 The new version (0.4) of Cuckoo, the open source  malware analysis system has been released this week. That’s a great news! The list of changes and new features is very impressive. So big that an upgrade is not recommended. In my case, I just installed a brand new Cuckoo instance. It was much easier and save me some nightmares. I still need to upgrade the instance running on my Macbook pro, I hope it will run also very smoothly. Some of the most significant changes are:
The new version (0.4) of Cuckoo, the open source  malware analysis system has been released this week. That’s a great news! The list of changes and new features is very impressive. So big that an upgrade is not recommended. In my case, I just installed a brand new Cuckoo instance. It was much easier and save me some nightmares. I still need to upgrade the instance running on my Macbook pro, I hope it will run also very smoothly. Some of the most significant changes are:
- Brand new  base code
- Support for KVM
- Support for YARA & VirusTotal
- New post-analysis modules
- Behavioral signatures
The last feature is really what I was expecting for my CuckooMX project! It is now very simple to detect malware behavior just by creating some Python classes. You are free to perform any tasks in the classes: send emails, write in databases, communicate with other processes, … In my case, It will now help me to handle properly the quarantine with suspicious emails.
How does it work? Here is a first example. Malwares make extensive usage of domain names to communicate with C&C or to download software components. Some malwares have a list of hundreds domains they use randomly. It could be very interesting to detect if a program tried to communicate with one of those domains. Cuckoo already analyzes the DNS requests performed. We just have to check if the resolve FQDN are considered as suspicious. The good news: We can find on the Internet free lists of domains or IP addresses which are known as malicious. Such domains list is available on malwaredomains.com.
The following Python class is called by Cuckoo during the reporting phase. It loops through the DNS request captured during the analyze and try to match a malicious domain. If it’s the case, it reports a event of severity level “3” (between 1 – low and 3 – high).
import fileinput
from lib.cuckoo.common.abstracts import Signature
# Load the list of malicious domains
domains = []
for domain in fileinput.input(['/data/cuckoo/conf/malicious-domains.txt']):
domains.append(domain.rstrip())
class ResolveMaliciousDomain(Signature):
name = "resolve_malicious_domain"
description = "Try to resolve a malicious domain name"
severity = 3
category = ["generic"]
authors = ["Xavier Mertens <xavier(at)rootshell(dot)be>"]
def run(self, results):
for fqdn in results["network"]["dns"]:
for d in domains:
if fqdn["hostname"].find(d) >= 0:
return True
return False
Copy this code in your “$CUCKOO_HOME/modules/signatures directory” and restart the Cuckoo main process. To generate the “malicious-domains.txt” file, just use a crontab:
wget -o /dev/null -O - http://mirror1.malwaredomains.com/files/domains.txt | \
awk -F '\t' '{ print $3 }' >/data/cuckoo/conf/malicious-domains.txt
Give some food to Cuckoo and if you are lucky, you will see a result like this:
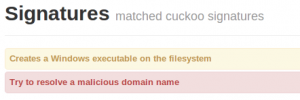
Today, a discussion started on the Cuckoo mailing list about signatures. Now that custom signatures can be quickly added to Cuckoo, isn’t time to start building a community and creating a central repository for signatures? I’m sure that malware analysts have plenty of suspicious behaviors to monitor. Some examples out of my bag:
- Creation of an executable file in a user document folder
- Files creation or modification
- Starting a process from a user home folder
- Spawning new processes
- Deleting itself
- Slowing down using mutliple sleep()
- Testing the presence of a debugger
- Code injection into another process
- Registering a file as auto-start
- Modifying registries or system configuration to enable auto start capability
- Modifying Windows registries
- Changing the proxy settings in Internet explorer
- Modifying the network connection settings for Internet explorer
- Using POST methods in HTTP
- Visiting an unregistered domain
- Downloading executable files with an incorrect file extension
- Using very short HTTP headers
- HTTP requests with non-standard User-Agent
- Performing a failed HTTP connection
- Visiting a malicious domain (done ;-))
- Visiting a Fast flux domain
- Visiting a recently registered domain
- Changing the security settings of Internet Explorer
- Visiting a known dynamic DNS domain
- Connecting to unusual TCP/UDP ports
- Connecting to a malicious IP address
- Using a heap spray attack
- Accessing Internet Explorer cookies
- Communicating over the loopback interface
- Listing the running processes
- Trying a network outbound connection
Personally, I’m ready to invest some time to help building this! I’m dreaming of a huge community like the one active with Nmap scripts! Comments? Idea?
Hi Xavier,
I dont understand this step: “Copy this code in your “$CUCKOO_HOME/modules/signatures directory— So, are you mean that we just need to add this code in to a file named by myself (ex: detect_domain.py) and then put detect_domain.py in to: $CUCKOO_HOME/modules/signatures ?
Hello Scott,
if im not mistake, check your virtualbox.conf file.
try edit at label = XP where “XP” is your virtualbox label name.
this name refer at Virtualbox -> Settings -> General -> Basic -> Name
Hope it helps.
Hello Scott,
No idea, did you follow the installation steps carefully?
Check out the Cuckoo mailinglist for some help…
First off, nice article. Thanks.
I am struggling with the following error when launching cuckoo; any ideas or where I may get assistance?
Thanks
2012-08-04 16:17:41,553 [lib.cuckoo.core.scheduler] INFO: Using “virtualbox” machine manager
2012-08-04 16:17:41,708 [root] CRITICAL: CuckooMachineError: VBoxManage error listing installed machines: