 Do you remember the good old times? When I put my hands on my first firewall (somewhere around 1997-1998 – wow, time flies!), it was to kick out all the bad guys playing on the Internet. And, at this epoch, not all firewalls had a default last-resort rule like “Any > Any: Dropâ€! Later, the infosec landscape highlighted the wonderful “security perimeterâ€: Your network was like a castle with big walls! No one could enter! What a wonderful world!
Do you remember the good old times? When I put my hands on my first firewall (somewhere around 1997-1998 – wow, time flies!), it was to kick out all the bad guys playing on the Internet. And, at this epoch, not all firewalls had a default last-resort rule like “Any > Any: Dropâ€! Later, the infosec landscape highlighted the wonderful “security perimeterâ€: Your network was like a castle with big walls! No one could enter! What a wonderful world!
Some times later, companies realised that their users were first of all people with human behaviours, trying to surf the web during business hours. Some of them switched to a new profile: malicious insiders! It was time to also inspect and block the outgoing traffic.
Today, generally speaking, solutions are in place to inspect what is called the “egress†traffic (the opposite of “ingressâ€). Wikipedia defines “egress filtering†as follow:
In computer networking, egress filtering is the practive of monitoring and potentially restricting the flow of information outbound from one network to another. Typically, it is information from a private TCP/IP network to the Internet that is controlled. TCP/IP packets that are being sent out of the internal network are examined via a router or firewall. Packets that do not meet security policies are not allowed to leave – they are denied “egress”. Egress filtering helps ensure that unauthorised or malicious traffic never leaves the internal network.
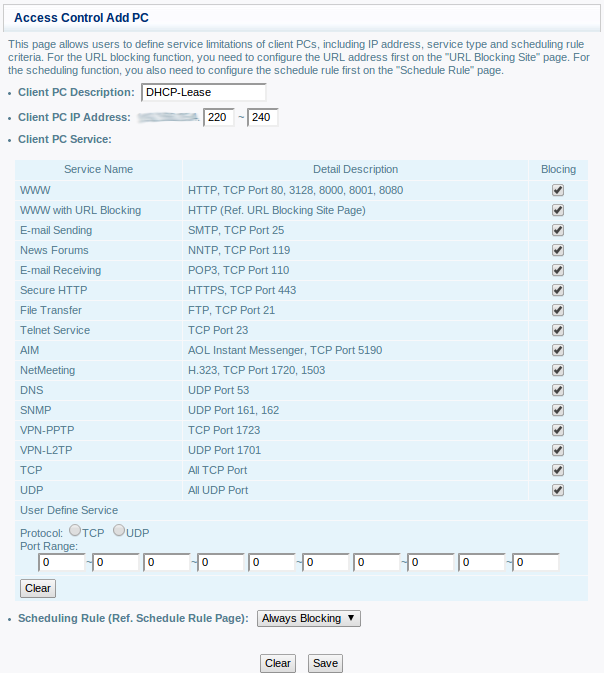
Implementing egress filtering is not always bullet-proof but it is a good start. Today, traffic like HTTP(s), DNS, SMTP cannot reach the Internet directly. So, what about your home network? If most DSL residential routers include firewall features, they remain basic and egress filters are often disabled by default. Here is an example of egress filter on a Belgacom BBox router:
What types of devices can we find in a home network today?
- Computers
- Game consoles
- Printers
- Phones
- WiFi devices (tablets, smartphones)
- Webcams
- Storage devices (NAS)
- Media players
- Heating systems, fridges
- Smart meters
- Smart TV’s
- Miscelaneous sensors
- Malware infections (callback to C&C)
- Your privacy! (like the LG story)
- Assign a fixed IP address to trusted devices
- Reserve a small DHCP IP pool for unknown (friends, visitors, …) or new devices and prevent this pool to access directly the Internet
RT @xme: [/dev/random] Controlling the “In”? Don’t forget the “Out”! http://t.co/QicKwUjnCw