BruCON is over! As usual, when I attended a security conference, I’m trying to write a small wrap-up for me followers. With BruCON, it’s completely different: I’m on the other side of the stage. For the “0x03” edition, I was again involved in the “bits & bytes” stuff. I did not attended talks always between two requests or small problems to solve… and I like this!
So, building a network for a security/hackers conference is a great challenge. You have to provide a (as much as possible) free Internet access but, for legal reasons, you have to keep an eye (even both!) on the visitors behavior. To achieve this, we kept a trace of all network flows generated during the conference. For privacy reason, we do not keep the payloads, just the IP headers (source IP/port & destination IP/port with timestamps). The audience of a security conference are normally good skilled people regarding security. I analyzed the data captured during the two days (Monday 19th and Tuesday 20th). Here are some facts…
First, a few words about our setup. We provided three different networks: A public Wi-Fi available to all the visitors, a private Wi-Fi dedicated to the crew, speakers and “VIP’s” and a wired network for trainings, workshops, the crew. Our Internet pipe (1Gbits) was provided by Belnet, the Belgian national research network with IPv4 as well as IPv6. The traffic was captured and analyzed in real time by a network sniffer which provided interesting statistics:
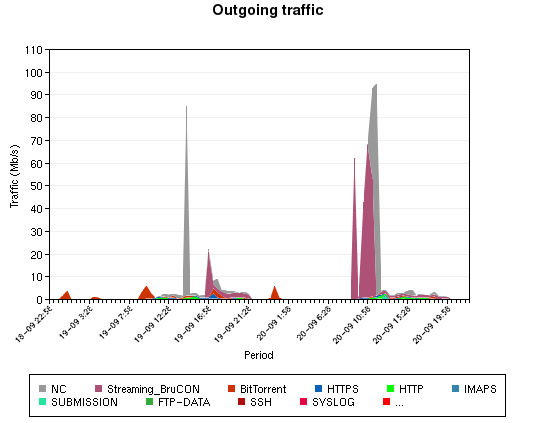
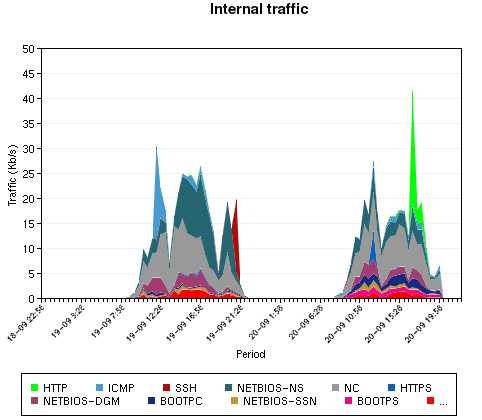
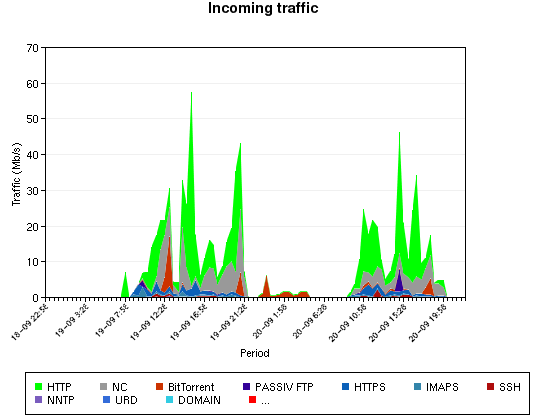
The “Internet traffic” is the traffic exchanged between the different networks. The “Incoming traffic” represents the traffic from the Internet (the users downloads) and the “Outgoing traffic” represents the traffic sent to the Internet. The peaks are the tests performed by our video team with higher quality streaming.
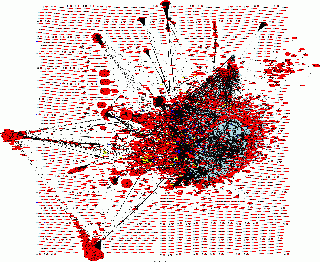
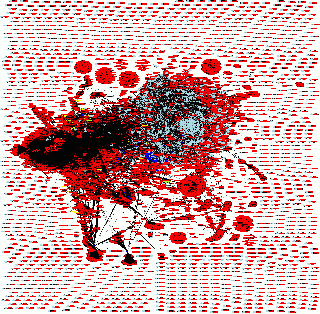
 What about the flows between hosts and the Internet? The following maps represents the traffic exchanged on Monday and Tuesday.
What about the flows between hosts and the Internet? The following maps represents the traffic exchanged on Monday and Tuesday.
Were our visitors aware of their own security? For the second time, we run a wall of sheep during the conference. We sniffed the public Wi-Fi network (and only this one!) for interesting traffic. Again and again, some people still use unsafe protocols! A visitor sent thousands of SNMP requests over the network during the event. I suppose this guy was using a corporate laptop with a running network tool in the background. Note that the traffic capture was executed live and no data was saved nor divulged outside of the BruCON network team.
Here are the top detected protocols:
| Protocol | Detected Occurrences |
| SMB | 4894 |
| IMAP | 1159 |
| HTTP | 481 |
| FTP | 340 |
| POP | 63 |
| TELNET | 30 |
| NNTP | 8 |
The web traffic was also analyzed. The traffic sent over the well-known ports (80, 8000, 8080, 3128, 443)Â was inspected to extract URLs. Here again, only the URLs were extracted, the HTTP content was not inspected nor stored.
Here is the top-30 of the most visited sites:
| URLs | Detected Occurrences |
| pwn3d.be | 2751 |
| www.google.com | 2624 |
| search.twitter.com | 2392 |
| www.google.be | 2137 |
| www.facebook.com | 1761 |
| 193.191.65.51 | 1546 |
| api.twitter.com | 1331 |
| notify8.dropbox.com | 1546 |
| pixel.quantserve.com | 1065 |
| notify2.dropbox.com | 882 |
| platform.twitter.com | 791 |
| static.ak.fbcdn.net | 729 |
| brucon.openamd.org | 710 |
| api.openbeacon.net | 681 |
| notify1.dropbox.com | 679 |
| twitter.com | 662 |
| notify7.dropbox.com | 660 |
| profile.ak.fbcdn.net | 623 |
| cdn.api.twitter.com | 613 |
| mail.google.com | 598 |
| notify6.dropbox.com | 586 |
| clients1.google.com | 553 |
| www.youtube.com | 515 |
| suggestqueries.google.com | 506 |
| www.msftncsi.com | 495 |
| fxfeeds.mozilla.com | 472 |
| csi.gstatic.com | 465 |
| notify9.dropbox.com | 465 |
| connect.facebook.net | 461 |
| ocsp.verisign.com | 454 |
The top URL (pwn3d.be) was in fact the wall of sheep. I saw lot of people keeping an eye on this page. The IP address was an address from the DHCP pool used by visitors. Otherwise, nothing fancy, the classic websites remains the same. Interesting to see how many people are using Dropbox!
But, it is sometimes interesting to search for the most obscure URLs (read: accessed only one time) or what occurs below the radar. Funny: did a visitor make some only shopping (c-and-a.com) during the conference? 😉
| URLs |
| media.rtl.be |
| br.yahoo.com |
| br.m.yahoo.com |
| p4.dkqv3d2fqxlpe.ailhxnhx2lw7xjgs.595488… |
| debianadmin.com |
| www.pandasecurity.com |
| p4.dkqv3d2fqxlpe.ailhxnhx2lw7xjgs.if.v4…. |
| www.windowsreference.com |
| static.zanox.com |
| api.zanox.com |
| platinum-suisseid-g2.ocsp.swisssign.net |
| IndC1DigitalID-crl.verisign.com |
| crl.swisssign.net |
| cache.pandasoftware.com |
| static.googleusercontent.com |
| pool.pebblemedia.adhese.com |
| content.landingpage.be |
| m.iszene.com |
| c.tifbs.net |
| postview.c-and-a.com |
Of course, we installed an IDS to capture suspicious traffic. The top detected events follow:
| Signatures | Occurrences |
| MS-SQL probe response overflow attempt | 9162 |
| POLICY poll.gotomypc.com access | 2343 |
| DNS SPOOF query response with TTL of 1 min. and no authority | 875 |
| MISC MS Terminal Server no encryption session initiation attempt | 288 |
| MISC MS Terminal server request | 150 |
| NETBIOS SMB-DS repeated logon failure | 103 |
| MS-SQL version overflow attempt | 48 |
| RPC portmap status request UDP | 30 |
| NETBIOS DCERPC ISystemActivator path overflow attempt little endian | 18 |
| WEB-CLIENT PNG large image height download attempt | 10 |
| ATTACK-RESPONSES id check returned root | 6 |
| MISC AFS access | 6 |
| MS-SQL ping attempt | 6 |
| WEB-CLIENT Windows Media Player directory traversal via Content-Disposition attempt | 6 |
| INFO Connection Closed MSG from Port 80 | 4 |
| WEB-CLIENT PNG large colour depth download attempt | 2 |
| MISC Source Port 20 to <1024 | 1 |
Did we face security incidents? For sure, I detected classic stuff:
- Rogue access points (broadcasting the “brucon” SSID)
- Port scans
- Gateway ARP spoofing
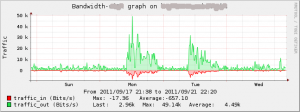
A few words about IPv6? We offered IPv6 via router advertisements. 10% of the visitors accepted the RA and got an IPv6. As the BruCON website is running on IPv6, it was the preferred protocol during the event:
To conclude, some tips if you are to deploy a network during a security conference in a “wild environment“:
- Internet is mandatory. Your visitors expect to have a powerful and reliable Internet access. Be prepared to the worst! Our DNS/DHCP crashed in the middle of the conference! Have backup plans and alternative solutions!
- Do not offer open Wi-Fi. Protect it via a WPA(2) key. The goal is not to avoid people to use it. The goal is to prove your “due care” in case of problems.
- In the same way, capture the traffic (via netflow, tcpdump or any other tool) to keep a trace of who did what and when. Don’t store the packets payload for privacy and performance (storage requirements) reasons.
- Keep an eye on your network, all the time. It’s like leaving hot milk on the fire.
- Try to keep control of all the infrastructure from A to Z. Ex: have access on a core router will help you to quickly implement basic access-lists to drop offensive users or protocols.
- Be reachable: broadcast a phone number and/or e-mail address where people could report suspicious activities.
- After the conference, burn a DVD with all your evidences (with SHA1/MD5 hashes).
Flows have been exported from a sniffing appliance and maps generated by AfterGlow.
Nice work
what did you use to get the flow map? etherape?
tkx
The OpenAMD.org BruCON 2011 team released a social network graph in PNG and PDF format. You can find canned versions of the visualizations and the gathered data for download there as well.