 During my holidays, I finally took the time to finish to read the book “IT Inventory and Resources Management with OCS Inventory NV 1.02” which covers the application with the same name. Even if the inventory of devices connected to a network is primarily a system administration task, it has also one foot in the security field. By knowing the devices used in your organization, you can better respond to potential threats.
During my holidays, I finally took the time to finish to read the book “IT Inventory and Resources Management with OCS Inventory NV 1.02” which covers the application with the same name. Even if the inventory of devices connected to a network is primarily a system administration task, it has also one foot in the security field. By knowing the devices used in your organization, you can better respond to potential threats.
The book takes the reader by the hand from the installation steps, the deployment of the agents and the web interface to the maintenance and debugging of complex configurations. The first chapters are quickly read: what are the benefit of systems inventory (who still doubts of them?) and how to install the application. OCS is a classic LAMP application, no big issue. Note that it can also be installed on a Windows platform using XAMPP.
The next chapters covers the agents. They are the critical components of the architecture as they will collect the following informations from the hosts: Hardware, BIOS, Processors, Memory, Video, Storage, Network, I/O (keyboard, mouse, ports), Sofware, OS, Installed software, Custom registry entries (for Windows agents). They must perform an effective job without being too invasive in terms of resources usage.
Agents are deployed on the target devices using multiple paths but they also offer an auto-discovery feature. They can detect hosts not yet inventoried. This process is based on Nmap. About the installation, it’s important to keep in mind the following points:
- Agents use HTTP(S) to communicate with the server
- Agents keep a local copy of the grabbed data using XML files
- Agents always initiate the communication with the server (this allow agents to be deployed behind NATed networks)
- Windows agens run under the “LocalSystem” account.
The deployment is an important topic. There are multiple methods available (depending on the target Operating System): Manually (using a “next-next-finish” method), via a GPO, via login scrip, via PsExec.
On Linux systems, it is performed locally or via remote access (SSH). Note that installation can be performed with or without user interaction. Other supported systems are: Apple computers (MacOS) and mobile devices (Windows Mobile or Java). There is also a export/import procedure to collect data from non-networked agents or agents not directly reachable.
On Windows hosts, an interesting feature is the ability to track certain registry keys. Very useful to track non-standard activities or specific software configurations on remote hosts. Once deployed, the agents will collect the informations and send all the stuff to the central server.
The following chapter will cover the web GUI, how to work with the collected data and how to broaden the OCS Inventory Management with other tools like GLPI for advanced features like reporting and ticketing system. Finally, the last chapters will review how to fine-tune and debug your environment.
The book is accessible to all readers. Implementing an inventory solution is not very difficult from a technical point of view but how to extract the real-value of the collected data? From to a security point of view now. Several useful information can extracted from the database:
- What are the operating systems and versions used in the organization
- What is the software base installed
- IP settings : is there a rogue DNS or gateway used?
Those collected information might be very useful to track suspicious devices. The primary usage of OCS Inventory Manager is to collect information in a “read-only” fashion. But the ability to deploy packages through the installed agents is an interesting feature. Example to deploy security patches or to deploy new configurations. This is covered by a dedicated chapter. A complete overview of the features is presented in a nice poster on the application website:
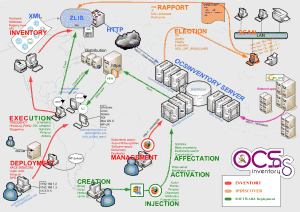
Related link: