Internet is a infinite source of free software! If you are looking for a small tool to automate tasks, convert files or make your life easier, there are chances that somebody around the world already wrote some code and distributed it for free on the Net.
But, on a security point of view, can you trust the guy who provides you the expected tool? Can you be absolutely sure that no back door nor hidden feature remains in the code? Here is a good (bad?) example to illustrate the potential threads: G-Archiver.
Basically, this tool performs a backup of your G-Mail account on a local drive. Indeed, it can be interesting to have a copy of your important emails. We never know what can happen with online services. As G-Archiver was developed with Microsoft .NET, a guy was interested to understand how worked this little tool and used Reflector to analyze the source code. And he discovered a nice hidden feature: Every time the software was configured to backup a mailbox, it sent a copy of the user credentials to the developer’s own mailbox! Check the screen capture:
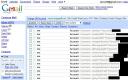 1000+ credentials were stolen like this! If the author would like to keep some statistics about the users, why not just send ask for a email address + country code. But in all cases, the end-user MUST have the choice to publish or not his personal information.
1000+ credentials were stolen like this! If the author would like to keep some statistics about the users, why not just send ask for a email address + country code. But in all cases, the end-user MUST have the choice to publish or not his personal information.
How to protect you against data leak?
- Never trust a software coming from an unknown source!
- Read the end-user agreement. It’s boring I know but in some cases, it can be stated that information will be collected for further processing.
- If the software archive is delivered with a hash value (MD5, SHA1), compare it with your local copy! It will not protect you against problems as described above but will prevent you to install a modified copy of the original package.
- Install and run the software in a virtual machine.
- Sniff your outgoing traffic for unusual packets (IDS/EDS)
Read the full story on codinghorror.com.