
This is my wrap-up of the second day of RSA Europe. As said yesterday, the panel of speakers was broader and much more interesting. Let’s go!
My first choice was to follow a session about the growing of threats in embedded devices presented by Stuart McCluse (Cylance). He is the author of the “Hacking Exposed” book (link). In 1977, in the Star Wars movie, R2D2 hacked the death-star. This is the first time, a machine hacked another machine! During RSA 2012 in the United States, Stuart did a live hacking demo. For a while, he’s focussing only on embedded devices. The world of embedded devices in incredible:  Estimated 10 billions devices with little no security by design and using radio, GPS, WiFi, Bluetooth or hardwire connectivity without any protective solutions. Those devices are running plenty of different OSes on multiple CHIPs. Some examples given by Stuart were just scaring like theUDP port 17815 open on 250M devices for debugging purposes. How to find online embedded devices? Using Shodan of course! It looks that some devices use SSL for communicates. This looks cool… If it is properly implemented.  Example: Rugged.com devices. Stuart located the crypto goldmine using a simple hex editor.

He find the public key and later the private key. What can you do with a private key? Play MitM of course! Just capture some traffic and decrypt it using a dumb Wireshark (video on Youtube). The next example was the medical devices like insulin pumps. Those devices were owned using wireless connectivity. Backdoors allow communication with any pump up to 300 feet away! RFID devices are also vulnerable to cloning. Drones will be the next targets? Spoofing GPS signal. Cars, ATMs, … Everything is exposed! One of the most issues is the presence of backdoors for management, debugging purposes. MitP (“Man in the Phone”). they were able to make/receive calls or send text messages. GSM authentication spoofing via a specific Motorola phone flashed with a modified firmware. 3D-printers? MIT has Nanobots able to replicate forms. Nice but same issue, they don’t have any security feature in place. Stuart cited a coming “Digital Pearl Harbor“. What about the future? More and more devices will be connected (read: vulnerable). An interesting question from the audience: What about devices in Europe? (Most examples came from the US) Example: SmartMeters. They are facing the same issues.
The next two hours were again dedicated to keynotes. Philippe Courtot (Qualys) is a regular speaker at RSA events and presented his vision of big data (the new buzz word?). Data are everywhere and came from different horizons. Example: new applications are exploding the amount of data like the new cameras which control license plates. Tracking applications usually generates tons of data. Forget SAAS, PAAS, etc.. Cloud computing is a new architecture with a set of new technologies according to Philippe. This introduces lot of changes in scale and new challenges. Cloud is based on four components:
- Data Centers
- Web applications
- Internet
- Internet devices (end-points)
Big advantage of cloud solutions: they are always on and always up-to-date. The new perimeter is the web applications. Are we going back to a perimeter architecture? What about the automation of devices configuration using correlation rules (ex: WAF). And follow developers to write good code. New releases of code are coming quickly. Then it was the keynote of Misha Glenny (journalist). “The Struggle for the Internet“, I passed this one, sorry!
The next keynote speaker was Joshua Corman (Akamai). He asked us the following question; “Are we getting better?“, the answer is of course “No“. Then a second question came on the table, “Is it getting better? Or do you fell the same?” In fact, the question is: “How do you know?“. We have poor indicators of success and they are constant changes which affects costs, complexity and risks: evolving technologies, compliance, economics, business and threats. On a replaceability scale, we spend a lot of resources (too much) to protect resources which can be easily replaced (like credit-card numbers) but what about the human life or intellectual property? What about the security in terms of dependence? A good example is fighting SQL injections. This is a known attack for 13 years and we still fail to build a secure website. The OWASP Top-10 did not change over the last years. I like the following Joshua’s quote:
- s/Software/Vulnerability
- s/Connected/Exposed

Our challenges are not technical but cultural. The tactical-first approach has reached its limits. Another example: we focus on the symptoms and not on their cause. When we fail to share our data, we share our failure. Thank for the mention to the BruCON talk…
To close the keynotes session, Bruce Schneier came on stage and talked about “Trust, Security and Society“. It was the same topic has the one presented during Hack In the Box in Amsterdam so here is the link to my previous wrap-up.

After the lunch, the regular sessions started again. I attended James Lyne‘s talk about the latest attack frameworks used by cyber-criminals (“Cybercrime, Easy as Pie and Damn Ingenious“). His definition of APT? “Advanced Persistent Tweed“. Those packages become real commercial products with supports, features requests etc. Today the volume of malicious piece of code is growing (200K/day received by Sophos!). virtest.com can test your viruses and using their API automatically generate a new version when others are detected. Gwapo’s professional DDoS service is also a “service” available online for a few bucks. Another interesting category of malwares: ransomware. Files are encrypted by the malware and depends you money to get access back to them. Attackers count on emotional behaviour of the victim. Other malwares fakes police websites asking for a fine. Demo time! Problem: no admin privileges required! Best solution to fight against this kind of ransom ware: Restore your latest backup (if you have one…).

What about crime packs? A crime pack has a CRM tool ;-). Exploitability does not refer to the computer but to the user! Crimepack can be bought as a software or as a service in the cloud. They also offer technical support. The crime pack dashboard is more beautiful than some security products! Blackhole is another well-known crime pack. Now version 2 with plenty of new features. They also maintain a cloud blacklist based on IPs or referrer. To protect them selves against SOCs, labs. Be offensive: insert a malicious code in the console. Exploit them using their own exploit. The pay off? Find user names, phone numbers, pictures (with interesting meta data) Two steps forward? Let’s talk about IPv6 with a demo of flood_router6 against a Windows box. (100% CPU usage). Â Nice awareness tip about IPv6 even if out to topic (IMHO). Who can be trusted? James did a demo of SET (“Social Engineering Toolkit). Conclusions: please consider upcoming technologies even if not using them (IPv6) turn them off or harden them. Consider offensive moves carefully and watch those basics (yes people can be that silly). My preferred talk for today!
The next talk was the one of Paul Stamp (RSA) about “Implementing an intelligent SOC” (Security Opertation Center). Skills and tools have been covered. But first, what are the objectives of a SOC?
- Ensure that security controls are up’n’running and work corruptly.
- Make sure that security incidents are detected quickly and addressed efficiently with the goal to minimise the impact on the business.

What are the difference between a SOC and a CIRC (“Computer Incident Response Center“)? SOC can be seen as the first line. They need to fix. CIRC will investigate and coordinate the response. Based on the anatomy of an attack, Paul showed the anatomy of a response. If we put things together, there is the “attacker free time” between the beginning of the attack and its identification by the SOC. The goal is to reduce this attacker free time period of time. This can be achieved by rethinking the toolset. Ex: better security analytics tools that are accurate, work in real-tome and exhaustive. Then, a better use of the human assets must be performed. Finally, the amount of data to analyse is constantly growing, again performant tools must be used. Companies requires: comprehensive visibility, agile analytics, actionable intelligence, better incident response. Example of suspect scenation: peak of network usage, then user authenticated on AD, another user starting a VPN session using the same IP, then FTP session to the outside (data ex-filtration). To detect all of these, a SIEM is not enough. Ex: reconstruct the exfiltrated data? This must be done via logs and network packets capture tools. Then Paul explains a live infection attack and how it was detected by RSA using their security analytics tool. How to improve your SOC?
- Take the last 3 major security incidents
- Map out people and tools used to detect and investigate them
- Evaluate which task took the longest
- Create a map of data and skills you don’t have.
- Create a plan for your SOC improvement: What resources do you need?
- Evaluate the people process and technologies.
- Indentify the “worse”
- Start a roadmap to fix them.
After a last coffee break, Eric Vyncke (Cisco) presented the security implications of the Internet transition to IPv6. This is already the 3rd Eric’s presentation about IPv6 at RSA events. Every time, it was the same message: we will run out of IPv4 soon. But this time, it’s done also in Europe: “Every big ISP asking for extra IPv4 addresses will one receive 1024 IP addresses“, the message is clear. Two countries in Europe are good players: France and Romenia. Others are very late! Can we resume IPv6 in one slide? Sure, Eric did it:

Not only ISPs will have to change their infrastructure but also content providers. Using load-balancers / proxies they will be able to give access to legacy IPv4 servers (example: Facebook is working like this). Who’s choosing if a (dual-stack) server will be accessed via IPv6 or IPv4? That’s the PC/MAC/device. How? Two ways: Â Use IPv6 first (local policy) or the RFC6555 (“Happy Eyeball“). What are the impact for datacenters? As example, Eric gave the story of an Innocent server upgrade from W2K3 to W2K8: IPv6 used by default in 2K8! All OS have IPv6 stacks enabled, you have to harden it. Another example: the famous rogue RA’s. IDS must be upgraded to support IPv6 and people must be trained to understand IPv6. What are the impacts on applications? First issue: the IPv4 address reputation: what if 10000 customers use the same IP? (via Carrier-grade NAT). Same issue for rate-limit controls. Example: the Google sorry page. What about reputation of IPv6 addresses? Actually, this is still a chicken-egg problem: There is no reputation DB so nobody’s using filtering and no filters are in place to build the DB. Geolocalization is not easy (think about tunnel – mine ends in Amsterdam!) Let’s kill a myth: RFC6434 says “IPSEC SHOULD be supported by all IPv6 nodes“. IPsec will be used in the same way as IPv4. SSL will remain! Most vulnerabilities run at application layers, again nothing changes with IPv6. (ex: SQL injections). So good news: the mitigation techniques remains valid (if we consider them valid – that’s another debate :-). Logging? IPv6 addresses uses max 39 chars (compared to 15 for IPv4). In proxies, be sure to use “X-Forwarded-For” in HTML headers. What to do?
- Log the source port (RFC6302)
- Learn about IPv6! Increase the size of your fields to store IPv6 addresses
- Review critical apps regarding their behaviour with IPv6
- Think about pen tests. Their scope must include IPv6 addresses right now.
Last presentation for today and last minute planning change: “CSIRT, Cyber Extortion DDoS attacks & Forensics” by John Walker (Nottingham Trent University). The scheduled talk looked interesting (“The best defense is offence“). Anyway… Today, there are crimeware campaign. Attacks are announced and occur! Quote of McNealy, the CIO of Sun Microsystems, in 1999: “People have less privacy online than ever“.
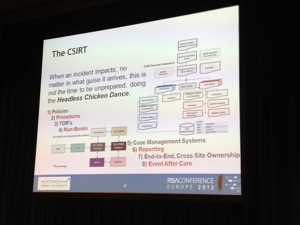
There are multiple examples of cyberwar/cyberconflict. For John, there are sometimes confusion of objectives. Example: PCI-DSS is good to drive compliance and security but sometimes, it causes a reduction of budgets & resources (the minimum is done to “be compliant”). This is a side-effect. We are facing a state of denial for years. Example: SPAM is not dangerous, Worms were not possible, Cellphone security is not an issue, Cyberwar is a product of the imagination etc… What are the required skills to compromise targets? Hackers: “it’s more a question of target insecurity being the point of leverage“. Printers, metadata are all ways to get access to interesting data. John demonstrated plenty of failures in information security. Exposed points of leverage: wmic:root\cli> or powershell. Why are those tools available to all users? Others? Dropbox, Tonido Plug, Sharepoint Desktop, Office 2010. Targets for extrusion are sport, gambling websites because they must remain online. If you pay, you be attacked again. Extorsion is a security issue, not only a financial one. We know that attacks will occur, so we need to have a first responder capabilities to react and engage with any incident. How? Policies, process, training, tools, information & communications. Some interesting tools mentioned by John:
- FRAT.BAT – First Responder Assessment Tool (running from an USB key)
- Process explorer is another good tools to start investigations.
- DNS Stuff to investigate remote site activity.
- A case management tools (self made or bought yourself)
That’s it for today! Now, let’s have some good time with friends!