The eighth BruCON edition is already over! Don’t expect a wrap-up because I just don’t have time. I’m always keeping an eye on the attendees’ bits & bytes! Based on the first feedback that I received from attendees and speakers, it was another good edition but, from a network point of view, it was harder. Indeed, the venue does not provide any network service at all and we have to build a temporary network from scratch. The ISP which provides us the pipe to the Internet was not able to help us and we had to find an alternative. We found one but it was extremely expensive for us (keep in mind that BruCON is a non-profit organization) and, worse, the quality was not present. When we deployed the network, we had only 25% of the ordered bandwidth (ouch!). The ISP installed in emergency a backup line via a 4G connection and I spend an half-day configuring the load-balancing between the two lines and some QoS to prioritize traffic. At certain times, we had up to 15% of packets lost on the main link… Our apologies for the bad network quality! Hopefully, more and more people don’t trust wireless networks and use their mobile phones or portable access points to access the Internet.
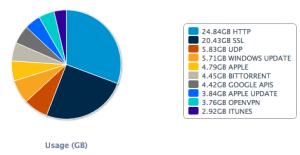
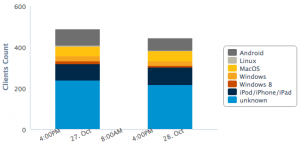
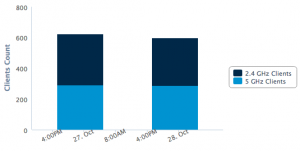
First some high level stats about the network usage:
About the traffic, we collected 193 GigaBytes of PCAP files. 528 unique devices (based on their MAC addresses) connected to the wireless and got an IP address. We did not play MitM to inspect encrypted protocols (we respect your privacy). Editions after editions, we see that more and more people are using VPN, which is good! Here is the top-20 of MIME types detected:
| Count | MIME Type |
| 1034509 | application/pkix-cert |
| 94885 | text/plain |
| 74707 | text/html |
| 61321 | image/jpeg |
| 34892 | image/png |
| 31268 | image/gif |
| 20709 | text/json |
| 19209 | application/ocsp-response |
| 14323 | application/ocsp-request |
| 9370 | application/xml |
| 5054 | application/vnd.ms-cab-compressed |
| 4304 | application/javascript |
| 2717 | application/x-debian-package |
| 2250 | application/font-woff |
| 1761 | image/svg+xml |
| 1734 | image/x-icon |
| 1608 | application/x-gzip |
| 675 | video/mp4 |
| 675 | application/zip |
| 519 | application/x-bzip2 |
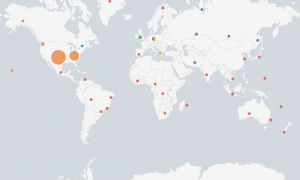
Our attendees communicated with 115.930 uniques IP addresses from the wild Internet. Here is a global map:
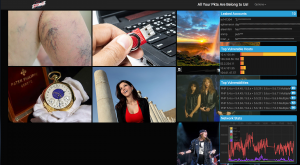
Of course, we had our wall of sheep running to collect all pictures and interesting credentials. If our attendees use VPN connections, some of them regularly fail to protect their network communications.
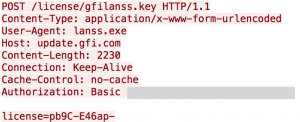
We collected 68848 images and 119 credentials. Amongst the classic IMAP or SNMP accounts, we found that some security products are not so secure by default. Two attendees were running the GFI LANguard tool which communicates over HTTP with the central servers:
About DNS requests, 129883 unique A requests were performed. Here is the top-30 of hosts queried:
| Count | FDQN |
| 119314 | google.com |
| 93601 | brucon.org |
| 90383 | t.co |
| 57564 | apple.com |
| 42841 | microsoft.com |
| 29479 | facebook.com |
| 27399 | vmware.com |
| 27043 | g.co |
| 27038 | softwareupdate.vmware.com |
| 23418 | capgemini.com |
| 22252 | gstatic.com |
| 21127 | dns.msftncsi.com |
| 20532 | www.google.co |
| 20425 | www.google.com |
| 19952 | wall.brucon.org |
| 19405 | pool.ntp.org |
| 19375 | push.apple.com |
| 18844 | auth.gfx.ms |
| 16919 | live.com |
| 14999 | twitter.com |
| 13942 | avast.com |
| 13443 | zabbix.countercept.mwr |
| 12814 | dropbox.com |
| 11006 | www.googleapis.com |
| 10680 | doubleclick.net |
| 10346 | nucleus.be |
| 9952 | teredo.ipv6.microsoft.com |
| 9863 | google.be |
| 9706 | sz.local |
| 9205 | corp.capgemini.com |
Interesting top queries: WPAD, AD, ISATAP. WPAD is amazing, so easy to be abused to play MitM. Some samples detected:
wpad, wpad.hogeschool-wvl.be, wpad.nl.capgemini.com, wpad.corp.capgemini.com, wpad.home, wpad.howest.be, wpad.brucon.org, Â wpad.be.capgemini.com, wpad.capgemini.com, wpad.bnl.capgemini.com, Â wpad.capgemini.be, wpad.capgemini.nl, wpad.fantastig.lan , wpad.webde.local, wpad.eu.thmulti.com, wpad.soglu.internal, wpad.ctg.com, wpad.sogeti.be, wpad.united.domain, wpad.fictile.lan, wpad.telenet.be, wpad.eu.didata.local
The DNS traffic remains one of my favorite source of intelligence! Many devices are corporate ones and keep constantly trying to “phone home”. Here is a list of companies that were present (well, their devices) at BruCON:
- Cap Gemini
- Ernst & Young
- Sogeti
- PWC
- ING
- CTG
- Hogeschool West-Vlaanderen
- MWR
- Nucleus
- Limes Security
It’s always interesting to extract the download PE files. We captured 268 unique PE files. Not really malicious but some of them were really suspicious. We detected the following signatures:
- 5 x Win32.Trojan.WisdomEyes.16070401.9500.9997
- 1 x Trojan.Agentb.akq
- 2 x Win32/Bundled.Toolbar.Google.D potentially unsafe
- 1 x Posible_Worm32
- 1 x Win32.Application.OpenCandy.G
- 1 x Trojan-Clicker.Win32.Agent!O
A special mention to the guy who downloaded a malicious ‘BitTorrent.exe’ (22bc69ed880fa239345d9ce0b1d12c62). Do you really need to download such files at a security conference?
From a security point of view, we did not face any incident. Only one device was blacklisted during the conference. As usual, some folks spent time to bring p0rn pictures on the wall of sheep. Besides the classic [smurf|avatar|manga|hulk] p0rn, we have a winner who used furnitureporn.com! Taste and colors are not always the same! 🙂
We already have nice and fun ideas to implement during the next edition. We will expect your packets again in 2017!

RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ
RT @xme: [/dev/random] Debriefing the #BruCON Network https://t.co/Qs8cZ5kPCJ