
“Cloud computing”! This is a hot topic in IT security for a while. I won’t explain why security is so importing within the cloud. To have a good overview, I recommend to follow Craig Balding’s blog.
For sure, you already have personal data stored on the web. You use webmail services like Google, you post pictures and videos on Facebook. The major issue is the total loss of control when posted. Where are they stored? Is privacy respected? Worse, if you decide to bring some material off-line, it has been indexed by robots or is it really removed from the servers? Some data may also become obsolete or confidential after some time.
That’s why the Washington University developed a product which adds some kind of “best-before date” on the data you publish on-line. The idea is very simple: when you create some content (ex: a blog post), you specify after how long the data will become unreadable for everybody, even you, the author!
To create self-destructing data, let’s have a look to the Vanish tool. It’s a software based on two components: A Java application and a Firefox plug-in. Once the software has been installed (runs on Windows or almost all Linux distributions), select any text you need to vanish and choose the option “Vanish -> Create Vanish Message” from the context menu:
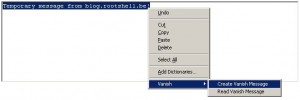
Your original text will be replaced by something like:
-----BEGIN VANISH MESSAGE----- Use http://vanish.cs.washington.edu to read this message. This message will self destruct by Thu, 30 Jul 2009 19:27:47 GMT AKztAAVzcgBGZWR1Lndhc2hpbmd0b24uY3MudmFuaXNoLmludGVybmF sLm1ldGFkYXRhLmltcGwuRXBvY2hBd2FyZU1ldGFkYXRhSW1wbE1yiFVDG n2bAgACSgAMZXBvY2hfbGVuZ3RoTAAIbWV0YWRhdGF0ADVMZWR1L3dh c2hpbmd0b24vY3MvdmFuaXNoL2ludGVybmFsL21ldGFkYXRhL01ldGFkYX RhO3hwAAAAAAG3dABzcgBHZWR1Lndhc2hpbmd0b24uY3MudmFuaXNo LmludGVybmFsLm1ldGFkYXRhLmltcGwuSW5kaXJlY3RLZXlNZXRhZGF0YU ltcGw6bcmI6fsf7QIAAlsAEmVuY3J5cHRlZF9kYXRhX2tleXQAAltCTAAIbWV0 YWRhdGFxAH4AAXhwcHNyAEFlZHUud2FzaGluZ3Rvbi5jcy52YW5pc2guaW 50ZXJuYWwubWV0YWRhdGEuaW1wbC5CYXNpY01ldGFkYXRhSW1wbNgVQ Ujt/E3XAgACSgANbG9jYXRpb25fc2VlZEwABnBhcmFtc3QANkxlZHUvd2Fz aGluZ3Rvbi9jcy92YW5pc2gvaW50ZXJuYWwvbWV0YWRhdGEvVkRPUGFyYW 1zO3hw6Gffaq4cVxNzcgA0ZWR1Lndhc2hpbmd0b24uY3MudmFuaXNoLm ludGVybmFsLm1ldGFkYXRhLlZET1BhcmFtc7292Mmleh6MAgAISgALY3JlYX Rpb25fdHNJABVlbmNyeXB0aW9uX2tleV9sZW5ndGhJAApudW1fc2hhcmVz SQAJdGhyZXNob2xkSQAJdGltZW91dF9oSgAGdmRvX2lkTAAUZW5jcnlwdG lvbl9hbGdvcml0aG10ABJMamF2YS9sYW5nL1N0cmluZztMAA9lbmNyeXB0 aW9uX21vZGVxAH4ACnhwAAABIsfEIk8AAACAAAAACgAAAAcAAAAYDIstI4 Viu3R0AANBRVN0AANDQkOREhq410f4hqFaaoICvN9kU/q2yqdxZ9LRxYEYX 3a1KKBAgTbUnYZQkDnMn5areXA= -----END VANISH MESSAGE-----
Anybody will be able to decrypt the message until Thu, 30 Jul 2009 19:27:47 GMT (I configured my Vanish add-on expiration timeout to 24 hours). To read the original text, recipients of your message must have the same Firefox add-on installed, select the vanished message and use the second menu “Read Vanish Message”. Once the expiration date expired, nobody will be able to decrypt the message! Simple and powerful! Please keep in mind that your data won’t be encrypted nor signed.Anybody will be able to read the message content! Let’s have a look at the video which describes the application:
Note: the Vanish application requires Internet connectivity to work. Operations rely on the Vuze network!
A new program Vanishing Message has been released by John Kapili. Vanishing Message is a file message that can be sent by email attachment or file transfer. The message can be read by the recipient then vanishes without a trace. As we all know there are times when we need to send a message to someone that we want no trace of later. Vanishing Message uses a random encryption on all words, no word is ever encrypted the same. The message vanishes if exited, cannot be copied, if viewed longer than 1 minute it vanishes and you can use the same file to forward or email another person a new message. So prove it!!! Did it ever exist?
http://www.JohnKapili.com
http://www.johnkapili.com/news.php?item.39.1
Indeed! Vanish used “as is” does not prevent any copies of the original data. Except if the original version is signed using your PGP private key.
On the other side, the goal is clearly to prevent your data to be indexed and lost in the “Cloud”. Preventing people to save a copy of it locally on their hard drive is another problem.
AFAIK they state in their paper that explicitly do not consider the case when a trusted insider makes a copy during the allowed time period (ie Alice decodes the message in the interval it is valid and takes a digital – and thus perfect – copy of it and passes it on to Eve). While it is a perfectly assumption, it does limit the effectiveness of the system a great deal and it is also not the scenario most people think of when they hear “self destruct”.
my 2c