Ghidra is a very nice disassembler developed by the NSA. When they released it, the tool became very popular amongst the security community thanks to its power and a huge list of features (that some competitors included with extra licenses – like the pseudo-code generator). Ghidra is also the default disassembler used in the SANS FOR610 training (reverse engineering and malware analysis).
The idea behind this plugin is to avoid losing time with the basic analysis of the sample and to focus on interesting code blocks. The plugin uses the Intezer’s API to collect information about the sample (it must have been submitted to the Intezer’s sandbox first). Then, the Ghidra plugin will provide you a list of functions identified as shared with other malware samples or tools.
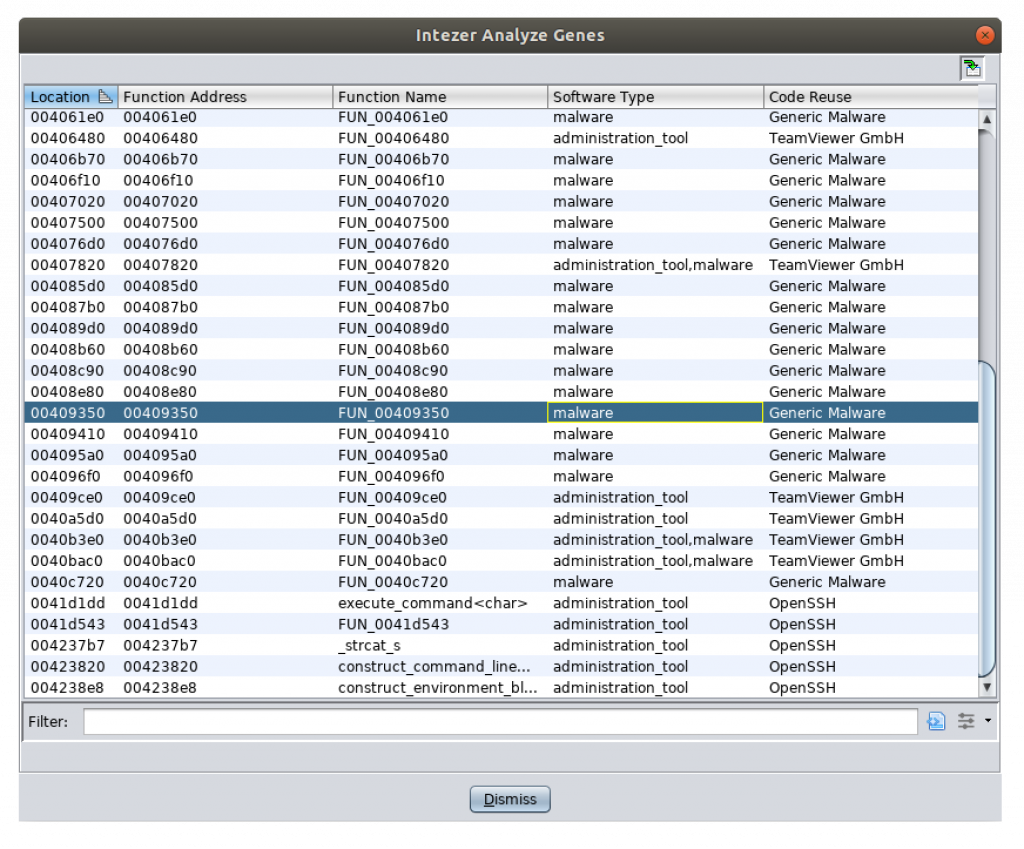
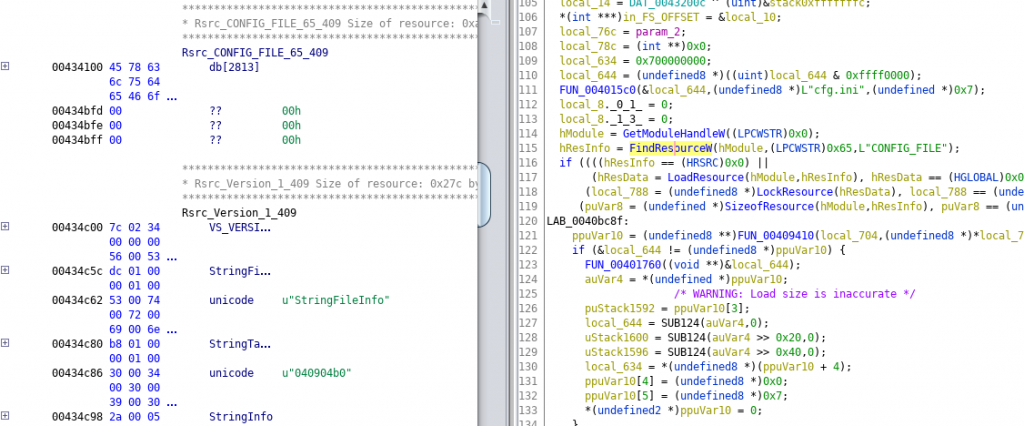
Just browse the functions identified as “reused” and you can jump directly into the code to see what they do. This is also a great way to learn how malware behaves. In the following example, you can find a classic set of API calls to read a configuration from the resource in the PE file:
- FindResource()
- LoadResource()
- LockResource()
- SizeOfResource()
I had some issues installing the plugin on my Ubuntu 18.04-LTS VM that I use to run my Ghidra setup. So, I’d like to share some setup steps with you.
There is a problem with the Python requests module installed in Ubuntu (the official package). I had to remove the official module (2.18.4) and install an older version via PIP:
root@ubuntu:/# dpkg -r python-requests
root@ubuntu:/# pip install requests==2.7.0
(Note that you could have some dependencies with the python-requests package, be careful when removing it!)
The next step is to add the local repository of Python modules in the plugin script (intezer_analyze_gh_community.py):
if os.name == "posix":
sys.path.append('/usr/lib/python2.7/dist-packages')
sys.path.append('/usr/local/lib/python2.7/dist-packages')
else:
sys.path.append('C:\Python27\lib\site-packages')
Then, the plugin will work smoothly! Happy reversing!

One comment