 The job of security professional is definitively not an easy one! You have to be dedicated to your job and, once your business hours completed, there are all the remaining tasks which help us to keep your expertise level at the highest level. Hopefully, we do this with passion (otherwise, I pity you!)
The job of security professional is definitively not an easy one! You have to be dedicated to your job and, once your business hours completed, there are all the remaining tasks which help us to keep your expertise level at the highest level. Hopefully, we do this with passion (otherwise, I pity you!)
Attending security conferences is a must for everybody who wants to learn how new threats may hit users and systems. If you live in Europe, I recommend you the following ones in September: SOURCE Barcelona and BruCON. You can also follow webcasts, listen to podcasts. There are lot of places to learn! Once you grabbed interesting information, you come back to work fully motivated and try to implement the right counter-measures to protect your users from these new threats. After all, it is your job no?
Then, problems arise! As a good security professional, you will try to have the highest level of security in your infrastructure (ideal situation). Unfortunately, too much security controls may have a bad impact on your users, preventing them to perform they work in good conditions.
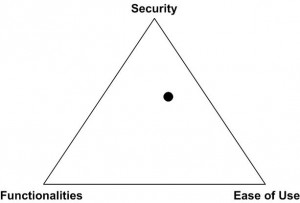
Keep in mind the security triangle (below). This triangle helps you to find the right balance between:
- Security
- Functionalities
- Ease of use
In an ideal situation, the black point must stay at the center of the triangle, this is the best balance. If you increase one of the components, the two others will be affected. If you increase the security (move the point nearby the top corner), you will increase the distance with functionalities and ease of use. Same for the ease of use. By adding nice features to your environment, you fill decrease the security.
Examples are multiple: You have mobile users requesting access to customers data. Good security practice is to authenticate users via strong authentication (the black point moves in direction of the security-corner) but you have to deploy a procedure to manage token-related issues (lost, broken, loss of sync) to not block the mobile users to access their data (ease of use). If you allow your users to update the data while on the move (a new functionality), you decrease the security and the ease of use. There are plenty of examples like this one.
That’s why your security policy can be compared to a recipe! You have to find the best balance between all the ingredients. Like cooking, there are basic rules that must be respected but then it is up to you to spice it as you like. As for the “compliance”, see this as “Controlled Designation of Origin” (or AOC in French). Compliance is performed via a consistent and traditional manner. Try to keep the security triangle in mind!
Hello,
I like this posting because it is pointing to something important: Security alone does not exist – Security always requires functionality, features and usage. (see http://www.computec.ch/projekte/tractatus/?s=tractatus)
But you could also add administration (cost/time for installation and operation) to the scheme for example. Thus, what about creating a rectangle 😉
Regards,
Marc