And we are back to the Disneyland conference centre for the second day of Hack in Paris… It looks that the night was very short for many people (who hacked all night long?) because the planning started with a delay!
And we are back to the Disneyland conference centre for the second day of Hack in Paris… It looks that the night was very short for many people (who hacked all night long?) because the planning started with a delay!
The second keynote was presented by Jayson E. Street. Like Winn who presented the opening keynote yesterday, Jayson is a regular speaker and comes always on stage with interesting ideas. This time, his talk title was “Around the World in 80 Cons!â€. Last year, the talk was more technical (about spear phishing), this year it’s more about the “communityâ€. Jayson likes to travel but not like a classic tourist. He like to meet people. A few months ago, he had the idea to make a survey about how hackers and the hacking culture is seen in different regions. What are the different culture around the globe? He started by reviewing some charts and numbers from different incident report papers released by vendors. The way information is presented can clearly have an impact on our views. That’s why disclaimers are important. The numbers presented are only a “tip of the iceberg†and my reveal false ideas about some countries.
Think about China. They are often accused:
- To spy on their citizens (and what about NSA?)
- To spy on other countries (and what about GCIH?)
- To infect nations computers with malware (think about Stuxnet and Flame)
- To censor the press
- To suppress protestors (think about Bush and his free speech zone)
In the same reports, even neutral or pacific countries are hosted hostile servers (C&C). Then Jayson reviewed the results of his survey which was based on three main questions:
- How did you find out about hacking?
- What’s the perception of hacking for the public?
- Is hacking in your region seems as more for crime, hacktivist, nation-sates, other?
Another fact, hackers aren’t … equally to other criminals. Jayson resumed the situation with two slides which compared years of jail for hacking related crime and traditional crime performed by really bad guys (murder, rape, …). Hackers are sentenced up to 20 years of jail. Other criminals get between 3 to 6 years! Think about Aaron Swartz story! The perception of hacking is very important. Why are hackers always shown in dark rooms wearing black sweats? The media have a major impact on how hackers are seen. It’s also our role to “be a voice†and broadcast the right message about what hacking really is. Also, think about the future, our kids must understand what hacking is and be aware! It was an awesome keynote (as usual for Jayson).
Mario Heiderich started today’s set of talks with one about JavaScript MVC or “Model View Controllerâ€. The website describes it as an open-source framework containing the best ideas in jQuery development. Why speak about this? Because such frameworks become more and more popular, but are they really secure? Their usage is clearly growing. They are written in JavaScript and are huge and complex.
They allow lot of crazy stuffs that change ways how developers work with JavaScript (you don’t work in the classic way – interfacing with browsers). Amber, KnockOut, Ember are well known frameworks. On the websites, we can find lot of marketing messages like “they increase productivityâ€, “they are simple and intuitive“, etc. With some examples, Mario showed how it is possible to write apps with only a few lines of code. Then, he demonstrated how code execution is still possible. eval() remains intensively used. This talk was presented during an OWASP Belgium chapter meeting and I already covered it here.
After a short coffee break, we go further with Alvaro Alexander Soto who presented “Extreme Forensics Reloaded 2Q/2014â€. The goal of the presentation was to explain how to work beyond traditional forensic tools. Digital forensics evolved from PC’s to cloud computing.
New tools and software must be developed to face all the cases. By the way, if you deploy a forensic lab, Alvaro recommends to make it ISO 17025 compliant (which will make it compatibe with scientific procedure). Forensics tools and procedures must evolve with all new technologies (which are more and more complex). Some future paths were reviewed by Alvaro:
- OS + internals
- NOS + internals
- Mobile phones / smart phones
- Digital devices / appliances
- Reverse engineering / malware analysis
- App servers / Web 2.0, 30
Of course, new tools must also b deployed:
- Faraday cages
- Sand boxes
- Spectrum analyzers
- EEPROM / NAND readers
- Data mining tools
Alvaro make an interesting demonstration of a tool to read data from a broken hard drive. One think to keep in mind: modern tools are able to make some “magic” and read data from corrupted or broken devices, it looks awesome. Finally some recommendations if you are busy with forensics investigations:
- Team work is mandatory
- Research beyond the standard channels
- Use VM and isolation
- Avoid self-destruction of data (mobile)
- Do some research
- Keep always the legal aspects in mind (depends on your region)
- Share!
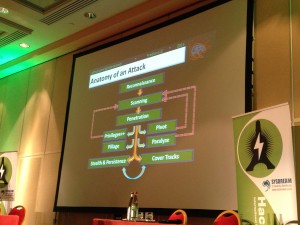
Due to a last minute change in the planning, “Plunder pillage and print†was presented earlier by Deral Heiland and Pete Arzamendi, both are pentesters at Rapid7. Their topic focused on “MFP†(Multi Function Printers). All started with a fact: What want pentesters? Usernames and passwords to get “sheeeeeells†or course!
In 2010 they owned some printers and got access to Windows AD user accounts with a success rate of 10-15%. In 2014, the security did not change and chances to find juicy information is even higher. Why?
- They contain usage tracking features (tracking colour levels)
- They have a scan to email feature
- They have a scan to file feature (and store to a share)
- They use LDAP authentication
- They allow remote firmware upgrade
First step: plunder! What can we expect from such printers? Via the web interface, we have access to interesting data depending on the printer models:
- Dell : Usernames, application and client hostname
- Xerox: Usernames & applications
- HP: Usernames & applications
Step two: pillage! Printers need to communicate with users. Why not try to perform an adress book extraction attacks (usernames, email addresses and passwords!) Two examples were described by the speakers:
- On Canon printers, passwords are encrypted by default during export but encryption settings are end-user controlled and can be turned off.
- On Konica printers, export is performed via SOAP messages (on ports TCP/50001 & TCP/50003). It’s also possible to get shares info (SMB, FTP, SMTP) with credentials.
Then, another type of attack was explained: The “pass-back-attacksâ€. It targets printers which support authentication services like LDAP. Once connected to the printer web interface, change the LDAP server address to ours and trigger a LDAP query: credentials sent to us in clear text! Up to now, most examples in this presentation were not high level. The speakers were just asking the printer to give us some information. The next demo targeted Xerox printers. A rogue document was created and once sent to the printer over port 9100 (JetDirect), a root shell is started to a remote netcat listener. Amazing! The next step was of course to automate the attacks. To achieved this, a new tool has been developed and is called Praedasploit (Praeda + Metasploit). It works in four steps:
- Scan network for embedded devices
- Fingerprint them
- Run Praeda modules
- Gather data and log it
Some modules have already been created like a Xerox LDAP pass-back module or a Konica address book extract module. The tool is available here if you’re interested. So how to protect against such attacks?
- Change default passwords!!!!
- Patch
- Disable firmware upgrades
- Don’t expose to internet
- Functional isolation (segmentation & ACLs)
As you can see, there is nothing brand new right? This is exactly what was discussed yesterday during the talk about “BPT” (Basic Persistent Threat)!
After some junk food with friends, Sebastien Andrivet started the last set of talks with “C++ 11 Metaprogramming technics applied to software obfuscationâ€. As introduction, Sébastien made an awesome video looking like an Hollywood movie trailer, awesome!
What’s the problem with obfuscation? He started with a demo of a well-known MDM (“Mobile Device Managerâ€) client used normally to enforce the security of a device. Sebastien demonstrated how easy it is to find the code responsible of jail break detection. How? Just be searching the string “Cydia†(the well-known alternative app market for jailbroken devices) in the code, it’s quickly solved. The application is just searching for some well-known application. If one if found, the device is considered as  jailbroken. Easy to patch and return always “falseâ€. That’s why obfuscation can be helpful even if the principel of “security by obscurity” is not considered as the best one. The goal of obfuscation is to create code that can’t be easily understand. How be transforming the source code or the binary code. Sebastien explained how to use C++ instantiations to obfuscate the code. He reviewed C++ templates and why they will be helpful in the obfuscation process:
- They are programs that manipulate or produce programs
- This is a subset of C++
- Turing-complete
- Fully supported
Then demonstration with details followed:
- Demo 1 – strings literal obfuscation
- Demo 2 – obfuscate calls to functions
I’m not a developer and some concept were too complex for me but the principle looks very interesting!
The next speaker, Cyril Brunschwiller talked about “Energy Fraud and Orchastrated Blackouts: Issues with Wireless Metering Protocols (wM-Bus)â€. After a quick review of the Smart Grids architecture, Cyril explained why Smart Metering will be mandatory in a near future.
Collerctors are part of the infrastructure and support multiple protocols (GPRS, Ethernet, WLAN, WiMax). Meters are talking to collectors. Wireless M-Bus is used to exchange information between the collector and the meter. It’s used across Europe (15M devices deployed today). Cyril explained the different layers of the protocol with frame structures (with lot of details). Good news, encryption is available but is it properly implemented or “Are we safe using AES?†he asked. According to Cyril, no! He demonstrated how the encryption is badly implemented and could disclose interesting information for an attacker. As an example: Encryption packets are the same if there is no energy consumption. So, it’s easy to detect if somebody is at home or not. The integrity of packets can also be abused! Which means that potential attacks could introduce wrong tariffs or false reporting…
He performed some demonstrations of energy fraud. There exists sender sniffer and simulator devices which is handy for demos and labs. The first demo was re-injecting an old packets into the network. It was accepted! The scond one was replacing the device string ID with a funny one: “Hack in Paris“. But more critical scenario could happen: What about war-driving into a city and broadcasting disconnect messages to smart meters? Think about this! We are close to Die Hard 4! If you’re interested, have a look at Cyril’s blog for more info.
The last talk was presented by Solomon Sonya: “Splinter the RAT Attack: Create your Own Botnet to Exploit the Networkâ€. Solomon’s motivation for this talk were multiple: network defense is always behind! It’s very difficult to address emerging threats.
First, Salomon reviewed some botnet terminology:
- Controller (C&C)
- Dropper
- Implant (the “listenerâ€)
The concept of dropper is to be as smallest as possible (exploit, malicious PDF, SE toolkit, malicious insider, …) and install the implant. Then Salomon explained the principle of the “Beacon bot“: to minimise footprint and detection on the network (by avoiding very long sessions like MetaSploit does). It works with the following steps: wake up, check-in, download & execute commands, sleep, recurse.
Salomon performed lot of demos of his own botnet:
- Executing remote commands
- Payload migration. The new payload was a reverse TCP to Armitage Nice way to start a session to another tool.
- host file modification
- DoS
Nice research and good presentation, the code is available here.
And finally, to close the event, we had a very interesting (and unique!) panel with the following people:
The moderator was Winn Schwartau and the (hot) topic: “Global surveillance: Security VS Privacy“. Immediately, we saw that the panel was split in two camps: the pro-privacy and the pro-security. In fact, there was three camps: Annie & Hans defended the privacy, Dave defended the security and Eric, due to his current position (working for the French Gendarmerie Nationale), was a little bit in the middle…
As expected the debate was intense and both parties had great arguments in favor on privacy or security. There was interesting questions from the audience. Hopefully, the key point for all the panelists was the same: We need more transparency!
This is over for me, I’m already back in Belgium. Unfortunately, I won’t attend the 2014 edition of la Nuit du Hack. Thank you to Sysdream for the great organization and see you next year…