> output add http_search pom> input start wlan0 pom> config show
More fun, a LUA API is available to add your own plugins. Another demo was the extraction of images from HTTP flows based on such LUA script. Some example scripts were reviewed by Guy. The future of pom-ng will bring more features like more protocols, EXIF data parsing(!), improved LUA API, offline DNS resolver, counters and gauges. It’s a very nice (another one) tool for your forensics toolbox!
And, last but not least, Adrien Kunysz presented “BOFH meets SystemTap“. SystemTap is basically a debugger or tracing tool.

After a short introduction of the tool, Adrien started directly demos. First one, intercepting IRC conversations (performed via lib purple) using three lines of code:
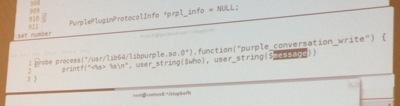
Other examples:
- Eye-dropping a pseudo terminal
- Preventing deletion of files
- A keylogger(!)
All the examples used during the talk are available online. Nice presentation with lot of demos to close the schedule!
So we are done with this 2012 edition! Thanks to the organisers, the speakers and all those who talked/exchanged interesting, funny, scary ideas with me! Next week, I’ll attend #days and try to write some wrap-ups too!
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #3 http://t.co/GtTSywJE #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #3 http://t.co/GtTSywJE #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #3 http://t.co/GtTSywJE #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #3 http://t.co/GtTSywJE #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #3 http://t.co/GtTSywJE #hacklu
RT @xme: [/dev/random] Hack.lu 2012 Wrap-Up Day #3 http://t.co/GtTSywJE #hacklu