
Beginning of this month, the Internet Storm Center published a diary about a new malware (called Trojan.Flush.M) detected by Symantec: Rogue DHCP servers.
The malicious code was analyzed by Symantec. Once the machine infected, it sends fake DHCP offer packets using UDP ports 67 and 68 when another computer on the same network renews its IP address. It then attempts to hijack the DNS configuration of other computers on the same LAN network:
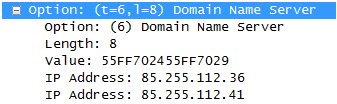 |
Changing name servers is really nasty. It’s fully transparent for the end user and potentially any web site can be redirected to a false one to conduct phishing attacks. E-mail flows can also be redirected to malicious MX records.
A good protection against this kind of attacks is to not allow direct DNS requests trough firewalls (or at least restrict them to your ISP name servers). All internal hosts must use a local resolver. Unfortunately, this is not always the case.
Groundwork or Nagios are monitoring tools which use an infrastructure based on plugins to perform monitoring of devices and applications. A plugin already exists to monitor a DHCP server:
# ./check_dhcp -h
check_dhcp v2018 (nagios-plugins 1.4.13)
Copyright (c) 2001-2004 Ethan Galstad (nagios@nagios.org)
Copyright (c) 2001-2007 Nagios Plugin Development Team
This plugin tests the availability of DHCP servers on a network.
Usage: check_dhcp [-v] [-u] [-s serverip] [-r requestedip]
[-t timeout] [-i interface] [-m mac]
Options:
-h, --help
Print detailed help screen
-V, --version
Print version information
-v, --verbose
Show details for command-line debugging
(Nagios may truncate output)
-s, --serverip=IPADDRESS
IP address of DHCP server that we must hear from
-r, --requestedip=IPADDRESS
IP address that should be offered by at least one DHCP server
-t, --timeout=INTEGER
Seconds to wait for DHCPOFFER before timeout occurs
-i, --interface=STRING
Interface to to use for listening (i.e. eth0)
-m, --mac=STRING
MAC address to use in the DHCP request
-u, --unicast
Unicast testing: mimic a DHCP relay, requires -s
Send email to nagios-users@lists.sourceforge.net if you have
questions regarding use of this software. To submit patches or
suggest improvements, send email to
nagiosplug-devel@lists.sourceforge.net
I patched the plugin code and added a new option to detect any change in the name server offered by the DHCP server. A new command line flag has been added: “[-n requesteddns]”. You can specify a name server IP address. If the offered address is different (via the DHCP option 6), the plugin will return a CRITICAL state. In the example below, the DHCP server must offer 192.168.254.1 as official name server:
# ./check_dhcp -n 192.168.254.12 CRITICAL: Received 1 DHCPOFFER(s), ROGUE DNS WAS OFFERED (192.168.254.1), max lease time = 43200 sec. # ./check_dhcp -n 192.168.254.1 OK: Received 1 DHCPOFFER(s), max lease time = 43200 sec.
A specific DHCP server can also be checked (if you have several servers distributed across a backbone:
# ./check_dhcp -s 192.168.254.1 -n 192.168.254.2 CRITICAL: Received 1 DHCPOFFER(s), 1 of 1 requested servers responded, ROGUE DNS WAS OFFERED (192.168.254.1), max lease time = 43200 sec.
This patch is based on the Nagios Plugins 1.4.13. The new plugin is free to download: check_dhcp.c. Note that only the first name server is checked! (the DHCP option 6 allows multiple IP addresses).
The patch is provided “as is” without any warranty. It’s a quick fix and it worked for me. Send me your feedback or remarks.