Everybody still reminds the huge impact that Wannacry had in many companies in 2017? The ransomware exploited the vulnerability, described in MS17-010, which abuse of the SMBv1 protocol. One of the requirements to protect against this kind of attacks was to simply disable SMBv1 (besides the fact to NOT expose it on the Internet ;-).
Last week, I was trying to connect an HP MFP (“Multi-Functions Printer”) to an SMB share to store scanned documents. This is very convenient to automate many tasks. The printer saves PDF files in a dedicated Windows share that can be monitored by a script to perform extra processing on documents like indexing them, extracting useful data, etc.
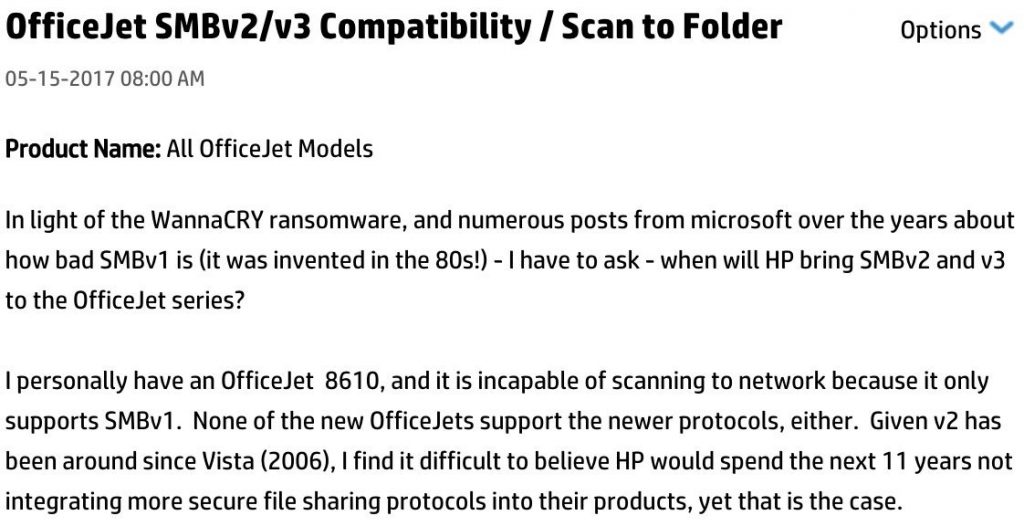
I spent a long time trying to understand why it was not working. SMB server, ok! Credentials, ok! Permissions on the share, ok! Firewall, ok! So what? In such cases, Google remains often your best friend and IÂ found this post on an HP forum:
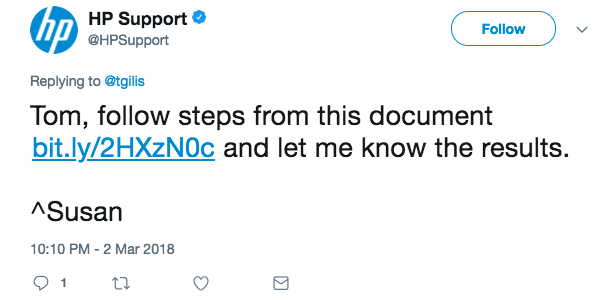
So, HP still requires SMBv1 to work properly? Starting with the Windows 10 Fall Creators update, SMBv1 is not installed by default but this can lead to incompatibility issues. The HP support twitted this:
The link points to a document that explains how to enable SMBv1… Really? Do you think that I’ll re-enable this protocol? HP has an online document that lists all printers and their compatibility with the different versions of SMB. Of course, mine is flagged as “SMBv1 only”. Is it so difficult to provide an updated firmware?
Microsoft created a nice page that lists all the devices/applications that still use SMBv1. The page is called “SMB1 Product Clearinghouse” and the list is quite impressive!
So, how to “kill” an obsolete protocol if it is still required by many devices/applications? If users must scan and store documents and it does not work, guess what will the average administrator do? Just re-enable SMBv1…

One comment