This BruCON edition (also called “0x0B”) is already over! This year, we welcomed more than 500 hackers from many countries to follow wonderful speakers and learn new stuff with practical workshops. Like the previous editions, I played with the network deployed for our attendees. Here is a short debriefing of what we did and found during the conference.
Basically, from an infrastructure point of view, nothing really changed. The same hardware was deployed (mainly wireless access for the attendees and wired network for specific purposes. We welcome the same number of attendees and we see every year more and more people trying to avoid wireless networks. Furthermore, all European travellers benefit now of the free data roaming across Europe. Also, the trend is to use encrypted traffic (SSL or VPNs), which means less “visible” traffic for us (No, we don’t play MitM 😉
First of all, we launched our wall-of-sheep like every year. It remains a very nice security awareness tool. New attendees ask me always how it works or “what’s behind the magic”. Of course, some dumb people keep trying to flood it with p0rn pictures. We used the same technology to reduce the number of offending pictures but it’s not bullet-proof. [Personal opinion: if you spent your time flooding the WoS with p0rn, you completely missed the point of a security conference… that to say!]
If we don’t play MitM, it does not mean that we don’t inspect most of the flows passing by our network. This is clearly stated on the website and the brochure. The first change that we implemented this year was an intercepting proxy to collect all URLs visited by our beloved attendees. Last year, we detected that many corporate laptops were trying to find WPAD files but we needed more data. Here are some stats about the proxy:
- 274K HTTP requests (GET, POST or CONNECT)
- 39K unique URL
What about the top-visited URLs? No Facebook etc this year, but many many (read: “way too many”) automatic updates URL! Many applications or systems still check and download their updates via HTTP! When you see how easy it is to manipulate this kind of traffic, it scares me. Bad practice: Do NOT enable automatic updates while connected to wild environments.
What about DNS traffic? Here again, we slightly changed the configuration. Many people don’t trust DNS provided by DHCP and use their own DNS or a public one (Google to the rescue with 8.8.8.8!). Blocking all DNS traffic to “force” people to use our own was nice but too intrusive. This year, we allowed all traffic but intercepted all UDP/TCP/53 traffic and port-forwarded it to our firewall. This way, people did not see that the DNS traffic was redirected to our own resolver. It was also an easy way to block some malicious or unwanted websites.
Here is the top-10 of resolved domains (without noisy and local domains like the ones used by the CTF):
| Query | Count |
| coldchilli.de | 15346 |
| softwareupdate.vmware.com | 11730 |
| www.google.com | 9672 |
| api.twitter.com | 8197 |
| auth.gfx.ms | 7962 |
| swscan.apple.com | 7955 |
| ipinfo.io | 4032 |
| twitter.com | 3698 |
| http.kali.org | 3582 |
| ftp.belnet.be | 3504 |
About DNS, we saw some DNS tunnelling and, for the first time, some DoH traffic! (DNS over HTTPS). Ok, only two different clients but it’s a sign!
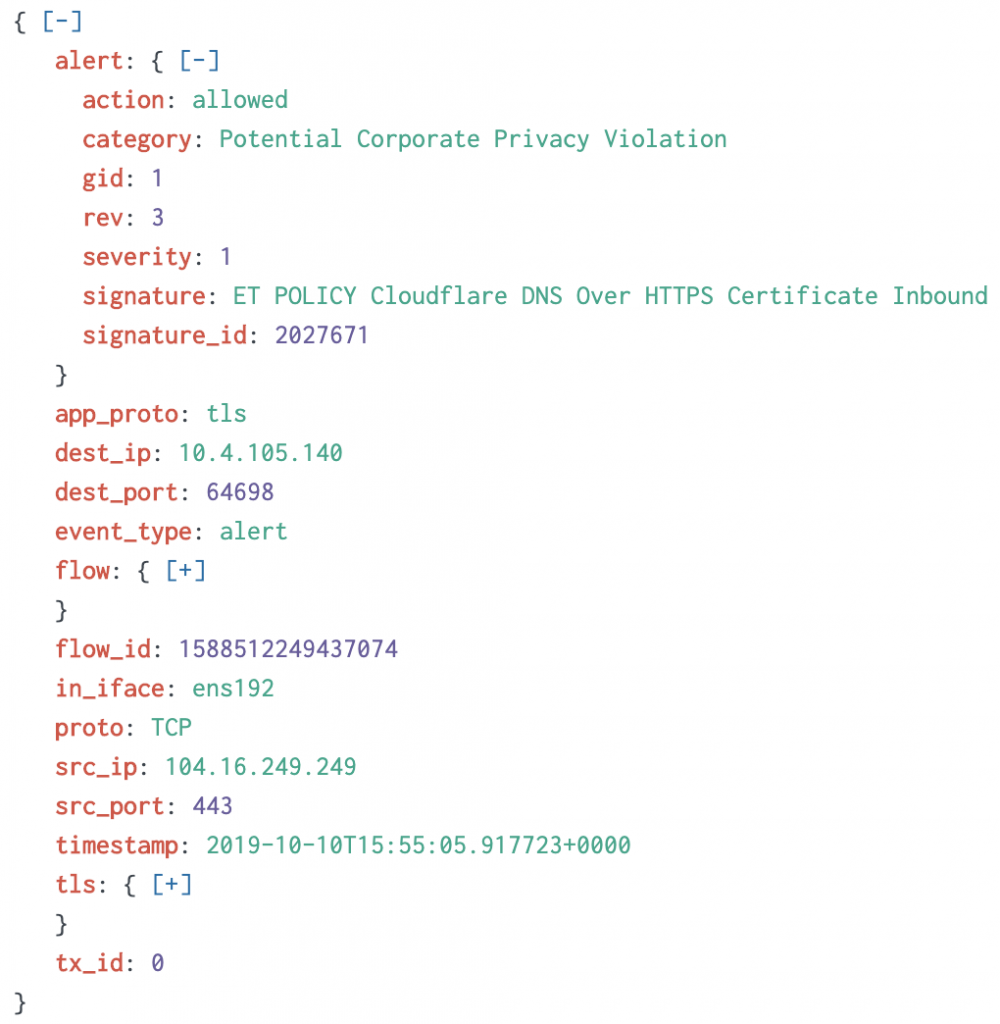
Also, we collected interesting files transferred via HTTP:
| Mime-Type | Count |
| HTML | 161391 |
| PNG | 26772 |
| Text | 20706 |
| Jpeg | 14003 |
| JSON | 6968 |
| XML | 5729 |
| Gif | 3744 |
| ZIP | 365 |
| JS | 168 |
| Exe | 116 |
| PHP | 14 |
| BMP | 7 |
| Doc | 2 |
| SWF | 1 |
| Unknown | 42258 |
About communications & chat, we detected IRC, Google Talk (both in clear text!), Skype & Teams.
We detected some juicy traffic which looked very suspicious but… it’s was just a guy testing a potential 0-day 🙂
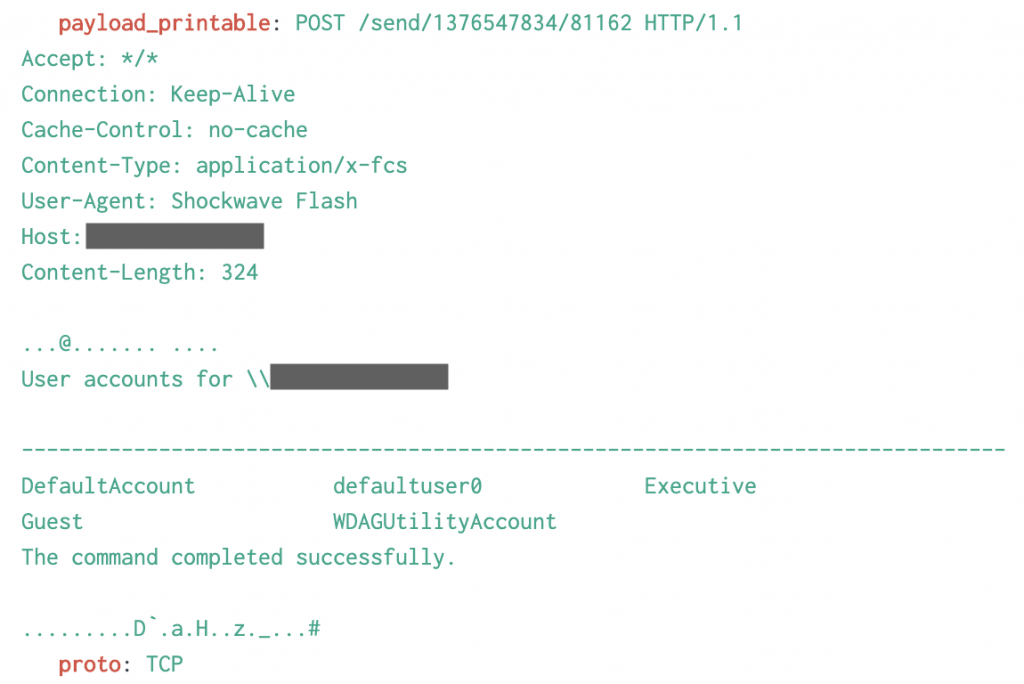
About the logging capabilities, this year, we collected in real-time all data and indexed them into a Splunk instance. This is much more convenient when you need to investigate urgently an incident. We had to track a “bad guy” and he was discovered within a few minutes based on the MD5 of the downloaded picture! (I mean we discovered his MAC address and the device name).
To conclude, some extra numbers:
- 3 Internet access lines (load-balanced)
- 171GB downloaded
- 847 devices connected to the network
- 504 badges connected
- 28515 pictures collected by the WoS
- 282.244 collected files:
- 898.638 DNS requests
- 2.757.669 collected flows
- 274K HTTP requests
- 101.457 IDS events
- 52 blocked p0rn sites
- 4 network gurus 🙂
We are ready for the next editions and, based on what we learned, we already have nice ideas…
