 “Home sweet home!“, its time to wrap-up the second day of Hack in Paris before taking some sleep hours. The second day started with Winn Schwartau from securityexperts.com. His talk was called “Measuring people and technology security“. We have technology everywhere today but warfare started a long time ago with the “Trojan horse” (the real one, the one of the Greek who used it to enter the city of Troy). The difference with today’s attacks: From months, it takes now milliseconds. A simple question to ask yourself: “Do you know what’s happening on your network now?“. Another big change: we moved from an uni-directional communication system (think about the dump terminal connected to a mainframe) to a fully bi-directional system. How can be measure if we are properly protected? Winn made a presentation of the OODA loop (Observer, Orient, Divide, Act). Good quote from him:Â “The first rule of security: kill all the users“.
“Home sweet home!“, its time to wrap-up the second day of Hack in Paris before taking some sleep hours. The second day started with Winn Schwartau from securityexperts.com. His talk was called “Measuring people and technology security“. We have technology everywhere today but warfare started a long time ago with the “Trojan horse” (the real one, the one of the Greek who used it to enter the city of Troy). The difference with today’s attacks: From months, it takes now milliseconds. A simple question to ask yourself: “Do you know what’s happening on your network now?“. Another big change: we moved from an uni-directional communication system (think about the dump terminal connected to a mainframe) to a fully bi-directional system. How can be measure if we are properly protected? Winn made a presentation of the OODA loop (Observer, Orient, Divide, Act). Good quote from him:Â “The first rule of security: kill all the users“.

Security started to grow up during the cold-war. The basic concept was: Let’s build a high wall around our computers (this is called the “Fortress mentality“). But you can fly above walls or break them!. Early security models took this approach (read: keep everybody out). This is a model from 1970 which remains static & expensive. What’s the reference monitor? Each system request is mediated (“yes/no” decisions). Lessons learned:Â We are not smart enough to build a 100% secure computer system. In the physical security (ex: your home protection) we have this equation:
Protection = Detection + Reaction
How to apply it to information security? We call this TBS (“Time Based Security“).
- Protection (ex: a bank vault) : P(t)
- Detection (ex: sensors & alarms) : D(t)
- Reaction (ex: cops) : Â R(t)
And: P(t) > D(t) + R(t)
We can’t rely on our protections. Networks are growing, admins make errors, so many things may occur. Test your own stuff! One big question is how do you notify? Do you alert on screen, send a SMS, send a mail, etc. Â Attackers won’t wait the business hours to attack you! (No 9AM-5PM in this business) Evaluate your exposure (E). If you don’t have a protection:
(if P=0): E = D+R
That was a good reminder to implement security controls. The content can be categorized as “boring” by some but it was delivered in a relaxed atmosphere (good speaker)!
Georgia Weidman (owner of bulbsecurity.com) came in second place with a presentation about “Bypassing the Android Permission Model“. Georgia’s introduction was: “Who has a smartphone? Throw them now!”. The questions covered were: Is the permission model working on the Android platform? Are users making good decisions? As a first example, Georgia reviewed the permissions granted to the Facebook application (the #1 app on Android): Access contact details, access to sms, access Internet, access to location, access to accounts, access to the storage. Even if no malicious action is performed by the Facebook app, why does it have so many permissions? Why not apply the least-privilege principle?

I like Georgia’s quote: “Dear vendors, we want more security in smartphones to continue to call them smart!” Then Goergia explained with demos how applications abuse permissions. The first one was sending blind SMS blind (in the real life – to a high-rate number). No root exploit was used, just asking permissions to read contacts and send SMS. About rooting (or jail breaking) your devices, it can sometimes be very useful (example: to use the teetering feature to avoid Wi-Fi costs in hotels). The malware DroidDream was also reviewed by Georgia. This malicious code is packaged inside of legitimate applications posted to the Android Market in order to trick users into downloading it. More information available here. The next topic was your data protection. Android may use a SD card as external storage. But they are formatted in VFAT (read: no access control). She provided other demos to prove how easy it is to steal data stored on a card and extrude them via SMS. How to mitigate this? Do not use SD cards and do not make them world readable. Even storage in the source code is not safe. There exist tools to reverse engineer the Android apps. Finally, the Android open interface was reviewed. You probably use it daily. You take a picture and send it via Twitter. Data are exchanged between different applications. Georgia demonstrated again how to abuse of the SMS feature of an application from another one which don’t. The best way to mitigate this risk is to ask user interaction (confirmation). Very interesting talk and given by a woman! What else?
After an expected coffee break, Mario Heiderich presented his research under the title “Got your nose! How to steal your precious data without using scripts“. XSS has been a huge topic for a while and plenty of researches have been done. But Mario’s idea was to not use scripting at all? Why? Script attacks are more easily detected and blocked (example: via the NoScript add-on). Scriptless attacks also attack your browser. How to steal data using the browser? (such as passwords, tokens and sensitive data in general)

Mario looks involved deeply in his job, it’s a pleasure to listen to him. He explained multiple types of attacks based only on CSS and HTML codes, no scripting at all. The first example demonstrated how to steal a password by using a CAPTCHA: http://heiderich.ch/opera/captcha/. The second one was a brute force attack against a complex password (25 characters) brute forced in 2262 checks: html5sec.org/invalid?length=25. Another amazing demo was a key-logger based on the accessKey() function: html5sec.org/keylogger. The last proof of concept was based on fonts. You can define your own font types and replace a string of characters by a single one. You can build your own directory of passwords stored in a fond (100K entries could fit). If the string is present, the corresponding character will be displayed. I won’t give more details here because I’m not fluent with HTML/CSS and the different examples were explained at a sustained speed. But have a look at Mario’s researches, he deserves it!
After the lunch, the second panel was organized (Joe McCray was not present). This time with a focus on attacks. The speakers were Georgia (with cute Minnie Mouse ears!) and Mario. The moderator was again Winn. Today, it’s easy to attack people as multiple ways to attack exists (BYOD, social network account, etc) . A good remark by Georgia: “If they want to steal my wallet or my phone, I’d prefer my wallet!“. This is a good proof that data are stored in new places which can also be attacked. Â Question to start the discussion: what about building “walls” between countries? Do you think laws will solve the cyber-criminality issues? Most said no in the audience.

In case of attacks, how to be sure that the attacker is really the good one? To attack your victim, compromise other servers in “suspicious” countries and attack from there. No, not all attacks originated from China are not started by the Chinese government. Some other questions: what’s the difference between cyber-terrorism and cyber-war? What will be the next type of attack? (APT 2.0 or SAPT – SuperAPT 😉 ).
Ange Albertini is a reverse engineer and owner of the website corkami.com. He talked about PE files. For me, this guys is simply crazy, writing PDF or PE files by hand 😉 He also developed its own tool to analyze PE files. What’s a PE file? It’s the Universal Windows binary! Plenty of information is also stored in PE! More info here: pe101.corkami.com.
Microsoft released “official” documentation on PE format but practically, the reality is totally different! Example: Microsoft says that value X must contain a value > 0 but a value of 0 does not affect the program execution. By modifying PE files, you could make them undetectable by anvi-virus. What to remember from this talk: Do not truss vendor documentation and PE is a mess!
Amol Sarware from Qualys talked about SCADA security. This presentation was the same as the one presented during BSidesLondon in April. Read me previous review, the talk was the same. Just one remark, why develop your own tool (“Scanscan”) and not integrate the researches within Nmap or Metasploit? Just wondering…

The afternoon continued with a talk was given by Nicolas Grégoire: “Attacking XML Processing“. This talk was also scheduled in Hack in the Box but I was not able to attend it, it’s done now! After a brief introduction of the XML concepts (XML content is everywhere, you’re using XML content all day long), Nicolas explained different types of attacks he developed and gave nice demos.

Based on different XML format (XXE, XSLT), Nicolas demonstrated mainly:
- How to perform DoS
- How to read information from the remote file system
Two important things I learned: By using some encapsulation mechanisms, it’s possible to make the malicious files undetectable by anti-virus (reaching the famous score of “0” on virustotal.com). And, secondly, php://filter/ allow data to be Base64 encode before being sent. Very useful to evade binary files! Well prepared demos, clear information, I was happy to follow Nicolas’s talk today.
Jayson Street closed the schedule with his talk “Why are doing it wrong?“. He’s doing a “blue team” job: He likes his IDS, firewalls but also being an attacker from time to time. It’s not always easy to be the latest speaker in a conference but those who left sooner really missed a big show!

With its own style, Jason reviewed some fails that can be seen in all our companies! Communication problems remain a big issue between information security guys and the management. They see us coming to request extra budgets. I’ll quote Jayson here: “Bosses are stupid“. The nice example was: “I’ve a problem with my email, please restart the Exchange server!” (Who never eared this story?). They don’t understand what we are doing and, for them, we simply… fail! Situational awareness is important. Jayson give the example of  a phishing site deployed on the April-foo day against a CIO. Another big difference between us: We are proactive and they are reactive. Don’t forget metrics. They are used not only to convince the management (they like pie-charts) but also to you to understand better what’s happening on your network (visibility!). To improve the communication, we have to make the first step and try to adapt our language to the management. What about users? In a company, people have been hired to perform a specific job not to perform information security! That’s why awareness towards them is a key.
The last part of the talk was addressed to us, the information security professional. As seen in the picture below, there is an infosec hierarchy: Most people working in this field have a “life” (they have kids, go fishing, drink beers). This is the “industry“.
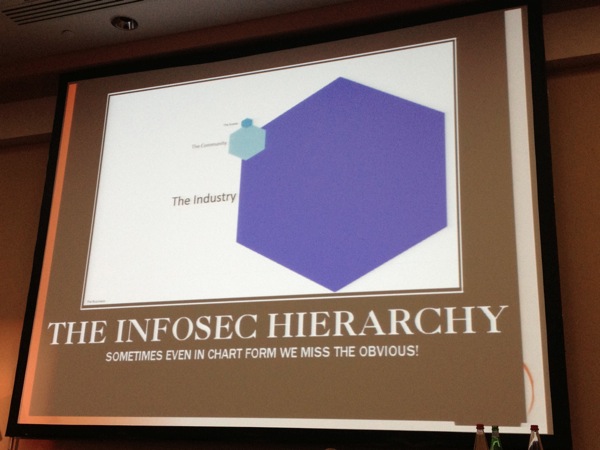
But only a small amount of them are part of the “community” (people who do researches, have blogs or simply follow conferences like this one to keep their knowledge at the higher level. Finally the “scene” is based on renowned people who are really contributing to the community. From my point of view, Jayson is part of this last one. He made a tribute for more local security conferences where local people could present their work. Don’t be afraid to submit your papers to CFP! Go ahead!
That’s done for the wrap-up. Unfortunately, I didn’t stay longer and won’t attend the next event (“La Nuit du Hack“). I need to organize my planning in a better wy next year. To all my friends and contacts who will attend, enjoy it! Finally, I’d like to thank Sysdream and Hackerzvoice for the organization and also the press pass 😉
One comment