 The primary goal of a log management solution is to receive events from multiple sources, to parse and to make them available for multiple purposes: searching, alerting and reporting. But why not send some interesting events to another log management system or application? Usually, some inputs are added in the log management environment like IP addresses blacklists, list of vulnerabilities, etc. But we can also generated some interesting outputs. By receiving data from multiple systems, it is possible to extract even more interesting stuffs. That’s what does dshield.org for years! Dshield is a service operated by the Internet Storm Center (ISC). Many volunteers from all around the world feed a huge database with events collected from systems like firewalls, routers, IDS etc. Based on this information, reports are generated and valuable content to be re-used in log management or SIEM environments; the loop is complete! 😉 Once you created an account, you can install a client which will collect your logs and send them at regular interval to dshield.org. Clients are available for the common types of firewalls.
The primary goal of a log management solution is to receive events from multiple sources, to parse and to make them available for multiple purposes: searching, alerting and reporting. But why not send some interesting events to another log management system or application? Usually, some inputs are added in the log management environment like IP addresses blacklists, list of vulnerabilities, etc. But we can also generated some interesting outputs. By receiving data from multiple systems, it is possible to extract even more interesting stuffs. That’s what does dshield.org for years! Dshield is a service operated by the Internet Storm Center (ISC). Many volunteers from all around the world feed a huge database with events collected from systems like firewalls, routers, IDS etc. Based on this information, reports are generated and valuable content to be re-used in log management or SIEM environments; the loop is complete! 😉 Once you created an account, you can install a client which will collect your logs and send them at regular interval to dshield.org. Clients are available for the common types of firewalls.
But what if you already collect your firewall logs via a log management tool (like OSSEC – just an example)? Why install a second client or agent? Once logs collected and centralized, why not send your logs directly from OSSEC? Dshield describes how to write your own client. The format is quite simple. So I write a small Perl script which works as described in the following schema:
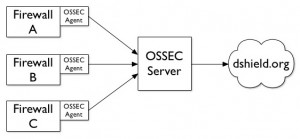
It read the OSSEC firewall.log file and generate events in Dshield format. The script syntax is simple:
$ ossec2dshield.pl --log=file --userid=dshieldid
--statefile=file --from=email
--mta=hostname [--help] [--debug]
[--test] [--obfusctate]
[--ports=port1,port2,...]
 Where:
--help                 : This help
--debug                : Display processing details to stdout
--test                 : Test only, do not mail the info to dshield.org
--obfuscate           : Obfuscate the destination address (10.x.x.x)
--ports=port1,!port2,... : Filter destination ports ex: !25,!80,445,53
 --log=file             : Your OSSEC firewall.log
--userid=dshieldid     : Your dshield.org UserID (see http://www.dshield.org)
--statefile=file       : File to write the state of log processing
--from=email           : Your e-mail address (From:)
--mta=hostname         : Your Mail Transfer Agent (to send mail to dshield.org)
Example:
 $ ./ossec2dshield.pl --log=/ossec/logs/firewall/firewall.log
--statefile=/ossec/logs/firewall/firewall.log.state
--userid=12345
 --from=user@domain.com
--mta=localhost
--ports="!80,!443"
You will need your dshield.org UserID, a mail relay (MTA). Very important, the state file will contain the timestamp of the last processed event. This prevents events to be sent twice to dshield.org. Once processed, the data will be submitted to register(at)dshield(dot)org. Using “–port“, you can exclude or restrict to some interesting ports. Example: “–port=’!80,!22,!443′” will report all blocked firewall traffic except for the destination ports 80, 22 and 443.
There are multiple advantages to use the OSSEC firewall log:
- You don’t need extra piece of software installed on the firewalls.
- You don’t need to send data to the Internet from the firewalls.
- You don’t need multiple clients, your logs are already processed and normalized by OSSEC.
The current script is not so powerful as the regular Dshield clients but it works. If you have ideas or suggestion, contact me. (Note: Your OSSEC must be properly configured to collect and store firewalls logs. Check out the OSSEC documentation for more details about this setup)
The script is available here in github.com. Feel free to re-use my code or to add features.
2 comments