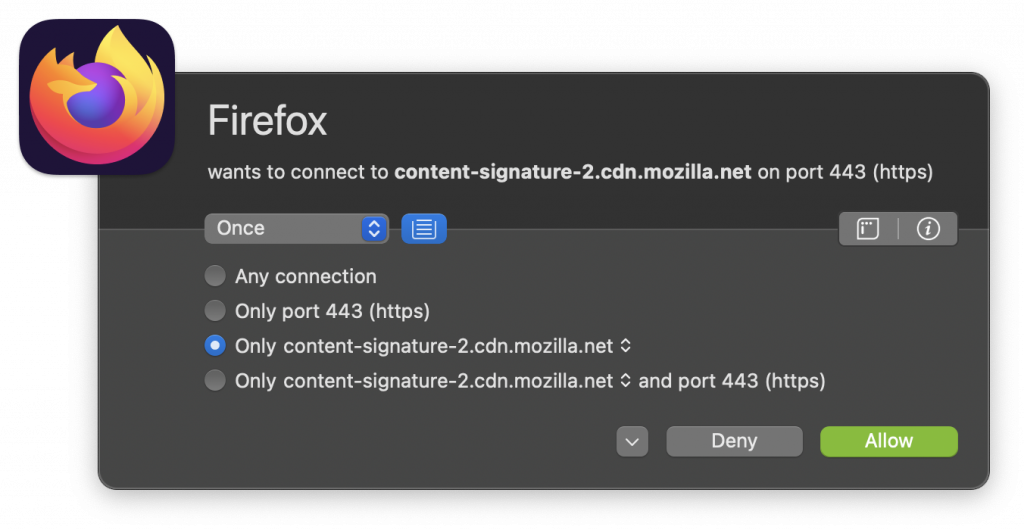
Today, I published the following diary on isc.sans.edu: “macOS: Who’s Behind This Network Connection?“:
When you must investigate suspicious behavior or work on an actual incident, you could be asked to determine who’s behind a network connection. From a pure network point of view, your firewall or any network security control device/app will tell you that the source is the connection is host « A », « B » or « C ». But investigating further how to discover who or which process is the source of the connection (now, at the operating system level)… [Read more]