When you need to quickly investigate a suspicious computer located thousands of kilometers away or during a pandemic like we are facing these days, it could be critical to gain remote access to the computer. Just to perform basic investigations. Also, if the attacker did a clever job, he could be monitoring processes running on his/her target. In this case, you should prevent to use of classic remote management tools like VNC, TeamViewer, etc.
The following computer is running a LanDesk process which indicates that it can be controlled remotely:
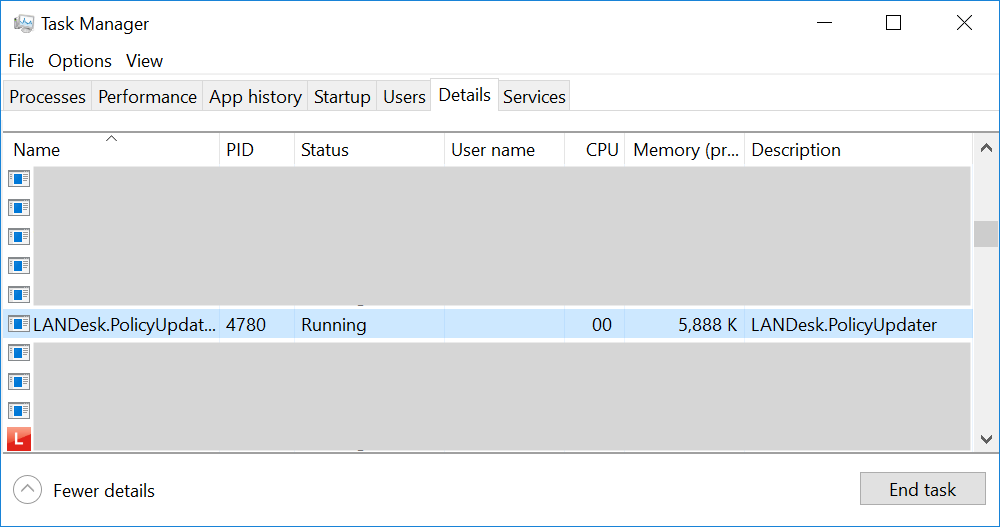
Also, if the suspicious computer is potentially under the control of the attacker, it could be interesting to not ring a bell by using classic tools. Today, web conferencing tools are very popular. Why not use them to gain remote access to start your investigations?
Via Zoom (but the feature is available via other tools), any participant to a web conference can share his/her screen but also transfer the control (mouse & keyboard) to a specific participant:
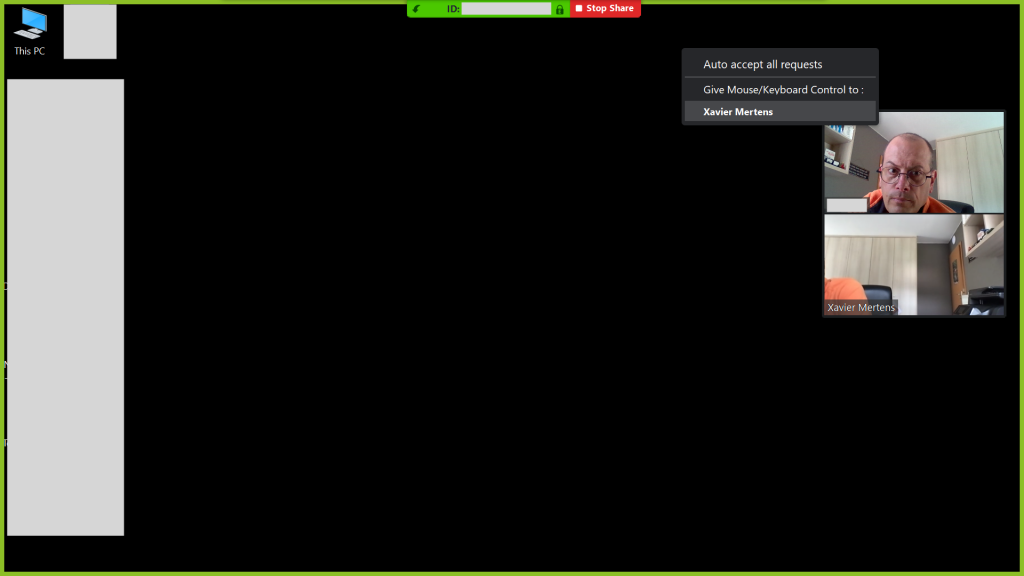
Now, you can download your favourite tools (events collector, memory dumper, etc)… This technique has many advantages:
- No need to reconfigure a firewall to allow incoming connections
- There are chances that the web conferencing tool is already installed
- From a forensic point of view, this has a small footprint: no new login events on the computer, no changes applied to the investigated computer.
- You gain the same rights as the connected user (which can already be ‘administrator’ rights in some (bad) cases.
Back on Zoom, the free subscription limits the conference duration up to 40 minutes but it’s enough to launch some tasks on the remote computer. If the meeting is aborted, just restart a new one. Everything you launched will keep running…

One comment