 Mobile devices are more and more seen as nice targets from attackers’ point of view. Which is easily understandable: the market is exploding and people still don’t realize that a mobile device is not only a mobile “phone” but a mobile “computer” with an operating system, I/Os and… applications! The mobile OS landscape is spread over two systems: iOS (Apple) and Android. Apple is renowned to lock its market share and keep a good control on it, even if they’ve a glitch from time to time. To install an application on your iPhone/iPad, go to the AppStore. Of course, if you jailbreak your device, they are alternative stores but let’s assume that you’re a good boy/girl!
Mobile devices are more and more seen as nice targets from attackers’ point of view. Which is easily understandable: the market is exploding and people still don’t realize that a mobile device is not only a mobile “phone” but a mobile “computer” with an operating system, I/Os and… applications! The mobile OS landscape is spread over two systems: iOS (Apple) and Android. Apple is renowned to lock its market share and keep a good control on it, even if they’ve a glitch from time to time. To install an application on your iPhone/iPad, go to the AppStore. Of course, if you jailbreak your device, they are alternative stores but let’s assume that you’re a good boy/girl!
Android is more open and, next to the official store (Google Play), many alternative sources of applications are available to us. Some of them suffer of a total lack of control and we are not always sure that the downloaded application is safe. The first reflex when you install an Android application is to check its permissions. Why a game should have access to your full addressbook and be allowed to send SMS or perform calls? This looks suspicious!
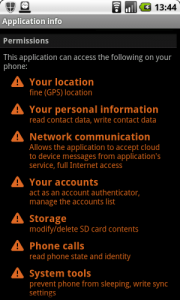
But what about the example of a small game requiring Internet access? This could seems legit to allow communications to the outside world: To upload scores, to download new maps or levels. But “Internet access” is very (too?) broad. Are you sure that some data could not be leaked? The only way to test the Internet traffic generated is to install the application on a test device and sniff your Wireless traffic… Easy if you are a techie! Otherwise, install the app and cross your fingers?
I won’t discuss here the process of malware analysis… Just a reminder: you have two major ways to do this: the static or behavioral analysis. With the first one, you analyze the provided binary and try to guess how it works (ex: by doing reverse-engineering). In the second one, you execute the code and collect as much information as possible like files accessed/created, DNS requests, network traffic, etc. This is performed in a safe environment (a sandbox).
For a while, there exists solutions to perform like a life analyze of regular (read: “for Wintel architecture“) pieces of malware. Some are commercial, others are open source (like Cuckoo). But what about Android applications? nViso, a young company founded by a group of Belgian Infosec professionals/enthusiasts, is working on a project called “Apkscan“. APK is the file format used to distributed Android applications. Yesterday, during a SANS@Night session in Brussels, Daan Raman demonstrated his tool:
As you can see it uses the same phylosophy as regular malware analysis tools: You submit a suspicious file, it executes it and generates a nice report. Both static and behavioral analyzis are performed. The report contains a static analyze, the permissions extracted from the Android manifest XML file, a Virustotal output, URLs found and behavioral analyze. The tool is still being developed but works quite well. I had the opportunity to submit some samples. Check out the two generated reports (a good and a bad one). The tool should be made publicly available soon. Great job!

It got stuck in the “Analyzing package…” one time (worked OK w/ another file.
The drag & drop worked.
Uploading worked.
A little follow-up, we have just published our first Beta version of ApkScan, it’s available at http://apkscan.nviso.be.
Thanks for taking the time to write up this review! As you mentioned, APK Scan is still under development, but once we go “live” we will send you an update.
Thanks again!