
There was an interesting post on the diary page of isc.sans.org yesterday: Some readers asked why ISC did not switch the InfoCon status to yellow due to the recent IE 0-day exploit. The on-duty ISC handler explained the situation and why they decided to stay “Green”. The following question popped up out of my mind: “What’s the real value of threat levels? Which one can we trust?”
The Internet Storm Center (“ISC”) is not the only organization to provide a “Security Threat Level”. There are other organizations like McAfee, Symantec, ISS, TrendMicro, etc. To have a good overview of the threat level amongst them, I often use the Threat Level Aggregator provided by CERTstation.com. Take the time to visit the website and you’ll immediately understand the problem:
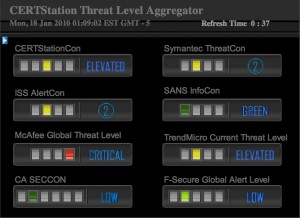
From the height aggregated services:
- One is “critical”,
- Five are “elevated”,
- And two are “low”.
If you’re not a security professional and visit this page, how will you understand the content? Am I in danger or am I safe when I use my computer? Do they monitor the same stuff? Worst, it can be disturbing for the management: why don’t the admins take action in such “crisis” situation?
My first concern is the “independence”. Some of companies providing a threat level indicator do business within the security landscape (example: they sell anti-virus software). It’s only my point of view but I prefer to trust an independent organization. Second, do not assume all information provided. A new zero-day exploit facing an application used on your network may have a smaller surface attack depending on your configuration and practices.
It’s important to have a clear view of:
- the software and hardware components used in your environment (model, version, patches),
- how they are used and configured (change management).
A good example? I remember the case of ProFTPd in the beginning of 2009. This popular FTP server was vulnerable to an authentication bypass but… only when configured with a MySQL backend! There was a debate inside my company about the severity of this exploit. In fact, no customer was using the vulnerable authentication method!
When a new security issue is disclosed, don’t raise the red flag immediately. Take some take to deeply analyze the facts and detect potential risks that can affect the business. It may also happen in the other way: a low vulnerability may have a bigger impact inside your organization. Take care!