 Here is my wrap-up for the second day. Yesterday, we had a nice evening with some typical local food and wine then we went outside for a walk across the city of Nancy. Let’s go!
Here is my wrap-up for the second day. Yesterday, we had a nice evening with some typical local food and wine then we went outside for a walk across the city of Nancy. Let’s go!
Paul Rascagnères kicked off the second day with a workshop about WinDbg debugger and some useful tips. It started with Paul’s questions like “Who think it’s a good idea to speak about ASM/debugger/WinDBG at 9AM†or “Who think I need a costume?â€. It started with a joke and now Paul is expected to wear a nice costume during his talks. Challenge accepted again!
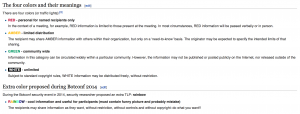
Starting the day with assembler code is not easy. For the fun, Paul proposed to use a new TLP code (“Traffic Light Protocolâ€) for this presentation: TLP:Rainbow. The Wikipedia page was changed but it was of course quickly rolled back to the previous version. Here is a screenshot of the updated version:
Then, he mentioned the singer Regine (who was born in Anderlecht – close to Brussels) and the recent Belgacom pwnage by the malware with the  same name. But enough jokes ad back to the topic: WinDBG. This is a Windows debugger that has powerful features but not easy to use. According to Paul, there are two majors issues: The layout and the built-in scripting language. The first problem can be solved by using plugins to reorganise the interface and the second one can be fixed by using pykb which adds Python support into the debugger. But don’t forget that it is prohibited to use  WinDBG in planes (real story). There are two ways to debug: live debugging (dynamic). A virtual machine can also be debugged live, Paul gave an example with VirtualBox configuration to achieve this. The second way is to use a Windows crash dump. In this case, we perform static analysis. It is mostly used during incident response. And Paul started to give some tips:
- “.logopen” is used to log everything to a flat file
- “!pool <xxxx>” 4-bytes char associated with a dynamically allocated chunk of pool memory
- “!object \driver\null” (this is typical to Uboburos  – not a joke)
- “!devobj xxxxxxx“
- “!chkimg nt -d” to perform integrity control (detect corrupt image by comparing the code in memory and the symbol store)
- List exported symbols: x Example: “x USER32!Create*“
- Check if the driver’s signing enforcement is enabled with “dq nt!g_cienabled“
- !process !explore.exe
- lm to list modules of a process
Finally, Paul gave an examples of pykd usage to analyse the Uroburos malware. It was a very interesting introduction to WinDBG. A suggestion could be to create a poster with all those nice tips.
The next presentation was “A timeline of mobile botnets†by Ruchna Nigam. Ruchna reviewed many malwares which targeted mobile devices.  It started in 2004 with the first malware but they were not real bots (no communication with a C&C). The real precursor was Symbian Yxes in 2009 (Internet access and SMS propagation) Internet access was not so common in 2009! Eeki.B targeted iOS devices (jailbroken only) and performed ssh scanning using the classic well-known default password ‘alpine’).
Which are the most affected mobile devices?
- Android (93%)
- Symbian (4%)
- iOS (1%)
- BlackBerry (1%)
- WinCE (1%)
And we continued to review a timeline of well-known infections:
- 2010: Symbian Zitmo (Zeus in the mobile) then multi-platform later
- 2011: Android DroidKungFu (root exploits and propagation)
- 2012-2013: Android Banking malware (Spitmo, Hesperbot, Perkel, Korean Banking Malware)
- 2013: BadNews (>2M downloads from Google play store), AndroRat (spyware), Claco (PC infector)
- 2014: Ransomware (Pletor.A, .onion C&C)
What type of data are most stolen? IMEI numbers, IMSI numbers, phone numbers, build info and location. The communications with C&C are performed over HTTP(S), SMS or a combination of both. This last type is nasty: if the current C&C becomes unavailable (ex: taken down), a new configuration is pushed through SMS messages! What are the motivations from criminals? If financial motivations become more and more important, it is due to the premium SMS services and the banking trojans. She also reviewed interesting cases like Android/SMSHowU which, when a SMS “How are you?” is received, send the mobile position via a Google map URL. Twikabot is a malware which communicates via Twitter. NotCompatible converts the infected phone into a proxy. The traffic is redirected to the C&C, guess what when the mobile phone is connected to a private network via a WiFi hotspot? There are multiple attack vectors: Google play can used but the malicious app is often quickly removed. Third party app-stores are real pain! FakePlay.C is also a nasty one: it infects the PC connected to its USB ports and used the autorun feature. Chuli was a specific one sent via mail attachment to all attendees of a conference. Some others targets groups of hacktivists like Xsser which targeted the “occupy central” participants in Hong-Kong (send via a Whatsapp message). Ruchna’s conclusions are: Mobile malware are a fact, not a fiction. They are more C&C channels than on a regular victim and they can be upgraded remotely (increasing the resilience). It was a nice review of the situation in the mobile world which is not better than classic computers. Maybe even worse due to the fact that people don’t consider them as real computers. She closed the talk with a nice demo of a live infection seen from the C&C… What a sensation of power!
The coffee break was followed by “Ad Fraud botnet 101†by Aleksander Tsvyashchenko and Sebastian Milieus from Google, which is a key player in ads networks! The presentation started with some examples like Win32.Bot.ZeroAccess2, Win32.Bot.ZeusZbot_P2P. The ZeroAccess traffic volume is estimated to millions of ads requests! It’s huge and fuelling the underground economy and the attack surface increases. The presentation focused on bots which generate false clicks on ads (fraud) and not to ads which delivers malicious code.
A classic ads ecosystem is simple: we have a direct deal between an advertiser and a publisher. In this ecosystem, the main issue is the scalability. Then came another model where we have more and more new players between the two original parties (ex: Google). The model can become very complex and each party takes a percentage on the price of a click. Billing models are based on CPC (“Cost Per Click“), CPM (“Cost Per Mile“) or CPE (“Cost Per Engagement“). With more and more parties trying to grab some cents at each click, it is normal to see more and more fraud attempts! That was the second part of the presentation. Aleksander and Sebastian explained in details how such botnets are working. The primary goal is to mimic a user browser (environment, user activity, mouse movements, etc). Each browser can be “infected” and have components added to automate such tasks. Once infected the computer surfs the web, detects clickable zones and click! But such artificial clicks have patterns that can be used to detect them (they click only on borders) as seen in the picture below:
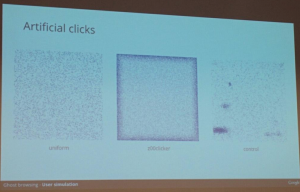
This behaviour is used by Google to detect fraud! While talking with friends after the presentation was: what percentage of fraud is “allowed” by Google. Of course, as seen in the beginning of the talk, Google is part of the business and each click earns a few cents. What was interesting is also the monitoring of the botnet and the very quick reaction time in case of take down operation (the botnet being down means no revenue!). Very interesting talk, I learned lot of interesting stuff in this field.
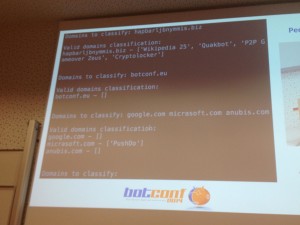
Then, Pedro Camelo and Joao Moura presented a tool called CONDENSER. It is a graph-based approach for detecting botnets. After an short introduction about botnets (was it necessary for the Botconf attendees?), they focused on the detection methods available: In a passive way, we can inspect packets, network flows, domain name syntax (ex: % of vowels, length, english words, …). In an active way, we can check the DNS resolutions. Once collected, you can correlated the information and play with infected machines, IP addresses reputation, malware analysis, … A demo was performed: tagging domain names with bot names. Interesting but the demo was very light.
After the lunch, we restarted with Ivan Fontaresky and Ronan Mouchoux who presented “APT investigations backstageâ€. The first indicators: OSINT, 3rd parties, customers or bad guy watch. What is a suspect? A data! IP addresses, domains, logins,  binaries. They can be identified from a knowledge base or from different aspects: behaviour, social or financial. The keyword is “Follow your enemy“! Build your knowledge base! But what is a suspect behaviour?
- Usage of too much encryption
- Buy many anonymised servers
- Submission several times of the same malware (until not detected)
- Domain typo-squatting
- Work outside “normal hoursâ€
The next part of the talk was how to build a performant team. Choose your area of expertise. Try to estimate how many people you need. Keep in mind that more people means more competencies and more complexity for sharing info. People must have an area of competence but also be backup for a colleague. To resume, they explained how to work in team. When investigations are over, what to communicate? Do we anonymise What about privacy (even of the attacker). Technically we are all good but we have to improve working in teams and teams of teams.
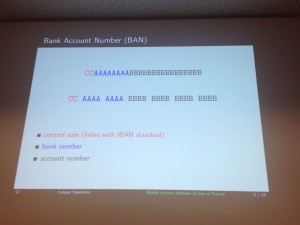
The following talk was very interesting: “Middle income malware actors in Poland: BVKlip & beyond†by Lukasz Siewierski from CERT.pl. This talk focused on a malware that is active in Poland only, Lukasz never saw it outside his country. In Poland, people do a lot of e-banking and wire transfer. Bank account numbers are based on the following format:
How do people work? They receive a payment request from a third party via PDF files. They copy/paste the bank account number. Guest what? If they are infected by the VBKlip malware, the clipboard content is changed on the fly if the data correspond to a bank account number. It is replaced by another number (the one of the attacker). Nasty! This malware can be detected using the following IOC’s: the following processes are running on an infected host: atidrv32.exe, winlog.exe and ms32sound.exe. SMTP is used for communications. The infection vector is mainly via email. Banatrix is another alternative. It has a funny way to replace data using a keylogger: it waits for 26 characters corresponding to a bank account number and send 26 backspaces then retype the new numbers! Very nice presentation with a unusual way to process data.
Paul Jung presented “Bypassing sandboxes for funâ€. I missed this one at hack.lu in October and I was very happy to follow this talk which looked intersting. In his introduction, Paul explained that, today, every malware is unique. To help in detection, companies are adding sandboxes in their network and are playing in sand:
- The code is executed in the sandbox, sometimes against multiple OS
- The sandbox  logs, hooks, captures and rely heavily on virtualisation!
There are plenty of solutions on the market… free or commercial. Paul tested them. The goal for the malware is to detect if it is running in a v virtualised environment. If it is the case, the malware just stops its execution. So, Paul explained how to seek for virtualisation! VMware offers a very huge footprint in the registry, files and processes. They detect MAC addresses artefacts. Virtualised hardware has often the same serial numbers. Another technique is to use 64-bits software, to check the browser history, user activity, a potential link with an ActiveDirectory.
The next step is to be more stealthy and to check without calling API’s. A good practice is to detect the number of CPU, most VM have only one. But today, even the smallest computer has at least a dual core. It is also possible to detect the hypervisor brand via the CPUID. Another tip: VirtualBox does not report a L-1 cache for the CPU, real CPU’s have L-1 cache for years! Between all the test performed, only Joe Sandbox resisted to Paul’s tests but it’s not really a nice appliance like other products and not usable as is in a network. I had an interesting chat with Paul in the evening: very interesting feedback about other solutions and how they reacted to his research. To conclude the talk: harden your VM’s to reduce the detection ratio, never install the provided tools. Here are some interesting link about this topic:
- http://www.kernelmode.info/forum/viewtopic.php?f=11&t=3478
- https://github.com/jbremer/vmcloak
- https://github.com/Th4nat0s/No_Sandboxes
- http://bit.ly/1zZJkth
Another very interesting one: “Learning attribution techniques by researching a Bitcoin stealing cyber criminal†by Mark Arena from INTEL 471. What is attribution? It’s taking an incident and figuring out who and why, who’s being the keyboard? It depends on the motivation of the threat actor: cyber espionage VS. hacktivism VS. cyber crime. If you can’t disrupt the criminal makes his life difficult (Think about the “WANTED†posters published by the FBI).
Bitcoins are interesting case. To search for an actor, it’s a human habit to reuse stuff (usernames, ICQ, IPs) etc. It’s very difficult over a long period to completely separate two online entities. It’s not just a name and address! We need to know a lot of stuff about him (goals, methodology, etc) How to start? From an incident? (action – reaction) or start with an actor (actor-centric). Mark’s talk could be sub-titled “Doxing for Dummies“, he explained step by step how he investigated the case of an attacker (probably located in France) who stole Bitcoins. He found plenty of information like:
- Malware samples
- Bitcoin wallet ID
- Email address
- PerfectMoney profile
- Whois info from domains
- …
It was a very great step by step introduction. The guys is probably located in France and targets users of crypto currencies. His new malware can be easily detected but Mark is not sure of who’s behind the keyboard!
The two next presentations focused on the same topic: DDoS. The first one was presented by Dennis Schwarz from Arbor Networks. Called “The Russian DDoS one: Booters of Botnets†or “RD1“. You want to rent a botnet? It will cost you $5 for 1h. DDoS became a real business with plenty of potential customers. They also have a reputation service, vouchers, dispute resolution procedures, exactly like a normal business!
If the first part was interesting, Dennis continued with a presentation of all know botnets, one by one with the same slides: what they propose, the architecture in place and known targets. This was not very relevant for me! Then, again about DDoS, Peter Kalnai and Jaromir Horeisi presented  “Chinese chicken: multi-platform DDoS botnets“. They explained with many slides a botnet based on ELF binaries… Very nice research but the slides contained too much information (MD5, SHA1, IP addresses, filenames, etc…). Impossible to take some notes! If you are interested, I suggest you to have a look at the great review make by MalwareMustDie.
Finally, Tom Ueltschi closed the second set of talks with “Ponmocup Hunter 2.0 – The sequelâ€.  Tom presented his project during the first edition of Botconf (link to my wrap-up) and came back to give new details. He performed a very good job to track this botnet which is huge (21M infected servers) but remains below the radar! He also gave details about the Zuponcic exploit kit.
What about Ponmocup finder for the masses? The idea is to find more infected servers. A new version of the script was written in Python and tested against the Alexa 1M list as PoC. One fact is that being in the top-rank does not mean that the website is more secure! How to prevent & detect infections? Block known IP ranges and to detect check for DNS lookups to intohave.com or fasternation.net. The botnet has also an interesting anti-sinkhole technique (data is encrypted into a cookie). Once again, good job Tom!
A second set of lightning talk was organised to close the day. Topic were:
- Somehow unusual Android malware sample: Why is there a LUA library in this sample?
- Hewlett-Packard the C&C owner: Retefe white space encryption!
- Grading intelligence – The UK system: new implementation of TLP “make in UKâ€
- Stop using MD5:
- Radare2
- “Water Torture†attack
A social event was organised at the Musée des Beaux-Arts of Nancy. Very nice place, very nice food and people, what else to finish the day?








RT @xme: [/dev/random] #Botconf 2014 Wrap-Up Day #2 http://t.co/4dYHjrTLDu
RT @xme: [/dev/random] #Botconf 2014 Wrap-Up Day #2 http://t.co/4dYHjrTLDu
RT @xme: [/dev/random] #Botconf 2014 Wrap-Up Day #2 http://t.co/4dYHjrTLDu
RT @xme: [/dev/random] #Botconf 2014 Wrap-Up Day #2 http://t.co/4dYHjrTLDu
RT @xme: [/dev/random] #Botconf 2014 Wrap-Up Day #2 http://t.co/4dYHjrTLDu
RT @xme: [/dev/random] #Botconf 2014 Wrap-Up Day #2 http://t.co/4dYHjrTLDu
RT @xme: [/dev/random] #Botconf 2014 Wrap-Up Day #2 http://t.co/4dYHjrTLDu