Passive DNS is not a new technique but, for the last months, there was more and more noise around it. Passive DNS is a technique used to record all resolution requests performed by DNS resolvers (bigger they are, bigger they will collect) and then allow to search for historical data. This is very useful when you are working on a security incident. By example, to track the different IP addresses used to host a C2 server.
But Passive DNS can also be very helpful on the other side: offensive security! A practical example is always better to demonstrate the value of passive DNS. During an engagement, I found a server with ports 80, 443 and 8080 publicly available. The port 8080 looks juicy because it could be a management interface, a Tomcat or? Who knows? Helas, there was no reverse DNS defined for the IP address and, while accessing the server directly through the IP address, I just hit a default page:
You probably recognised the good old default page of IIS 6.0 but it’s not so important here. The problem was the same on port 8080: an error message. Now, let’s search for historical data about this IP address. That is where Passive DNS is helpful. Bingo! There were three records associated with this IP. Let’s retry to access the port 8080 but now through a vhost: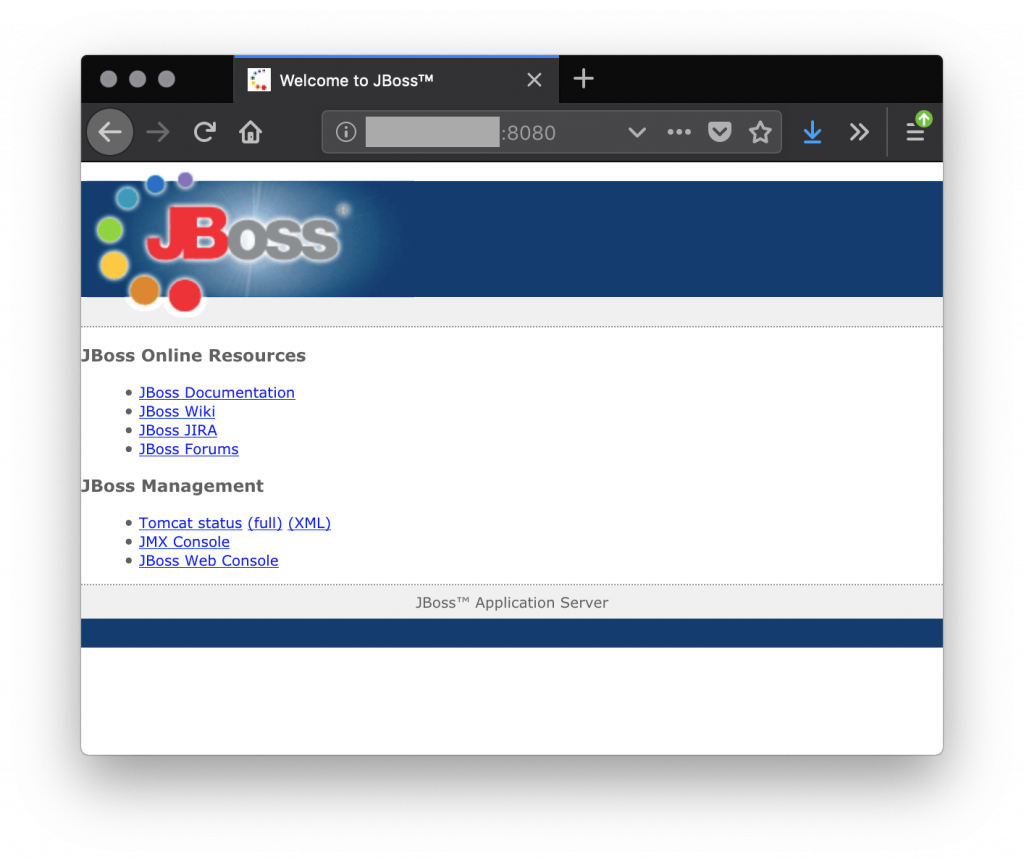
This looks much more interesting! We can now go deeper and maybe find more juicy stuff to report… When you scan IP addresses, always query then against one or more Passive DNS databases to easily detect potential websites.
How to protect against this? You can’t prevent your IP addresses and hostnames to be logged in Passive DNS databases but there is a simple way to avoid problems such as the one described above. Keep your infrastructure up-to-date. Based on what I found and the Passive DNS data, this server is an old one. The application has been moved for a while but the vhost and the application were still configured on the old server…
