
Back from the last ISSA Belgium Chapter event about targeted attacks. The speaker was Swa Frantzen. This is really a great guy who’s also a SANS ISC handler. Last year, he already made a presentation for ISSA about one day @ ISC. Less than twenty people attended the meeting today, a small audience but more open to discussion with the speaker, not bad at all!
Swa started with a attempt to define a targeted attack. This is an attack that “discriminate”: against a specific group of people who share the same interests, a company or an authority. One of the primary goals of such attack is to “fly under the radar”.
In the past, bad guys performed malicious activities for the fame or to cause mayhem. Today, gains take the first place. Attacks are performed to get money and tools are available for that! Crime is now well organized (think to the RBN – Russian Business Network). Interesting remark from Swa: the biggest botnets (> millions of infected computers) are totally unmanageable! (can you imagine a control-center to handle requests from millions of computer?).
The evolution of targeted attacks is visible on several aspects:
- Botnets are divided! Bad guys can rent a part of their botnets for specific purpose and another one for another type of attack at the same time.
- Even if defacements are less a hot topic (We don’t speak here about script kiddies who deface to promote their message), defacements hits more famous victims like major companies and major event websites.
- Malicious <iframe> are more difficult to track: search engines cannot index them anymore and specific tools cannot retrieve them (like wget). They behavior takes now care of the User-Agent.
- Spear phising is on the wild! This is a nice example of target attack. Send a mail with a fake resume to jobs@company.com. How many chances that the mail will be opened and the malicious PDF read?
Targeted attacks try to keep their targets small enough to not be detected and reported to anti-virus and/or IDP vendors. A good example given by Swa? WoW players are nice targets. Once passwords stolen, their ‘virtual’ money is transferred to other malicious players who convert it to ‘real’ money. And where do we find WoW players? On forums! All forums rely on database. A simple SQL injection will do the trick! Bingo!
Targeted attacks define a clear relationship between the target (the “audience”) and the value (the “expected gain”). Check the following graph:
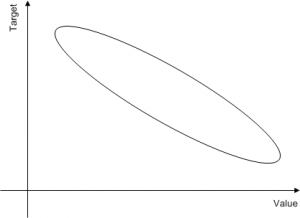 |
If the target is important, less value can be expected. On the other hand, a reduced target base will give much better results. The same effect can be represented by a pyramid:
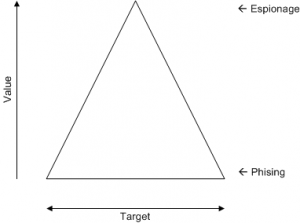 |
Do we have to be scared about targeted attacks? According to Swa, we must be scared about what targets us. Each company or group of people have its own centers of interest and can be the victim of different attacks. But, it’s a good practice to keep an eye of what appends and learn from other stories. We don’t have to worry about all attacks for follow them. A good balance is required.
What about the defenses? Swa reviewed all classic countermeasures available (firewalls, IDP/IPS, anti-virus, archtecture, …). The main idea is that signature based detection is not bullet proof! One of the best countermeasure to deploy is the anomaly detection. Example: your server generates 10GB of traffic per day. If suddenly it generates 50GB, you are facing in issue! Finally don’t forget the users: security awareness training! What’s the best way to find information about a company? Just ask! Visit forums, social network websites, invite people to a presentation and let them talk.
Swa’s presentation is already available online.