 pcapr.net is a cloud (again!) service available for a while. Basically, it’s a repository of pcap (“packet capture”) traces uploaded by members. The packets are dissected and presented in a human readable form. Once inspected and indexed, a search engine helps you to find interesting traces using a simple syntax like “http admin” or “sip and “180 ringing“. It’s also possible to tag some interesting packets or edit them.
pcapr.net is a cloud (again!) service available for a while. Basically, it’s a repository of pcap (“packet capture”) traces uploaded by members. The packets are dissected and presented in a human readable form. Once inspected and indexed, a search engine helps you to find interesting traces using a simple syntax like “http admin” or “sip and “180 ringing“. It’s also possible to tag some interesting packets or edit them.
Pcapr released a tool called “xtractr“. As described on the web site, it’s an hybrid application (between the cloud and your local system). Pcap files potentially contain sensitive data (user names, passwords, cookies, …) and sending them to the cloud can be dangerous even totally impossible from a security point of view in some organizations. How does it work? xtractr makes usage of the tshark tool (normally, coming with any Wireshark installation). tshark is the command line version of the network analyzer. xtractr decodes your pcap files and index them. As it provides its own web server, you connect to it with your favorite browser and, in the same time, to the cloud (pcapr.net) to perform the analytics and correlation. Most important, all your data remains local!
Once the pcap files have been indexed, the following information is available via your browser:
- The hosts seen and who’s talking to who;
- The ports and applications used by servers;
- The decoded IP flows;
- The decoded packets;
- etc.
The indexed data can be searched like in Splunk… You “point and click” to refine your search criteria:
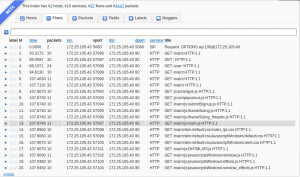
This is a nice tool for network administrators who need to know “what happens” on their network (what? You don’t know?), for forensics investigators or researchers who need to find evidences or suspicious activities.
Live demo: http://www.pcapr.net/xtractr/demo#/flows