BruCON 0x09 is over! It’s time to have a look at the data captured during the last Thursday and Friday. As the previous years, the setup was almost the same: An Internet pipe with a bunch of access-points, everything interconnected through a pfSense firewall. The guest network (dedicated to attendees) traffic is captured and processed by a SecurityOnion server + basic full packet capture. We also used our classic wall-of-sheep to track the web browsing activity of our beloved visitors.
Let’s start with a few raw numbers. With the end of the 3G/4G roaming costs in Europe since June, most European visitors avoid the usage of wireless networks and prefer to remain connected via their mobile phone. In a few numbers:
- 206 Gigabytes of PCAP files
- 50.450 pictures collected by the wall-of-sheep
- 19 credentials captured
- 500+ unique devices connected to the WiFi network
- 150 PE files downloaded (Windows executables)
- 3 blocked users
- 1 rogue DHCP server
We saw almost the same amount of traffic than the previous years (even if we had more people attending the conference!). What about our visitors?
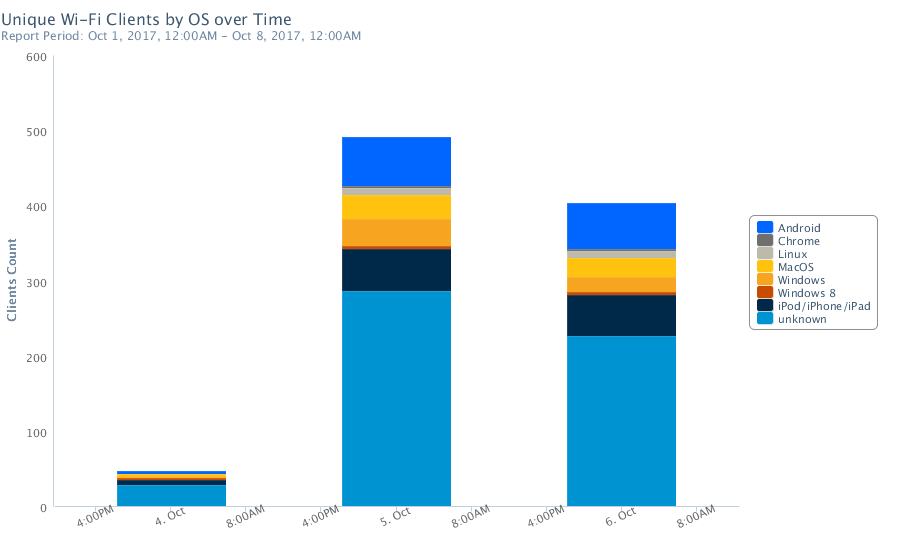
Strange that we had some many “unknown” device. Probably due to an outdated MAC address prefixes databases.
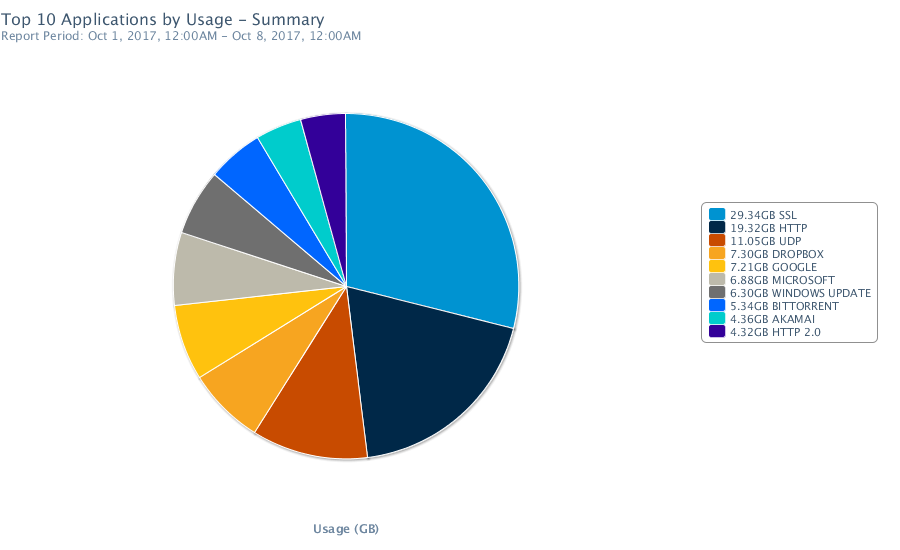
Good to see that SSL is the top protocol detected! UDP reached the third-position due to the massive use of VPN connections. Which is also good!
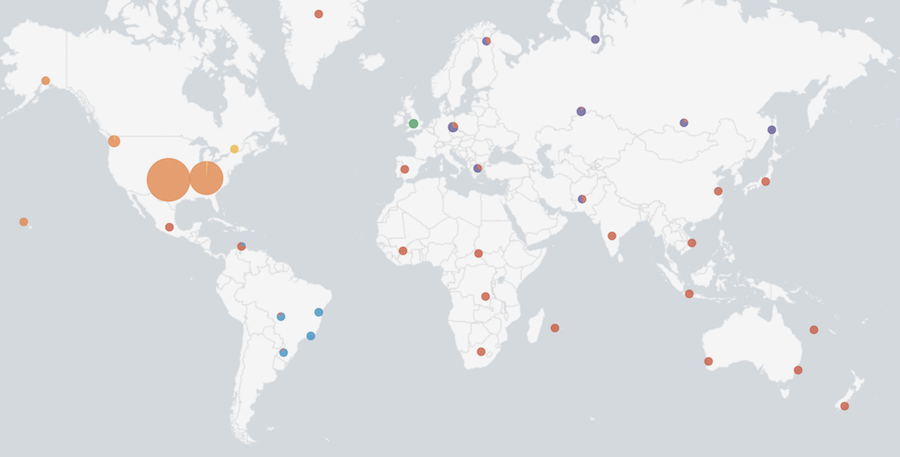
Our visitors communicated with 118K+ IP addresses from all over the word:
Here is the top-20 of DNS requests logged:
|
Rank |
FQDN | Hits |
|
1 |
api.dataplicity.com |
59310 |
|
2 |
www.google.com |
20097 |
|
3 |
softwareupdate.vmware.com |
9050 |
|
4 |
auth.gfx.ms |
6766 |
|
5 |
swscan.apple.com |
6706 |
|
6 |
v10.vortex-win.data.microsoft.com |
5300 |
|
7 |
www.googleapis.com |
5252 |
|
8 |
www.icanhazip.com |
4402 |
|
9 |
www.google.be |
3831 |
|
10 |
clients4.google.com |
3721 |
|
11 |
play.google.com |
3562 |
|
12 |
win10.ipv6.microsoft.com |
3459 |
|
13 |
outlook.office365.com |
3267 |
|
14 |
ssl.gstatic.com |
3130 |
|
15 |
settings-win.data.microsoft.com |
3111 |
|
16 |
pingsl.avast.com |
2884 |
|
17 |
safebrowsing-cache.google.com |
2841 |
|
18 |
avast.com.edgesuite.net |
2533 |
|
19 |
graph.facebook.com |
2164 |
|
20 |
0x13.nl |
1990 |
As most of the traffic captured was web-based, I had a look at the different tools/applications used to access web resources. Here is the top-20:
|
Rank |
FQDN |
|
1 |
Firefox |
|
2 |
Chrome |
|
3 |
Microsoft-CryptoAPI |
|
4 |
Microsoft |
|
5 |
Safari |
|
6 |
Dalvik |
|
7 |
trustd |
|
8 |
MSIE |
|
9 |
cloudd |
|
10 |
Debian |
|
11 |
Windows-Update-Agent |
|
12 |
iPhone |
|
13 |
Unspecified |
|
14 |
Microsoft-WNS |
|
15 |
CaptiveNetworkSupport |
|
16 |
serer-bag |
|
17 |
MICROSOFT_DEVICE_METADATA_RETRIEVAL_CLIENT (1) |
|
18 |
Spotify |
|
19 |
Unknown |
|
20 |
Microsoft-Delivery-Optimization |
(1)Â https://docs.microsoft.com/en-us/windows-hardware/drivers/install/device-metadata-retrieval-client
I uploaded the 200+ gigabytes of PCAP data into my Moloch instance and searched for interesting traffic. What has been found:
- One visitor polled his network devices (172.16.x.x) during the two days (5995 SNMP connections detected)
- Two visitors performed RDP sessions to two external IP addresses
- Two visitors generated SIP (VoIP) traffic with two remote servers
- 29 remote IMAP servers were identified (strange, no POP3! 🙂
- SSH connections were established with 36 remote servers (no telnet!)
Finally, our wall-of-sheep captured web traffic during the whole conference:
Of course, we had some “p0rn denial of service attacks” but it’s part of the game right? See you for the 0x0A (10th edition) next year with, crossing fingers, more fun on the network!


One comment