 In January, I developed a tool to sniff Wi-Fi SSIDs. I decided to call it ‘hoover‘ (based on the vacuum cleaner brand). The original post is here. I’m often running this tool in my area to detect the presence of some people in the neighborhood or when I’m staying at hotels. But usually, the scan scope is very limited.
In January, I developed a tool to sniff Wi-Fi SSIDs. I decided to call it ‘hoover‘ (based on the vacuum cleaner brand). The original post is here. I’m often running this tool in my area to detect the presence of some people in the neighborhood or when I’m staying at hotels. But usually, the scan scope is very limited.
A friend had the wonderful idea to run hoover during a major Belgian event: The Rock Wechter music festival! Belgium is a wonderful country for music lovers. Plenty of festivals are organized across the country during the summer. They are covering all music styles! Such public events are great places to find good samples of citizens. During four days, 139.000 unique people attended the festival (source). And guess what people are always carying with them? Their smart phones of course!
The high number of visitors attending festivals represents a very good sample of “common users“. We have:
- Belgian, foreigners
- Young, old people
- Male,female
- Students, workers
- French, Dutch speaking people (Yes, that’s Belgium!)
- etc…
My friend had a chance to stay at a good location. This was an excellent opportunity to keep his laptop safely running hoover to collect broadcasted SSIDs. What can we discover from the (huge) log file? Here are some of my findings…
First numbers:
- 29194 unique SSIDs were detected!
- 6475 unique MAC addresses (devices)
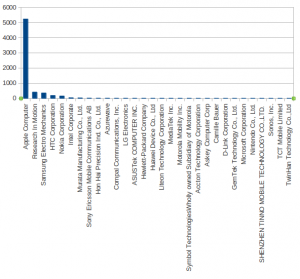
Among the detected SSIDs, here is the top-20 (based on the seen requests):
| Requests | SSID |
| 807891 | Hotspot-Corelio |
| 18853 | trofanaroyal |
| 13984 | RWIFI |
| 10693 | FON_BELGACOM |
| 9807 | Groezrock |
| 7775 | free-hotspot.com |
| 7042 | default |
| 7010 | linksys |
| 6899 | RKVL-COMCAR |
| 4891 | TELENETHOTSPOT |
| 4890 | Wifi Ranst NIV0 |
| 4653 | UZLeuven-gast |
| 4584 | zampass |
| 4485 | dlink |
| 4055 | shithappens |
| 3735 | Netwerk van Geert Delbaere |
| 3729 | St4rt |
| 3713 | wifi@home |
| 3712 | aspbs |
| 3685 | telenet-38C64 |
This top-20 is very interesting to conduct WiFi attacks later. We can see that SSIDs like “dlink” or “default” are commonly used. From an attacker’s point of view, this list is interesting to wisely choose the SSIDs which will increase your chances to attract devices to your rogue access point. I’m wondering what’s the first SSID (“Hotspot-Corelio“)? Corelio is a big Belgian media company which edits lot of newspapers. Maybe they were the sponsor of the official Wi-Fi access?
A fact: many people disclose their name via their SSIDs. There was plenty of networks with names. 169 SSIDs based on “Network of xxx” were detected. Some examples:
- “Netwerk van Geert Van Assche”
- “Beernaert-Geusens”
- “Netwerk van Alex Van Hoydonck”
- “Netwerk van Joost MUYLLE”
- “Netwerk Dennis De Smaele”
- “Netwerk van Dimitri De Schryver”
- “Famille Moies-Delval”
Lof of SSIDs contained geographic details (airports, city names). This helps us to build a list of countries from where the festival visitors came:
- France
- Morocco
- Italia
- Germany
- Holland
- UK
- Canada
- Burma (Myanmar)
- Luxembourg
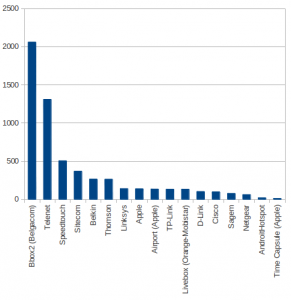
What about the hardware used to build wireless networks? Lot of Wi-Fi access point owners do not change the default SSID or just add extensions like a number or a name. Below is the repartition of hardware based on common strings:
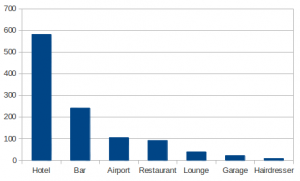
Where people do use Wi-Fi connectivity? Mostly in hotels:
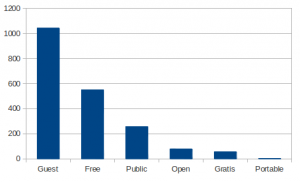
They also use free networks:
Of course, there are always some funny SSIDs:
- Hide yo kids, hide yo wi-fi
- LA TAVERNE with Big Boobs
- ( . )( . )
- Network of Darkness
- true-story_W64_trojan.exe
- 1heinekenplease
- HP-Print-c1-LaserJet 400 MFP
- Fort Knox-guest
- www.lloretwifi.es +34672530193
- boutrosboutrosgali
- pretty fly for a WiFi
- megavirus
- FUCKOFF58bis
- louloute qui boit le sperme ! ! (No comment – I won’t translate it)
- Anonymous
- trojan.exe
More events will be covered by my friend. He will try to perform the same operation. This will be a good opportunity to compare results.
Final disclaimer, no intrusion or attack of any kind was performed. The tool just listen passively for information broadcasted from Wi-Fi enabled devices.
The complete list of SSIDs is available here.
Hello Wouter,
You’re right… Example: Belgian citizens who visited hotels abroad.
Thanks for your comment.
I don’t know which model he used. Personally, I’m using a BT5 + AWUS036NH.
(You need a card supported in monitor mode)
Lof of SSIDs contained geographic details (airports, city names). This helps us to build a list of countries from where the festival visitors came:
That’s based on the incorrect assumption that geographically-named ESSIDs can only be used in the area as described by that geographic name.
It would be correct to say that the ESSIDs gives you a list of countries people have an affiliation to, or countries they like, or some such. That doesn’t necessarily imply they actually hail from that country…
Looking forward to more of these. Did your friend use the built-in wifi adapter or some external/more powerful one?