
Today, all organizations must take care of security. Not all of them have the same amount of data to protect nor the same level of confidentiality but they have to implement a security policy. If it’s rather easy to implement a security perimeter to protect against the Evil Internet, internal policies are much more complex to implement.
When you joined your organization, I’m sure you received at least the following stuff in your “packages”:
- at least one password (and be happy if you have only one) to log on the IT infrastructure to access applications and data, to read your emails and surf the Internet.
- a badge or code to physically access facilities (buildings, parkings, computer rooms, etc).
Using those security controls, Big Brother can track you: when you logged on the network, when and where you arrived or left the office. But such controls cannot prevent all the threats. There are remaining risks such as lost badges or shared credentials amongst users. How to deal with them?
Modern physical access control devices are based on IP. The readers have an IP address and the badges management is performed from a centralized console. Wait, if they use the IP network, for sure, it’s possible to collect data somewhere? Interesting data could be something like “badge X was used on reader Y at time T”.
Users access control is already centralized via AAA systems (“Authentication, Authorization and Accounting“). Behind AAA, we find the Active Directories, LDAP, Kerberos and lot of other systems used to track user activity on the network resources.
Let’s imagine the following schema:
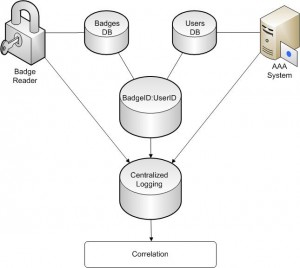
On the left side, we have a physical access control based, by example, on RFID badges. A database of badges is maintained (basically, who owns which badge and assigned access rights). All badges actions are logged in a centralized system. On the right side, a authentication system is deployed, by example, via a Microsoft Active Directory. Users are managed on the domain controllers and events are also sent to the same centralized system. If we can create a separate database which contains the “profile” of all users (their credentials linked their badge ID), we can greatly increase the value of events collected from the two systems. This is called the “Security Convergence”. The convergence of two distinct security controls. In this case, Information Security (the AAA system) and physical security (the badges and readers).
Example: John uses his badge to enter the building “A” of his company via the front door. A few minutes later, John’s credentials are used to log on a workstation located in the building “B”. Correlating those two events (of low priority) into a new one, we greatly increase the value of the correlated event and assign a higher priority to it: John’s badge was stolen or he shared his credentials with another employee. Another one: Two consecutive sessions are opened on terminals located in buildings separated by 100 Kms. Physically impossible!
Note that such controls not only apply in pure IT environments. They are widely used in other domains: Finance (a credit card cannot be used to get money from an ATM in Spain and Belgium within an interval of a few hours) or Telecommunications (same problem with a SIM card). Both can be cloned and used by bad guys. Another control from the Finance world? Buying the latest 40-inch flat-TV in the US with your Belgian credit card. This will generate a suspicious event. Will you really pay a huge amount of money to deliver goods to Belgium?
The security convergence can greatly increase your IAM (“Identity Access Management“) solution. Also, don’t forget that the tools deployed to perform security convergence are just only “tools”. It’s up to you to define what are your incidents!