 After some wrap-ups, let’s come back with a more practical blog post. I like to keep a good balance between hands-on and wrap-ups or theoretical articles. Today, it’s almost impossible to implement a good security without buying some commercial tools. At least, you have a corporate firewall provided by a big name. Security vendors use various marketing techniques to sell you more and more wonderful solutions which can magically solve all your problems and, sometimes, even make coffee! But what most of their users ignore is that almost all appliances or software solutions have API’s (“Application Programming Interface“) available to interact with other products. API’s help different softwares to communicate with each others in a structured way. My question is: Are you making the most of your security tools? Here is a practical example.
After some wrap-ups, let’s come back with a more practical blog post. I like to keep a good balance between hands-on and wrap-ups or theoretical articles. Today, it’s almost impossible to implement a good security without buying some commercial tools. At least, you have a corporate firewall provided by a big name. Security vendors use various marketing techniques to sell you more and more wonderful solutions which can magically solve all your problems and, sometimes, even make coffee! But what most of their users ignore is that almost all appliances or software solutions have API’s (“Application Programming Interface“) available to interact with other products. API’s help different softwares to communicate with each others in a structured way. My question is: Are you making the most of your security tools? Here is a practical example.
I’m always trying to keep my blog free of mentions to commercial products but today, I’ll make an exception and show you how to increase your overall security level by interconnecting two security products: A FireEye malware analysis appliance and a PaloAlto firewall. If you want more information about them, visit their respective websites. My lab was based on the environment showed in the picture below:
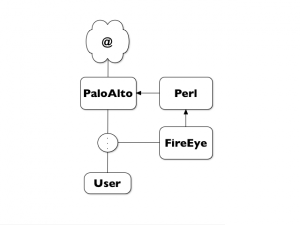
We have a user accessing the Internet through a PaloAlto firewall. The FireEye appliance is sniffing the user traffic and analyzes in real-time all suspicious traffic. This is an easy setup which does not “break” the network. Just a tapping port is required. But in this case, the FireEye appliance cannot interact with the traffic (passive mode). Why not configure FireEye to notify the PaloAlto firewall and block IP addresses detected as malicious? How to achieve this?
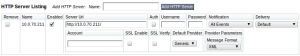
Step 1: On FireEye, configure the HTTP notification to send information in XML format to a web server:
Step 2: Create an API key on your PaloAlto via HTTPS:
https://paloalto.hostname/api/?type=keygen&user=username&password=password
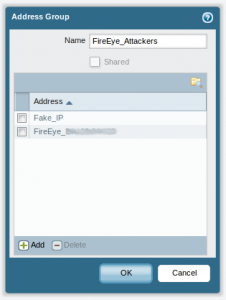
Step 3: Create a new address group in the PaloAlto configuration and block all traffic from/to this group:
Step 4: Using a few lines of Perl code, run a web server which will perform the following tasks:
- Accept XML data sent by the FireEye appliance via POST requests.
- Extract the attacker IP addresses
- Generate GET requests to the PaloAlto firewall to create a new address object, add it to the existing group and commit the configuration
My Perl script is available here and is just a proof-of-concept. The script does not run as a daemon, does not authenticate the FireEye and does not offer SSL. Quick and dirty! It should run on any Linux distribution.
My goal with this proof-of-concept is to demonstrate that security products can be deployed and integrated in a intelligent manner to increase the global efficiency of your security environment. Try to learn your products, how they work and how their information can benefit to others… Finally, please note that the two vendors mentioned in this blog post were selected as examples. The same could apply to plenty of others! Conclusion: RTFM! 😉
Yes, it could. But it could be interesting to notify other firewalls with attackers IP addresses (ex: remote offices, branches, etc).
BTW, I’m also working on a script which do the same with CheckPoint firewalls (via SAM).
Thanks again! I found out that FireEye can be deployed inline to block malicious web sites. No need for Palo Alto Networks (and save a bundle of money!)
Hello Erick,
The webserver is the script itself! It binds on port 80 and listen to HTTP requests!
Great post! Could you please provide more detail on how to setup the Web Server to accept notifications and pass them to the API? I’m currently trying to do a similar setup. I’m not very familiar with Web Servers so every detail you can provide would be very appreciated.