Last week, I had a unique opportunity to attend a demo of a “cool” product (I insist on the quotes around cool): A complete solution to track and intercept mobile devices. The company presents itself as a partner of law enforcement services, governments or special agencies (you know all the fancy 3-letters acronyms). They demonstrated how easy they are able to track people based on their mobile phones (passive). But, they also demonstrated how easy they can take actions (active) against the same people: blocking the mobile and preventing connections, draining the battery, interception of calls, SMS. But also injection of SMS and calls (spoofing). I won’t disclose more details of course.
My knowledge of mobile networks being very low, I tried to search for more information on the web. The solution used to track people is called an “IMSI Catcher“. What does mean “IMSI”? The “International Mobile Subscriber Identity” is stored in a 64-bits field and uniquely identifies a user on a mobile network. The ID is provisioned on the SIM card and, as you can imagine, it is extremely sensitive and must be protected. IMSI are usually represented by 15 digits: “xxx xx xxxxxxxxxx”. The first block represents the country (Mobile Country Code or MCC), the second block is the operator (Mobile Network Code or MNC). The remaining block is the Mobile Subscription Id Number (MSIN). Here is an example:
206 05 00043XXXXX
“206” is Belgium, “05” is Telenet (a Belgian operator).
While searching for more information, I found a project on GitHub called IMSI-Catcher. From an hardware point of view, it just requires a SDR device. Cool, I have a low-cost SDR dongle lying in my lab. Let’s try the tool. My SDR device is fully passive (no injection of data) and does not allow to listen to very high frequencies so I was limited to the 2G or 900MHZ range. I won’t cover the installation steps, just follow the tutorial available on the GitHub page. Once my VM ready, I started to sniff at home and collected a very low amount of data because I’m living in the country-side.
During the last two days, I was at a better location and results were much more impressive: 4473 unique IMSI collected! Ok, nice but what can we do with the data? First of all, there is no way to track people because it’s not possible to make a link between an IMSI and the mobile phone owner. It’s just like listening to the radio. However, we can deduce interesting information: IMSI from 40 different countries have been detected:
(Note: for a better readability, Belgium has been removed)
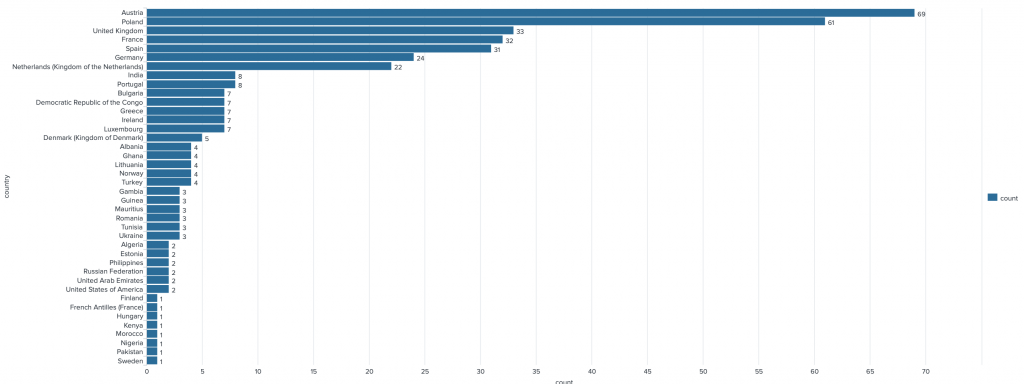
We can find mobile devices that are more often detected:
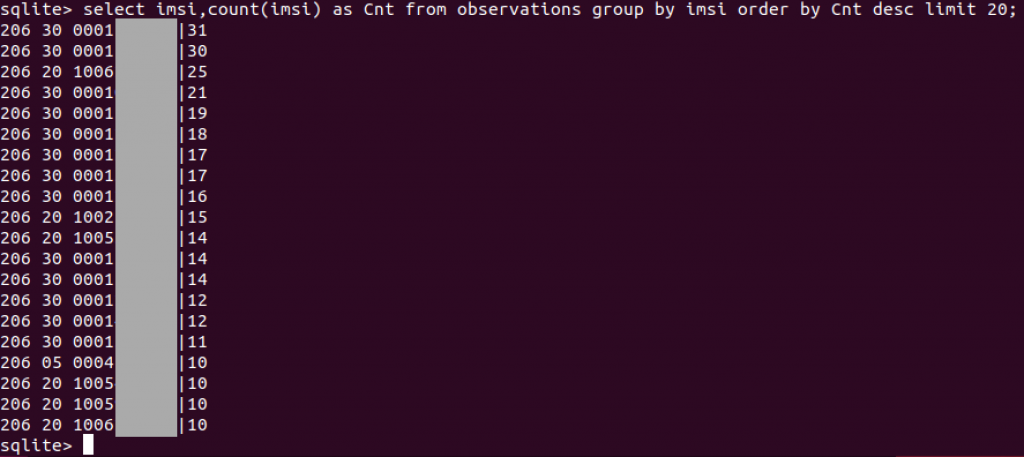
Just imagine that your business is very sensitive and that you’re afraid of some people who could try to spy on you. It could be valuable to know that a mobile device from country “x” has been detected in the area. You can track the behaviour of the same IMSI: what if it is detected every x minutes/hours or every day around the same time? If you, by one mean or another, get the IMSI number of somebody (I don’t want to know how ;-), it becomes very easy to spot the presence of this person in the area. This has a complete different impact on privacy!
The purpose of this blog post is just to demonstrate that we all have spying devices in our pockets! If you were not yet aware…

Thank for sharing the link, interesting to read!
The IMSI is not directly correlatable to an individual, but it is definitely PII: if you have a network of multiple IMSI catchers in different locations, it’s trivial to identify people with 80% accuracy:
http://www.cs.umd.edu/~mwh/papers/GraphInfoFlow.CCS2012.pdf