
Back at the hotel, here we go with my wrap-up for the first day! I joined Disneyland Paris early from Belgium. It’s always frustrating for your kids when you tell them that you’ll “visit Mickey” during two days! The conference started three days ago with a set of trainings. According to the organizers, 60 people at tented them. Which is not bad at all! Trainings are followed by two days of conferences (16 talks are scheduled) in a nice environment. The number of attendees was around 300 (tickets sale sold-out). After the welcome word from Sysdream and the notification of some last-minute schedule changes, Mikko Hypponen started the day with his talk.
The title was “Where are we and where are we going?“. Mikko is working in the security field for 21 years and always so busy! In fact, why can’t we get rid of vulnerabilities? Because applications and systems have… bugs! The most popular mobile phone, the iPhone, will be five years old next week. When it was released, there was no known malware (just proof-of-concepts). Only jailbroken devices were targeted. Things changed today! More success your product has, more it will be the target of attacks. In 1945, the nuclear science lost its innocence when the nuclear bomb was used against people. The same can be told for computers! Computer science lost its innocence in 2009 when Stuxnet was launched against critical infrastructures. Today, attackers can be classified in three types:
- Criminals: they are doing business (to make $$$)
- Hacktivists: they protest and send messages to authorities or organizations
- Governments: They need to keep control of citizens.

Mikko gave a good example of business for criminals: The website estdomains.com allows you to register domain names but your account will never be cancelled. More complaints they receive from CERTS or governments, more your bill will increase. If you have money, you’ll just remain online! Another business reference was made to Gwapo’s professional DDoS service. Another growing problem: ransom trojans. They are distributed via exploit kits like Blackhole. Often, people pay because they just don’t have a recent backups. If you have one, f*ck them and reinstall your system but don’t pay! Fake message against counterfeited softwares or illegal material or pornographic material became also common. All of those are based on people fear of authorities. And what about banking trojans? (well known as Zeus or SpyEye). Finally, the governmental attacks. A good example, is Iran which  hacked Diginotar to generate certificates (they don’t have a CA because nobody trust them). With those certificates, they were able to sniff Google traffic (gmail.com). And people died in Iran because of that!  A funny story, Stuxnet was based on pictures found on the Iran president website. Finally, the last one “Flame”…  Flame is huge key logger and screen grabber, SSH, SSL and LUA libraries. Collects excerpts from documents (doc, xls, ppt, auto cad!), it collects GPS coords from your JPEG files. It checks paired devices, connects to your phone and collects the address book. stores data to USB sticks and even if no network connectivity. Mikko’s conclusion for his talk: Yes, since 2009, computers became weapons too! This is a very good speaker, always a pleasure to listen to him.
The second presentation was “What are the new means for cybercriminals to bypass and evade your defenses?” by Klaus Majewski from Stonesoft (a sponsor of the event). The subtitle was “Being in the eye of the perfect storm“. He started by explaining the dynamics of security.  I like the quote “Marketing can make you feel secure”. Helas, the talk switched to a commercial presentation of the Stonesoft security product. One of the message broadcasted by Klaus: “Internet is broken but we need it more and more!” (unpleasant truth). He spoke a bout a new concept called AET (“Advanced Evasion Techniques“).

A live demo was performed. “live” is the right word: the speaker disclosed a lot of interesting information on his script. That’s a fail in a security conference:
The next talk was performed by Chris Hadnagy. He is a professional social engineer and maintains the website www.social-engineer.com. Presentation about social engineering looks always the same. But there are more interesting when nice statistics or tips are disclosed. That was the case with Chris’s talk. A lot of people are doing social engineering, example: doctors, kids and therapists. He also cited Sparky Blaze: “In my mind, SE is the biggest issue today!“.

Today’s common methods of SE attack are:
- Phising
- Phone
- Tail gating / impersonation
According to Symantec, 1 of 343.1 emails is phishing! Chris gave examples and some of them were really good! (no more typo errors, professional look, etc). What about phone calls? They increased by 33% (phone scams). Major worldwide events are now a good source of inspiration. Example, a few hours after the tsunami which hit the Japan, rogue websites were already online! Ready to collect information and perform the callback activities. Did you know that Sony was hacked due to social engineering? Only six(!) calls were required to get all the information to conduct the attack. Some slides presented nice statistics about passwords. A study was about the differences in passwords between men an women. Details are available here. If you are interested in passwords statistics, I would recommend you to have a look at the tool written by Digininja: Pipal. To conclude Chris talk review, I liked his quote: “Don’t wear a gun, wear a clipboard to get information… “. It says all! (By the way, thanks for the nice sticker Chris!)
Back to work after the lunch with a panel about “Computer Network Defense” . The moderator was Winn Schwartau with Jayson Street and Chris Hagnady. Today’s panel focus was on the “Blue Team“. Tomorrow, the offensive side will be covered.

Topics covered:
- What about SE in France? Is it different?
- Incident management (“When they get in, suddenly nobody’s in charge!”)
- Cloud computing
- Failing in security (all of us fail at a day!)
- BYOD
Then talks continued with: “HTML5 Something Wicked This Way Comes” by Krzysztof Kotowicz. His presentation explained different types of attacks based on the new HTML5 standard. The scenario was about owning Bob, the CISO of an organization. Funny.

The first attack was based on Filejacking. This one is only possible with Chrome but, if successful, allow JavaScript to read files from your system. The attack was tested live during 13 months via this URL:Â http://kotowicz.net/wu. It gave nice resulst! Lot of people were pwned. Of course, to attract people to the malicious page, some social engineering is required (again!). The second technique was to use rogue access point while Bob is traveling and use the HTML5 Offline Web Applications (“<html manifest=cache.manifest>“) or “AppCache poisoning“. The next one was “Silent File Upload“. Purely based on JavaScript, its possible to upload file to a service used by the victim (ex: Flickr). The two last attacks were based on drag-and-drop operation deguised as online games. It looked impressive but my knowledge of JavaScript and HTML5 is too low to be able to write a review here! The conclusion for this talk could be: “HTML5 is attacker’s friend too, don’t get framed! Users base pwnage FTW”. Oh, just a word for the developers amonst you:Â use “X-Frame-Options: DENY“!
Due to a last minute planning change, the talk proposed by my friends Jayson Street and Frank Breedijk was cancelled. It was replaced by Fernando Gont who talk about IPv6 security. He started with a brief introduction about the new protocol (always useful). What were Fernando’s motivation for this talk? There are lot of myths about IPv6 that must be killed! They have a negative impact on IPv6 deployments. Let’s try to separate the fud from facts. Today, engineers have less (or worse, no) experience with IPv6 and implementations are less secure. By deploying IPv4 & IPv6 networks, complexity of the Internet will grow (tunnels, nat, dual stacks, “old users”). Less trained people but it’s a key to remain in this business.
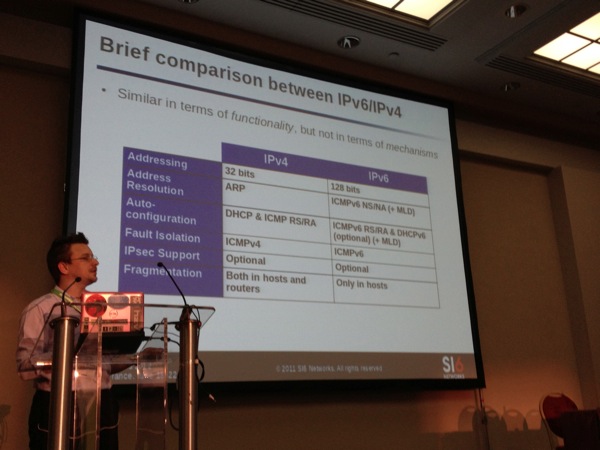
Honestly, the talk was a good resume of the new IPv6 features but focused on pure security too late. Only the part about host scanning kept my attention! Keep in mind that IPv6 reconnaissance can be performed via Torrents or mailing lists archives (by extracting IPv6 addresses from the SMTP headers. To remember from this talk: “Deploying #IPv6 networks without proper training is insane!“. Even if I found the talk not enough focused on security, Fernando has an excellent knowledge of his domain! I will be present at BruCON 2012 to give a two-days training. That is a good opportunity to learn more about IPv6! Details are here.
Jorge Sebastiao came on stage with a presentation called “Tracking modern weapons of mass destruction – Stuxnet“. Â Holliwood was always inspired by computer attacks (Wargame, Die Hard 4). Jorge reviewed the malwares Stuxnet and Flame. Nothing brand new! Maybe the most important think to remember is: “What you see on your screen is not always what’s happening in real life“.

To demonstrate this, he played the Symantec video where they make a balloon explode due to an infected PLC (the pump did not stop when required). He also played a second video which explain how specific devices can be destroyed by submitting them to a specific frequency. This proves that malware authors made a lot of research to find those vulnerabilities!
The last talk was presented by Andrei Costin about the Postscript language. It was the same as the one presented during Hack in the Box in Amsterdam, one month ago. Check out Hack in the Box wrap-up to a review of this awesome research.
My to presentations for today? Mikko Hypponen & Chris Hadnagy. The first day finished smoothly at the Planet Hollywood restaurant with friends!
One comment