 I was looking for a Nagios application to install on my iPhone for tests purpose and I was surprised to find more hits than expected. It’s true that Nagios is one of the best (if not THE best) open-source monitoring solutions. There is a huge community of developers and contributors busy to add extra features or tools around the core application.
I was looking for a Nagios application to install on my iPhone for tests purpose and I was surprised to find more hits than expected. It’s true that Nagios is one of the best (if not THE best) open-source monitoring solutions. There is a huge community of developers and contributors busy to add extra features or tools around the core application.
It sounds logical that a lot of projects started to expand Nagios monitoring capabilities to mobile devices. This post focuses on iPhone devices but the same logic applies to all mobile platforms.
Before deploying an application on my mobile, I had a look at the security aspects! Basically, Nagios is a web-based applications and could be accessed directly from any mobile browser (no web 2.0 technology is used). The best way to access it is to access it through a (SSL)VPN. But the standard web interface is not designed for small screens. Using a wrapper is much more convenient and use perfectly the mobile native interface but introduce some risks…
First,some applications are available for free and only provide a “read-only” access to the Nagios data. On the other side, paying applications offer more features and allow the user to interact with the Nagios servers via a “read-write” access. Possible actions are the Nagios classics: enable/disable checks, add comments, schedule downtime, acknowledge problems etc.
Second, I reviewed some available applications on the AppStore. They use different methods to access the Nagios data:
- Some access a MySQL database. In this case, Nagios must be configured to use NDOutils, an add-on which uses a MySQL backend to store the monitoring data.
Example:Â The old versions of N-Mobility. - Some access directly the Nagios standard interface (based on CGI scripts) and “simulate” a browser.
Example: TouchMon. - Some uses a specific wrapper coded in PHP which grabs the Nagios data using the standard CGI scripts
Example: New version of N-Mobility or iNag.
Of course, you can restrict access to Nagios via the organization WiFi network but today, users need mobility! The main consequence is: data could be accessed via wild WiFi, Edge or 3G networks. If you plan to deploy Nagios application on mobile devices, there are several security issues that you have to keep in mind:
- Nagios servers contains critical data and must not be directly reachable from the Internet. The data contained in the configuration files and check results has even more value than a port scan from a pen-tester point of view. It’s just like a gold mine!
- Data sent between the Nagios server and the iPhone will pass via untrusted networks. They must be encrypted using SSL.
- How to authenticate the mobile devices? Only authorized devices can retrieve Nagios information.
- What about the data stored locally in the mobile device memory? How does the application handle the data?
Here is an example of architecture to deploy a Nagios mobile application “in the wild”:
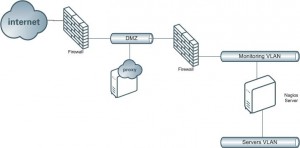
The traffic coming from the Internet must of course be filtered by a firewall. The mobile devices will use a server in a DMZ where will be installed the “wrapper”. Connections from this wrapper to the Nagios server will be restricted and inspected by a second firewall. The traffic between the mobile devices and the proxy (at least) will be encrypted and authentication is mandatory.
A good recommendation is to allow only a “read access” to the Nagios data. This will allow the mobile user to have a clear view of what happens on the monitoring infrastructure. If he needs to perform an intervention, he will use the regular remote access solutions (corporate laptop, SSL VPN, token, etc).
To conclude, the remaining question is: do you really need to access Nagios when you are not at the office? Just from my own point of view…