 For a while, DDoS are back on stage and one of the classic techniques still used today is the DNS Amplification attack. I won’t explain again the ins and outs, there are plenty of websites available which describe it – like the good article from CERT.be. This type of attack is well-known and can be fixed in one click or by changing one line on a configuration file for most DNS servers! A few days ago, I asked myself: “And what about Belgium? Do we still have lot of vulnerable DNS servers in the wild?“. As you probably imagine, the answer is… “Yes, there are!” But how to have an good idea of the disaster? To collect some statistics, I looked for DNS servers in the Belgian IP space…
For a while, DDoS are back on stage and one of the classic techniques still used today is the DNS Amplification attack. I won’t explain again the ins and outs, there are plenty of websites available which describe it – like the good article from CERT.be. This type of attack is well-known and can be fixed in one click or by changing one line on a configuration file for most DNS servers! A few days ago, I asked myself: “And what about Belgium? Do we still have lot of vulnerable DNS servers in the wild?“. As you probably imagine, the answer is… “Yes, there are!” But how to have an good idea of the disaster? To collect some statistics, I looked for DNS servers in the Belgian IP space…
The first step was to build the list of IP addresses used in Belgium. First, I used the data provided by Nirsoft.net. They have CSV files with assigned IP blocks per country. To build a list of Belgian IP blocks, just download the right file and look for the corresponding route in the RIPE Whois DB:
$ wget -O - -o /dev/null http://www.nirsoft.net/countryip/be.csv | \
awk -F ',' '{ print $1 }' | while read N
do
whois -h whois.ripe.net $N | grep ^route: | awk '{ print $2 }'
done | sort -u >belgium_prefixes.tmp
But after doing  manual checks, some ranges from big organizations were missing in the result file. I cross-checked with the RIPE route database (here) and added most missing netblocks. The I got a file of 302 subnets from /15 to /24 (Nobody got an /8 in Belgium? ;-)) I’m not sure that the complete Belgian IP space was covered by this file but most ISPs, most big universities were listed. The next step was to search for open DNS servers using Nmap:
$Â nmap -sU -T4 -v -oA be-opendns -PN -n -p53 --version-intensity 0 --host-timeout 15s \
--min-hostgroup 512 --open -iL belgium_prefixes.tmp
$Â grep "53/open/udp" be-recursive.gnmap |awk '{ print $2 }'|sort -u >unique-ip.tmp
Those two commands scanned all IP addresses for open ports UDP/53 and extracted a list of detected DNS servers. At this point, we only have regular servers that could be or not open to recursive queries. It took me a few days to get the scan completed. The next step was to search for “bad” DNS. Easy, Nmap proposes a script to achieve this:
$Â nmap -sU -sV -T4 -v -oA be-recursivedns -PN -p53 -iL unique-ip.tmp \ --version-intensity 0 --min-hostgroup 512 --script dns-recursion
Those tests were performed from a foreign IP address for more accuracy. The results fro the commands above are (after some cleanup and processing):
- 6340 IP addresses answered to port UDP/53.
- 2121 IP addresses were vulnerable to DNS recursive attacks (Note: the Nmap script tries to resolve www.wikipedia.org)
Just to be certain of the accuracy of my results, I quickly performed a second check:
$ for I in `cat be-recursivedns.tmp` do host www.pastebin.com $I done >host.output $ grep 'www.pastebin.com has address 66.252.2.46' host.output | wc -l 1956
IMHO, the difference is due to the fact that many IP blocks are used by DHCP servers to temporary assign IP addresses to residential customers and the hosts behind those IP addresses are changing all the time [Post-note: this is confirmed by looking at the PTR records]. During the scan for vulnerable DNS servers, I also collected the version strings. Here are the results:
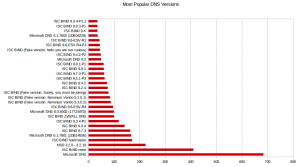
To conclude, two links to disable DNS recursion:
Belgium being a small country, the result of ~2000 vulnerable servers looks impressive and I’m not sure that the complete IP space was checked… If you are admin of a DNS server, double-check that recursive queries is not allowed for everybody (at lease from the Internet)! And something out of the scope but still interesting: Based on the gathered version strings, Â there are plenty of servers vulnerable to the latest vulnerabitlity discovered a few days ago in the ISC Bind server (CVE-2013-2854).
that magic you did with nmap is amazing . thanks for the cod3.
Which part is broken? Let me know, I’ll be happy to help!
Can you correct your first script, to get all the Belgian IPs ?
The first part extracts IP adresses but the second part is broken and bash isn’t my best friend, if you could correct and provide the source code that gives a correct output it would be really nice
RT @xme: [/dev/random] DNS Amplification Attack: Is Belgium Safe? http://t.co/w5e8hjWzmW
RT @xme: [/dev/random] DNS Amplification Attack: Is Belgium Safe? http://t.co/w5e8hjWzmW
RT @xme: [/dev/random] DNS Amplification Attack: Is Belgium Safe? http://t.co/w5e8hjWzmW
RT @xme: [/dev/random] DNS Amplification Attack: Is Belgium Safe? http://t.co/w5e8hjWzmW
RT @xme: [/dev/random] DNS Amplification Attack: Is Belgium Safe? http://t.co/w5e8hjWzmW
RT @xme: [/dev/random] DNS Amplification Attack: Is Belgium Safe? http://t.co/w5e8hjWzmW
RT @xme: [/dev/random] DNS Amplification Attack: Is Belgium Safe? http://t.co/w5e8hjWzmW
RT @xme: [/dev/random] DNS Amplification Attack: Is Belgium Safe? http://t.co/w5e8hjWzmW
RT @xme: [/dev/random] DNS Amplification Attack: Is Belgium Safe? http://t.co/w5e8hjWzmW
RT @xme: [/dev/random] DNS Amplification Attack: Is Belgium Safe? http://t.co/w5e8hjWzmW
RT @xme: [/dev/random] DNS Amplification Attack: Is Belgium Safe? http://t.co/w5e8hjWzmW
@xme The reference to CVE-2013-2854 is very mysterious since it appears this attack does not depend on recursion https://t.co/kQ9eZDrLwQ