
Today, the majority of websites offer dynamic content to visitors. All information is stored in back-end databases and processed live. A classic infrastructure is based on LAMP (Linux, Apache, MySQL, PHP).
Unfortunately, “database” means also a broaden surface attack. And risks are multiple: SQL injections, data leak, data alteration or destruction. To maintain the CIA triad principle (Confidentiality – Integrity – Availability), we have to implement counter measures.
First line protection is performed by IP firewalls (mainly layer 4) and WAF’s (Web Application Firewalls – layer 7). A new defense line can be deployed using GreenSQL, a database firewall which also work at layer 7.
In a client/server model, GreenSQL is placed between the database(s) and the clients:
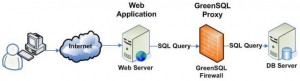 |
It acts as a reverse proxy and analyzes the SQL commands passed to the server. Based on rules, GreenSQL forward or drop the request. The “proxy” can run in several modes: IDS (detect), IPS (block suspicious traffic), learning or active mode. In IPS mode, SQL requests are allowed or denied based on the heuristic engine. I’ll not give more info about the internal of GreenSQL, check out the documentation for more details.
Configuration and monitoring is performed via a simple web interface:
 |
So, what can I say about GreenSQL? The product has certainly lot of advantages and can reduce the attack surface of a database. However, it is certainly not an alternative to security at development level!
Developers must be aware of security: Access to SQL databases can be secured using standard features:
- Do not use DBA credentials in your web applications
- Restrict the set of allowed commands using GRANT/REVOKE
- Define views and privileges to retrieve data
- Deny access to system tables
My recommendation is to use those SQL features and GreenSQL at the same time. A nice feature could be a real time export of logs via syslog. Information could be correlated with other events to perform security incident analysis (ex: forward events to Splunk or any other commercial SIEM appliance.
Check out the presentation of GreenSQL made during the OWASP Israel 2008 conference.
Nice article!
Some more info on GreenSQL :
http://www.databasejournal.com/news/article.php/3794771/Firewall-MySQL-with-GreenSQL.htm
And an old, but still useful alternative for Oracle using Oracle Net:
http://www.dbazine.com/oracle/or-articles/nanda8