If you follow my blog for a while, you probably noticed that I’m not really active with new content. Most articles are published through the SANS ISC Website but it does not mean I don’t have content to publish. It’s just a question of time like many of us!
Recently, I listened to an interesting conversation in a SOC (“Security Operation Center“). The topic was about assigning more development time to the SOC engineers to process the number of pending alerts. In a SOC, it’s important to rotate tasks across available people like first-line, ongoing investigations, hunting, and… development/maintenance of the platform (tools, processes, playbooks, etc)
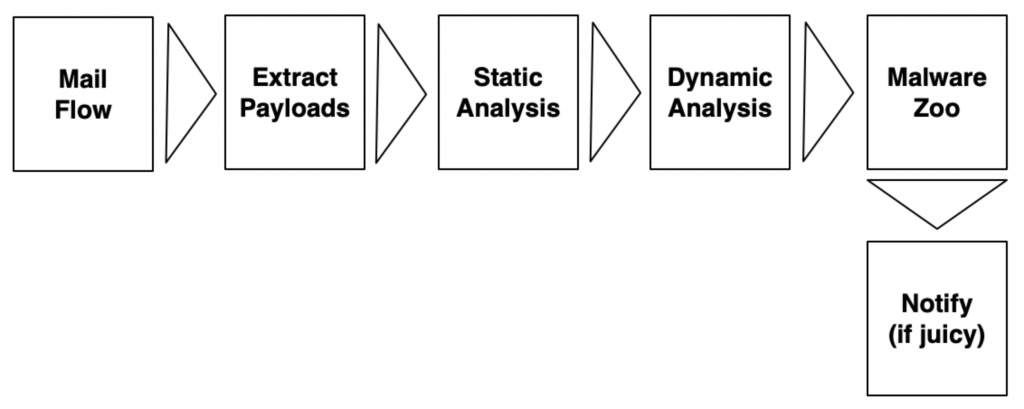
About automation, it’s a key element in processing data collected by the SOC. We are all lazy people and recurrent tasks are boring to perform. After all, we are facing huge amounts of data generated by computers, why not use computers to handle it? I like “automation”! I like the fact that you can automate everything to, while drinking your morning coffee, review what has been processed during the night and, more important, what deserves more investigation. A perfect example of this process is malware triage. You collect samples from multiple sources, parse them, extract the payload, perform basic checks, label it, and notify only if something “juicy” is detected:
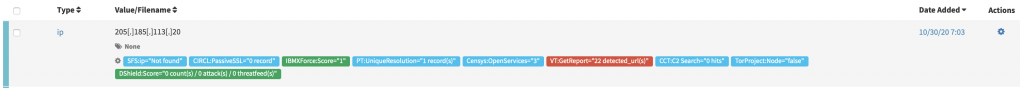
Another scenario to implement more automation is the processing of “Alerts”. When an alert is received, you have to acknowledge it and start investigating it. Let’s take a practical example with TheHive, a popular tool used in SOCs. When an alert is received and relevant, a case is created with many observables (IP addresses, hashes, domains, files, etc). The key feature of TheHive is the link to Cortex instance that allows us to search for observables across a long list of analyzers that query online services. For example, an IP address will be tested against blocklists, passive DNS services. The first automation that can be implemented here is to automatically run analyzers against freshly added observables. TheHive can do this perfectly through webhooks. Great! When the SOC engineer opens the case, observables have already been enriched:
This kind of automation is nice because it speeds up the investigations, optimizes the engineer’s time, and avoids “fatigue”.
Problems arise when an extension of automation is suggested to face a (too) huge amount of data to process. If you need more automation to process alerts received daily in your SOC then you’re facing an issue. If you have one rule in your SIEM that generates 150 alerts/day (just an example), the rule is probably not optimized and should be reviewed.
Do we need to automate or to reduce the noise? Both! Automation is a key point and must be used but the noise reduction must be applied as soon as possible in the data flow. Automation should not be used as a counter-measure to manage a flood of alerts…