 Following the presentation that I made at the RMLL 2014 last week, I slightly changed my malware analysis setup. The goal is to make it fully operational “offline“. Indeed, today we are always “on“, Internet is everywhere and it’s easy to get a pipe. However, sometimes it’s better to not send packets to the wild Internet, even more when playing with malwares. We can be connected to a network with restricted access and some “exotic” ports won’t be authorized (ex: IRC). By allowing malicious code to connect to the world, we could trigger some firewalls, IDS or IPS if working in a corporate environment. If the malware is targeting a specific company or country, it can be suspicious to flood the C&C or any other resource with suspicious traffic (in this case, we are suspicious for the attacker). In short, “to live happy, live hidden” 😉
Following the presentation that I made at the RMLL 2014 last week, I slightly changed my malware analysis setup. The goal is to make it fully operational “offline“. Indeed, today we are always “on“, Internet is everywhere and it’s easy to get a pipe. However, sometimes it’s better to not send packets to the wild Internet, even more when playing with malwares. We can be connected to a network with restricted access and some “exotic” ports won’t be authorized (ex: IRC). By allowing malicious code to connect to the world, we could trigger some firewalls, IDS or IPS if working in a corporate environment. If the malware is targeting a specific company or country, it can be suspicious to flood the C&C or any other resource with suspicious traffic (in this case, we are suspicious for the attacker). In short, “to live happy, live hidden” 😉
My setup is running on IOS because I’m always carrying my MB with me but it is easily reproducible in a classic Linux environment. To capture all traffic and redirect to fake services, you just need to run a shinkhole DNS which will answer to all queries with a configured IP address. To run the DNS and the services, the best tool (IMHO) is called INetSim or “Internet Services Simulation Suite“. It’s a Perl script which can emulate all basic network services (HTTP, SMTP, FTP, etc) and even respond with valid transactions. No need to deploy the Perl script and all its dependencies, just install a special Linux distribution called REMnux. It is a specific Linux image bundled with plenty of tools to perform malware analysis and one of them is… INetSim of course!
As suggested in the Cuckoo documentation, I’m using a host-only network (192.168.38.0/24) for communications between Cuckoo and its guests. My first idea was to deploy REMnux in the same network but… For VirtualBox, a host-only network is very specific and hosts are talking directly to each others. It’s not possible to put an interface in promiscuous mode and sniff the traffic! Michael Boman is a blogger very active in the Cuckoo community and he wrote last year an interesting article which describes how to sniff remotely. Interesting but I prefered to test another configuration as seen on the figure below:
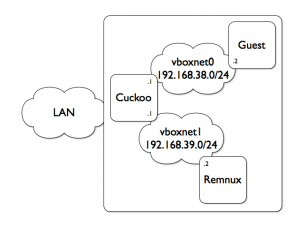
I created in VirtualBox a second host-only network (192.168.39.0/24) and moved the REMnux host to this network. At OSX level, I enabled the IP forwarding to allow packets to be routed across the two subnets. The Cuckoo guest was reconfigured to use the new REMnux IP address as DNS resolver. I have now the following config:
- Remnux – 192.168.39.2
- Cuckoo Guest – 192.168.38.2
- Cuckoo Host – 192.168.38.1 & 192.168.39.1
INetSim is configured to always return the REMnux IP address and to respond (+log) to all classic services. Cuckoo is still configured to sniff on the first host-only network (vboxnet0) but, strange behavior, it sees only the incoming traffic (fortunately which is the most important for DNS request – HTTP(S) GET/POST). I’m still looking for tips or ideas to capture packets in both direction. OSX has also a pecific syntax for tcpdump to allow the packet capture to run on multiple interfaces:
# tcpdump -i pktap,vboxnet0,vboxnet1 ...
But Cuckoo does not work with a sniffing interface format like this (the reporting fails and aborts). If somebody has an idea… Anyway, this setup allows me analyse malicious pieces of code without sending any traffic to the Internet.
Note: when you completed the analysis, saved the guests and exited Cuckoo, don’t forget to disable IP forwarding!
Hi Dan,
I don’t see a big problem here… Why take the risk to hardcode the C&C IP address in a malware? Such IP addresses can be detected very quickly and brought down by ISP’s/authorities. That’s why Fast Flux DNS is used… My $0.02
Hi,
Just a question: what happens if the malware tries to access a hard-coded C&C server by IP? In this case it won’t generate any DNS queries, and such I think the malware will get “Unable to connect”. What is your assumption for this scenario ?
Dan
For complete offline analysis another great tool is Fakenet (practicalmalwareanalysis.com/fakenet/)
-resolve all network request (ip/DNS) on localhost
-see any network request
-have some default files: exe, html, gif, jpg, pdf, etc. that will be served if malware request any file from internet
-simulated traffic is saved as a pcap file
is a great tool for analysing malware without network connection